API
APIs (Application Programming Interfaces) are a set of rules and protocols that allow different software applications to communicate and interact with one another. As a result, it defines the methods, data formats, and conventions for exchanging data between applications.
How does it work?
An API enables software applications to make requests and receive responses from another application or service. API requests are sent by the requesting application, specifying the desired action or data. A request is processed by the API, the operation is performed, and a response is returned containing the requested data or the result of the operation.
Types of APIs:
APIs can be classified into several types, including:
- Web APIs:
Access to these APIs takes place over the internet using the HTTP/HTTPS protocol. Web services are commonly used by applications to interact with web-based systems.
- REST APIs:
A REST (Representational State Transfer) API follows specific architectural principles when it comes to building web services based on representational state transfer.
To access resources, they use standard HTTP methods (GET, POST, PUT, DELETE).
- SOAP APIs:
The Simple Object Access Protocol (SOAP) API uses XML-based messaging protocols to communicate. Interacting with them generally requires the use of a library or framework.
Methodology:
- Scope definition:
Clearly define the API penetration test scope, including the APIs to be tested, the testing objectives, and any limitations.
- Information gathering and reconnaissance:
Obtain information about the APIs, including the endpoints, methods, parameters, and authentication mechanisms.
Identify potential entry points and vulnerabilities by using tools such as Burp Suite, Postman, and manual inspection.
- Authentication and authorization testing:
The API authentication mechanisms, such as API keys, tokens, or OAuth, must be tested. It is important to check for vulnerabilities such as weak credentials, insecure token management, or a lack of proper authorization checks.
- Input validation and parameter manipulation:
Test the API for input validation vulnerabilities, such as SQL injection, XML injection, and command injection.
Bypass security controls or do unauthorized things with parameters.
- Error handling and exception management:
Test the API’s handling of errors and exceptions. Analyze the system for potential information leaks, erroneous error messages, or vulnerabilities that could lead to a denial of service or unauthorized access.
- Data security and confidentiality:
Analyze how the API handles sensitive data, such as encryption, storage, and transmission. Look for vulnerabilities such as insecure data storage, weak encryption, or the exposure of sensitive information in responses.
- Session management:
Test the API’s session management mechanisms, including session tokens, cookies, and session IDs. Consider vulnerabilities such as session fixation, session hijacking, and insufficient session expiration.
- API rate limiting and throttling:
Test how the API limits and throttles traffic to prevent abuse. Check for bypasses, excessive request limits, and incorrect configurations.
Tools:
- Burp Suite: Test and analyze APIs with Burp Suite, which includes features for intercepting and modifying requests, scanning for vulnerabilities, and analyzing responses.
- Postman: Postman is a powerful API testing and development tool that allows you to send requests, inspect responses, and automate testing workflows. Various authentication methods are supported, as well as extensive testing capabilities.
- OWASP ZAP: There is an open-source web application security testing tool called OWASP ZAP (Zed Attack Proxy) that can be used for API testing. A number of features are included, including active and passive scanning, fuzzing, and authentication testing.
- Nmap: Nmap is a network scanning tool that can be used to find APIs running on specific ports or systems and discover their locations. The tool can be used for reconnaissance and mapping of the API landscape.
- SQL Map: Injection vulnerabilities in APIs that interact with databases can be detected and exploited using SQLMap. The tool automates the process of identifying SQL injection points and obtaining data from them.
- Fiddler: A web debugging proxy that can intercept and inspect API requests and responses. You can modify requests, analyze traffic, and identify possible vulnerabilities using this tool.
Known Vulnerabilities:
BOLA
Broken Object Level Authorization (BOLA) vulnerability, often also referred to as Insecure Direct Object Reference (IDOR),
Access details of another user’s vehicle
Here is an endpoint u will get details of another user
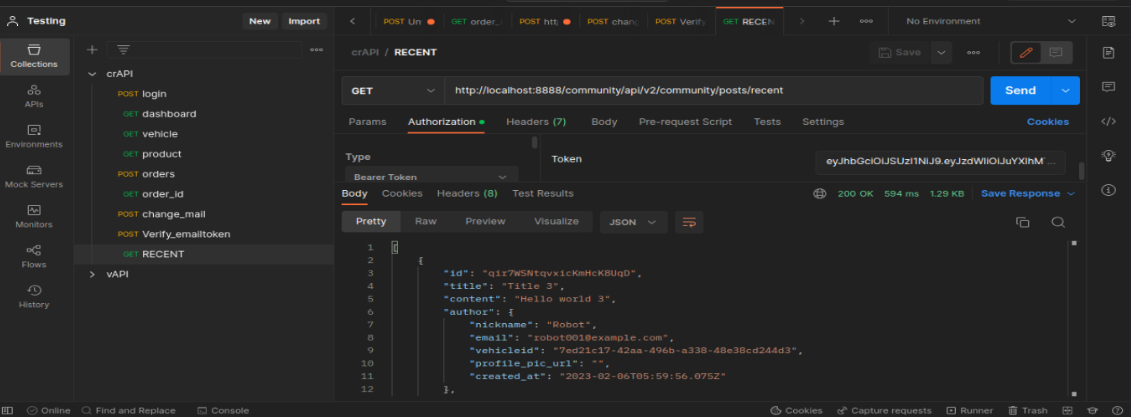
community/api/v2/community/post/recent here we see all details of other users that are provided by the user. By getting this information the attacker can misuse it.
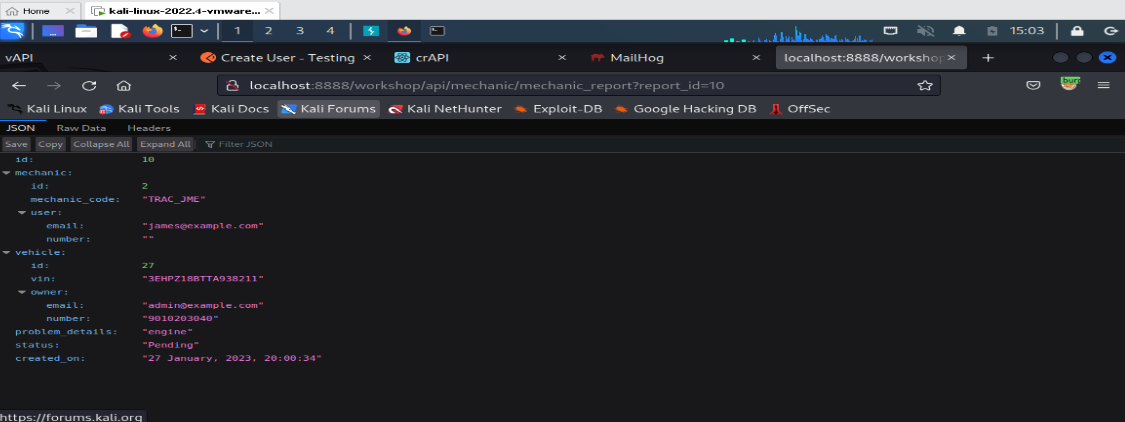
Access mechanic reports of other users
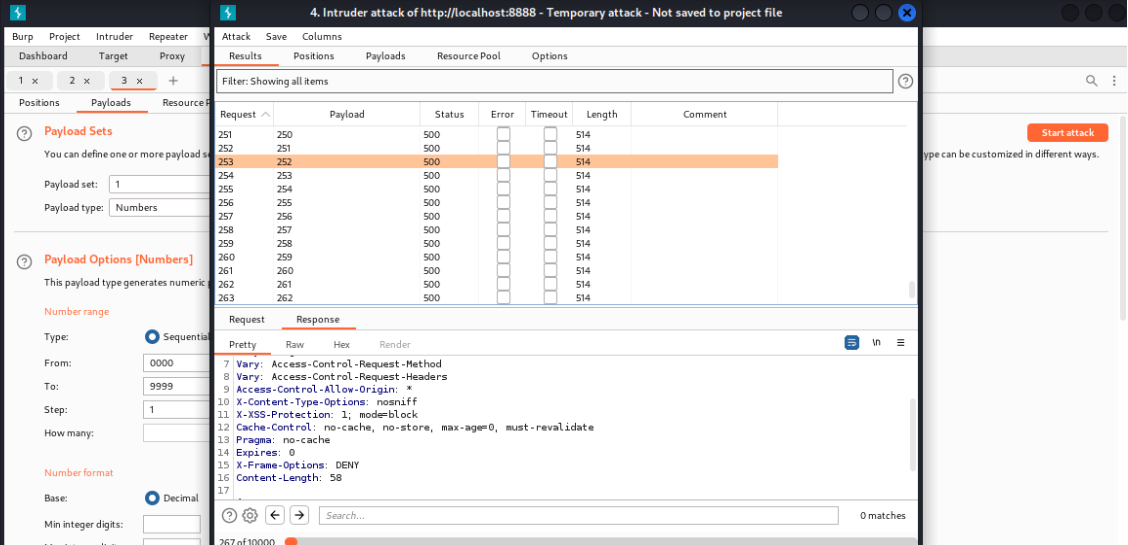
In this report_id endpoint we clearly see there is specific digit mean in every report there is report_id generated Here is a report id (report_id=5)
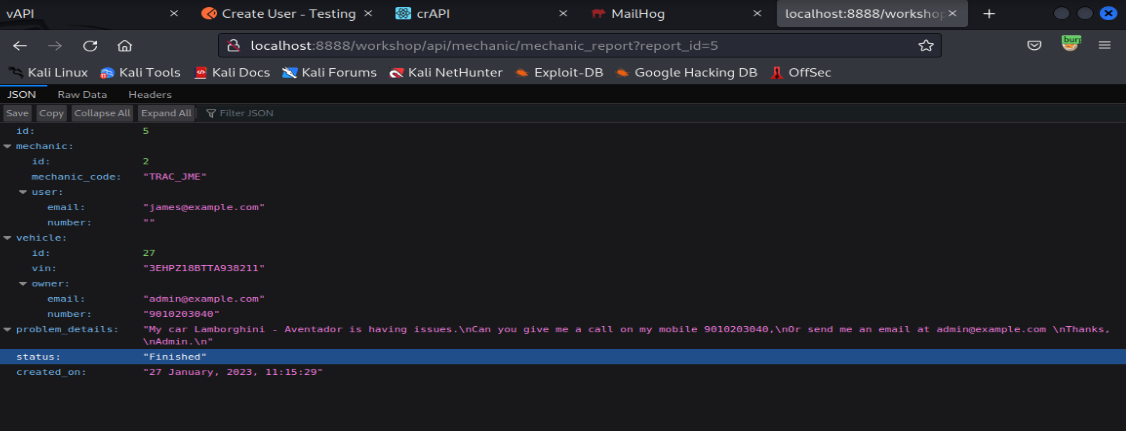
So, I changed the report_id to 10. it responds to the request; id is generated with the same user.
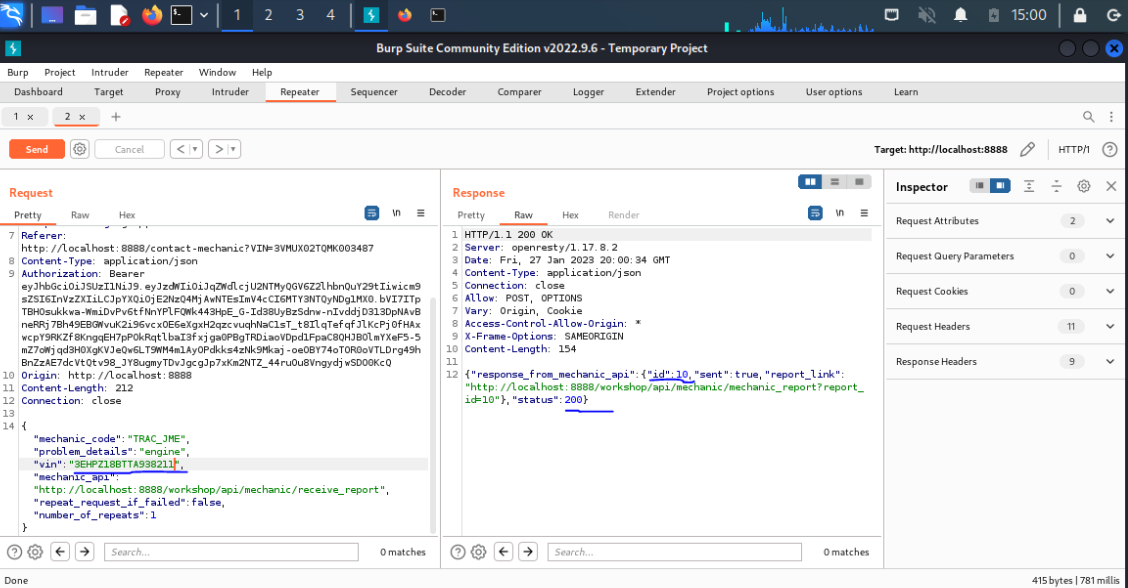
Intercept the request in burp and change the VIN no of other users .It returns with 200 status code.
Broken User Authentication:
Due to poor design and implementation of identity and access controls, the prevalence of broken authentication is widespread. Authentication is “broken” when attackers can compromise passwords, keys or session tokens, user account information, and other details to assume user identities
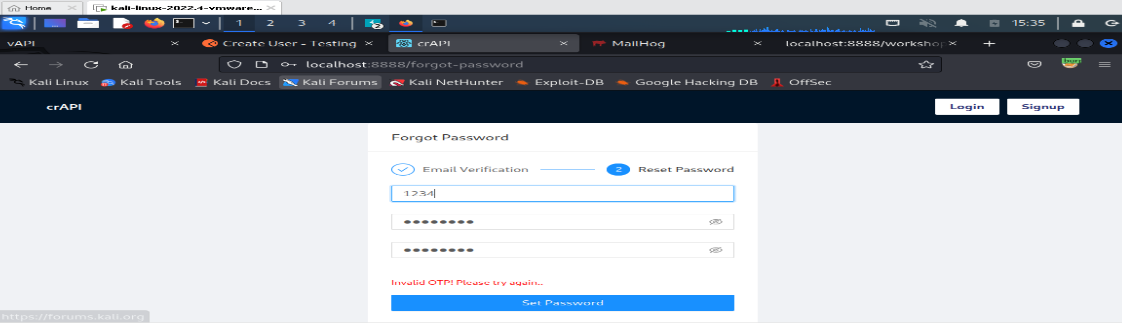
Reset the password of a different user:
Go to login page click forgot password, give others mail address capture the request in burp suite
Then do OTP brute force and set a password.
Here i perform OTP brute forcing
Rate limiting
Most of the time APIs are not configured to protect themselves from an excessive number of requests made from client-side. An attacker can use this flaw to overwhelm the server with too many requests to perform denial-of-service (DoS) or to bypass authentication mechanism
In this V2 version restriction is enabled (5 attempt is present)
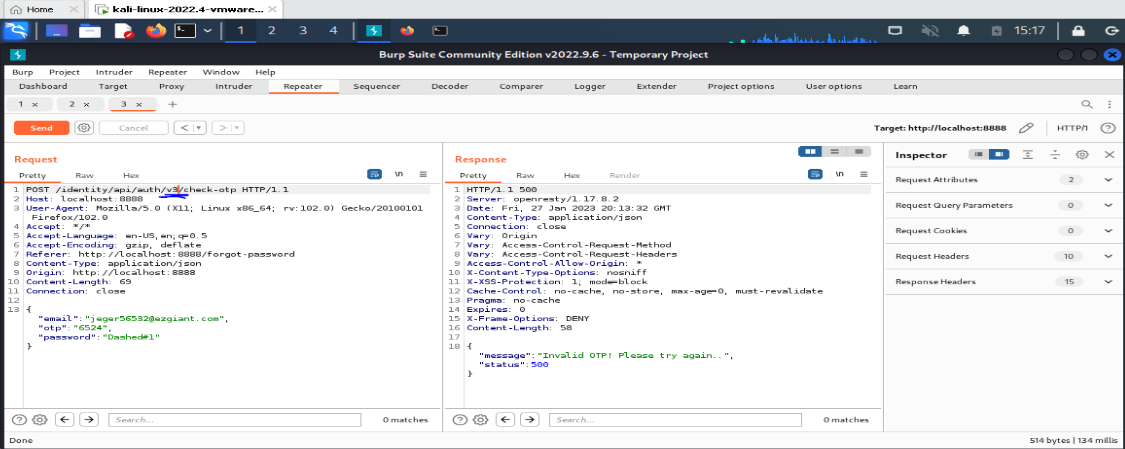
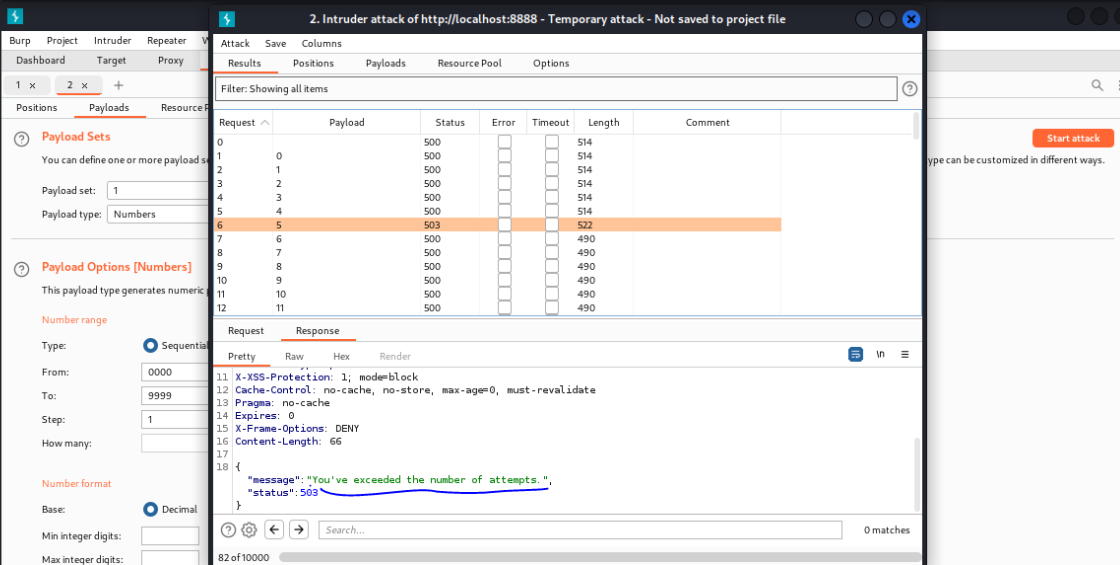 So, try with V1 version and there is no limit
So, try with V1 version and there is no limit
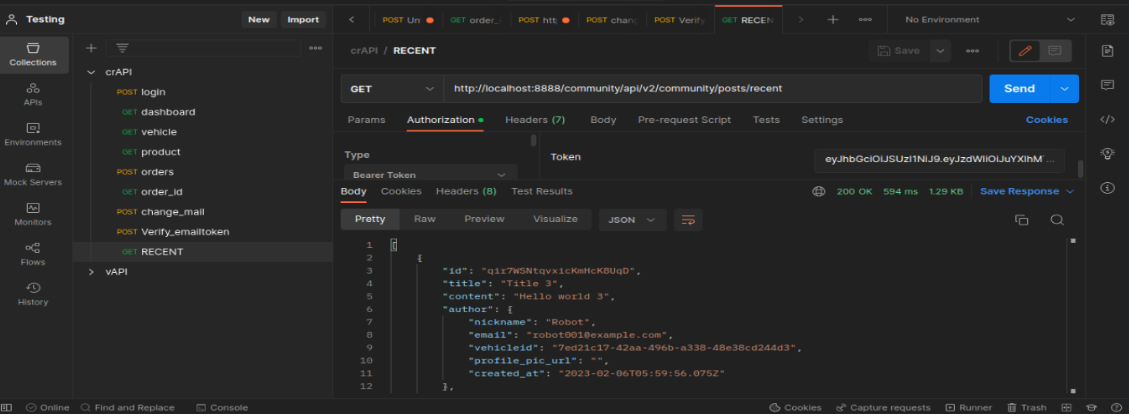
Excessive Data Exposure
APIs may return a lot of unnecessary data in response and filter it on the client-side to display only required data. An attacker can easily bypass client-side filtering by using proxy tools such as Postman and access the excessive data returned in the response.
In this GET endpoint we can access lot of information of other user community/api/v2/community/post/recent
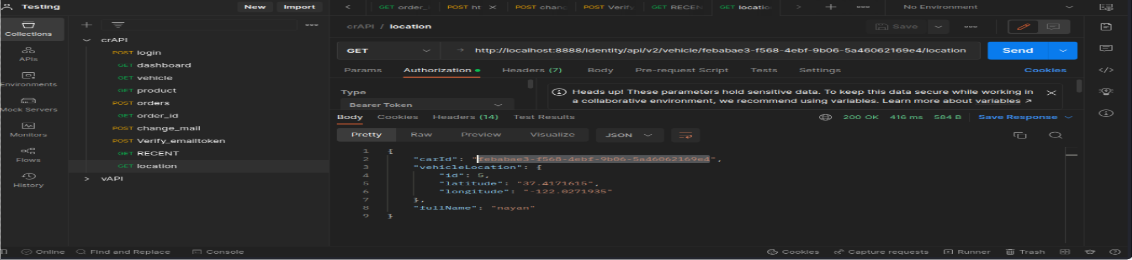
Go to the vehicle details you’ll see location click to refresh the location and capture this req in request there is car_ID and location info.
This my current location info with carID
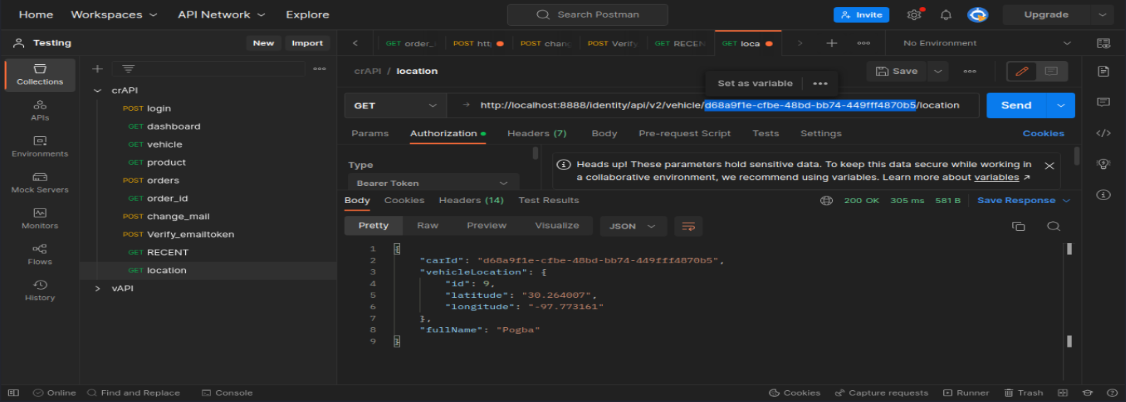
Replace car_ID value of other user in URL you can see that user’s location info
Mass Assignment:
Attackers can sometimes use this methodology to create new parameters that the developer never intended which in turn creates or overwrites new variables or objects in program code that was not intended.
Here I change GET req to POST because these endpoints allow me to change GET, POST, OPTION, PUT method. With the help of the POST method, I am able to create a new product.
Created a new product wroth of -$1000
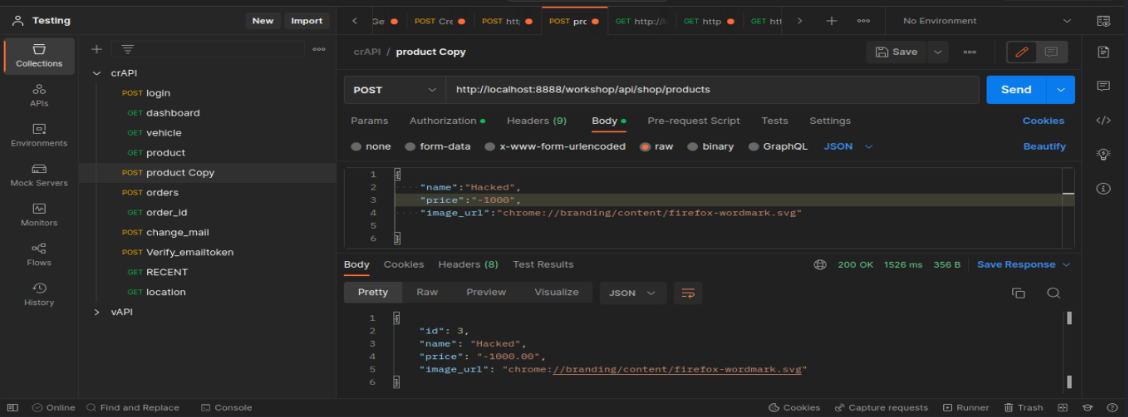
Here we can see our created product is visible in web application name is (Hacked) worth of -$1000 and let’s check if it works or not.
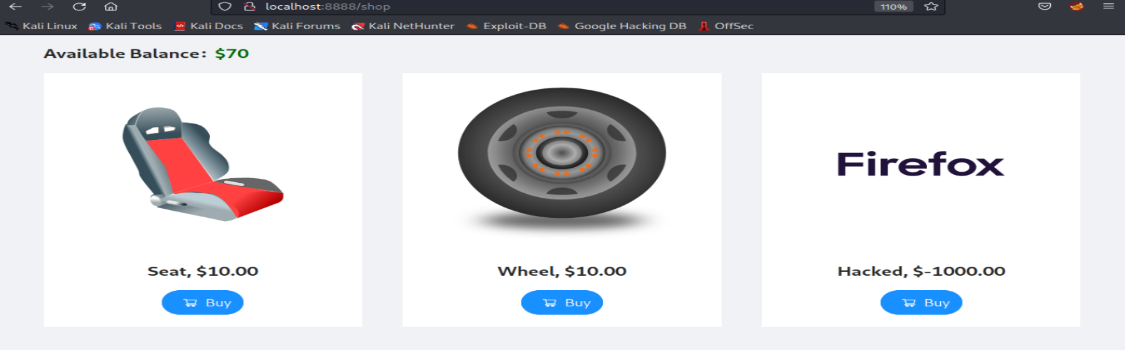
Previously available balance was $70 after purchasing a new product worth $-1000.Balance increased to $1070.
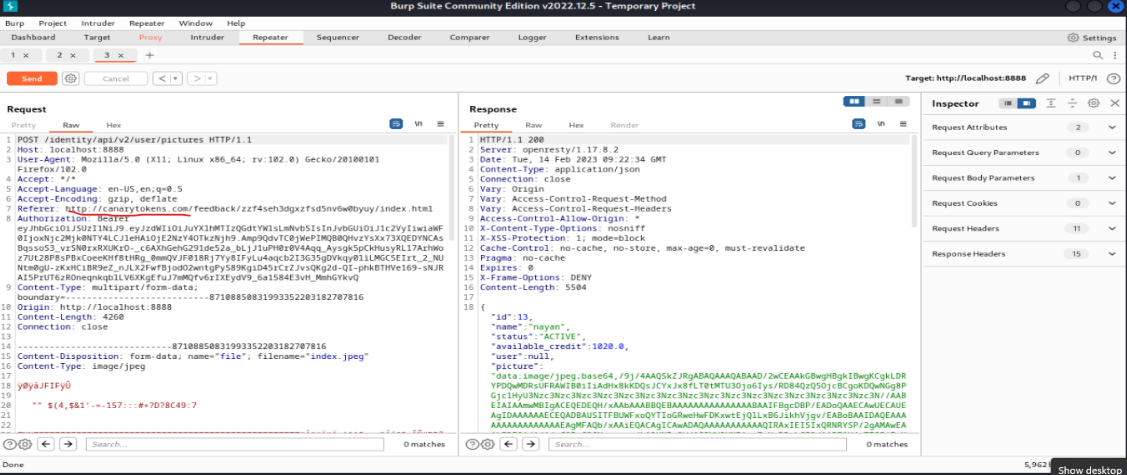
SSRF
Server-side request forgery (also known as SSRF) is a web security vulnerability that allows an attacker to induce the server-side application to make requests to an unintended location.
In this image I used a canary token to send http request as well as return with http response.
Successfully getting a response.
SQL Injection
SQL injection is a code injection technique through which we grab the data and manipulate also.
Inject some SQL query to get coupon code so first go near to end point “product” and click on add coupon
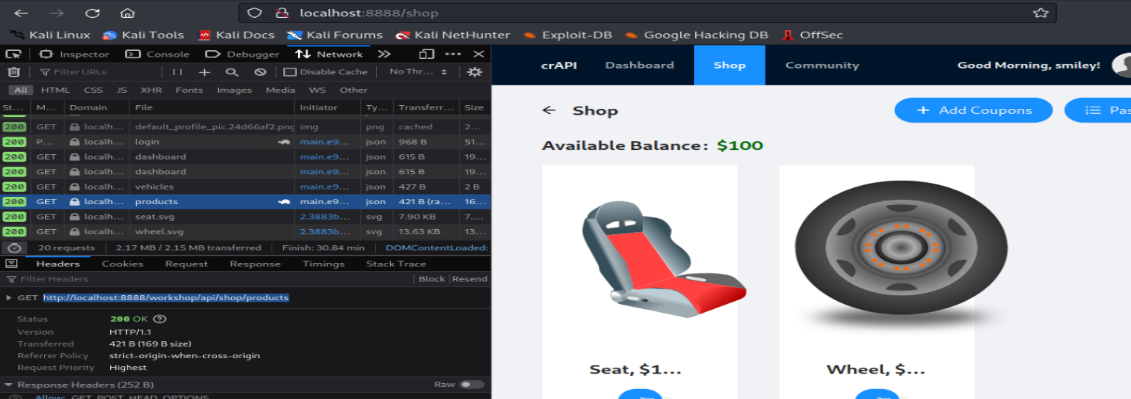
Randomly add some text and intercept the request in burp for later analysis
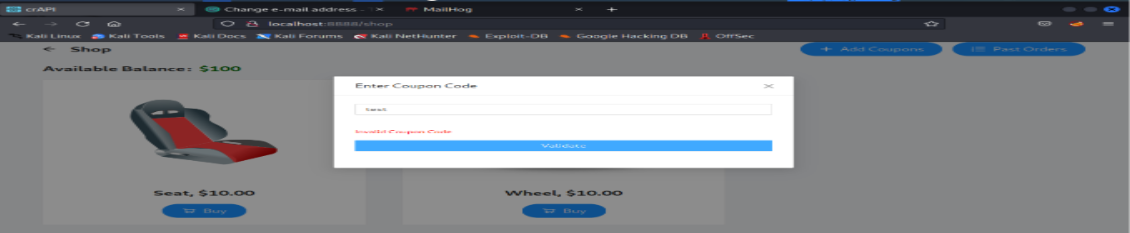
Response shows that GET, HEAD, OPTIONS methods are allowed to change. So, I changed to OPTIONS. It responded with 200 status codes.
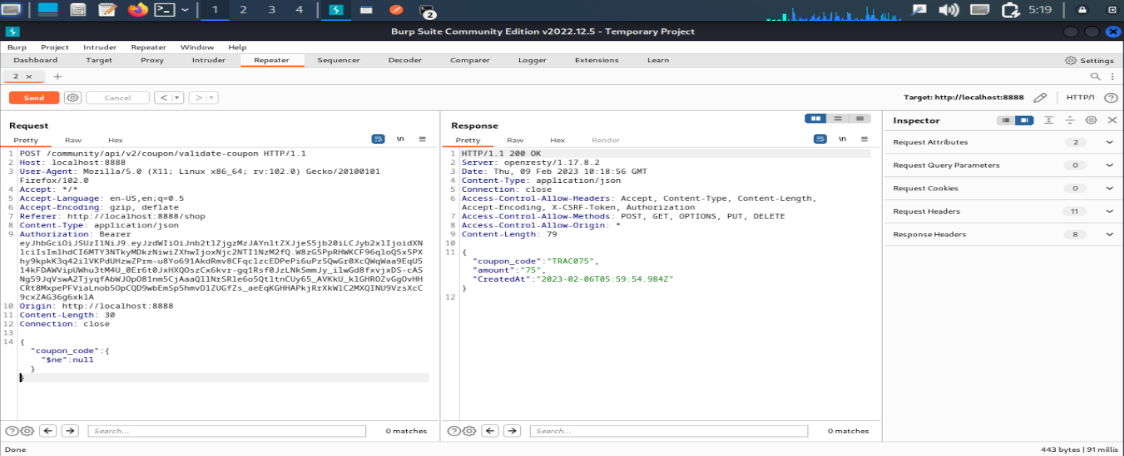
Here I add NoSQL injection $ne: mean not equal ($ne: null) for extracting coupon code
Yes, we get coupon code TRAC075 by inject SQL query.