Reconnaissance
Reconnaissance, often abbreviated as “recon,” is the process of gathering information or intelligence about a target, such as a person, organization, or system, to gain a better understanding of its characteristics, vulnerabilities, and potential threats.
Reconnaissance can be categorized into two broad types: active reconnaissance and passive reconnaissance.
Active Reconnaissance
Active reconnaissance involves engaging with the target directly, often by probing or interacting with the target system or network. This type of reconnaissance typically generates network traffic or produces visible actions, which may alert the target of the probing activities. Some common techniques used in active reconnaissance include:
- Port Scanning: Scanning a target system or network for open and filtered ports, which can provide information about running services and potential vulnerabilities.
- Vulnerability Scanning: Identifying known vulnerabilities in the target system or network.
- Network Enumeration: It includes gathering information about the target network, such as IP addresses, network topology, and network services.
Various Tools Used in Active Reconnaissance:
Ping: Ping is a basic network utility used to check the reachability and responsiveness of a target system or network device.
Telnet: It can be used to test if specific ports on the target system are open and accessible by attempting to establish a telnet session.
Traceroute: Traceroute is a network diagnostic tool that maps the path taken by network packets from the source to the destination. It displays the sequence of routers or hops traversed.
Nmap: Nmap is a network scanning tool, that can perform various active reconnaissance tasks, including port scanning, version detection, operating system fingerprinting, and vulnerability scanning.
Nessus: Nessus is the most commonly used vulnerability scanning tool. It actively scans network systems to identify known vulnerabilities and misconfigurations. It provides detailed reports and recommendations to enhance system security.
OpenVAS: OpenVAS is also a vulnerability scanner and open-source tool. It performs comprehensive vulnerability assessments, similar to Nessus, by scanning networks, systems, and applications for known vulnerabilities.
Nikto: Nikto is a web server vulnerability scanner. It scans web servers and applications, identifying potential security issues, misconfigurations, and outdated software versions. Nikto focuses on detecting common web server vulnerabilities.
Metasploit: Metasploit is a powerful framework for penetration testing and exploiting vulnerabilities. It provides a wide range of tools, exploits, and payloads for active reconnaissance, penetration testing, and security research.
Passive Reconnaissance
Passive reconnaissance involves gathering information without directly interacting with the target system or network. It gathers intelligence without raising suspicion or leaving any noticeable traces. Some common techniques used in passive reconnaissance include:
- Open-Source Intelligence (OSINT): Collecting publicly available information from sources like websites, social media platforms, online forums, and public records to gather information about the target.
- Network Traffic Analysis: Monitoring and analyzing network traffic passively.
- Information Gathering: Gathering data from public sources, such as domain registrations, DNS records, or WHOIS databases to get information related to the target’s infrastructure.
Various Tools Used in Passive Reconnaissance
- WHOIS queries are performed using the WHOIS protocol and servers, providing access to publicly available information about domain registrations, including ownership details, registration dates, and contact information.
- Nslookup and Dig are tools used to query DNS (Domain Name System) servers, enabling the retrieval of DNS database records, such as IP addresses associated with domain names, MX (Mail Exchange) records, and other DNS-related data.
WHOIS records and DNS database records are valuable sources of information for reconnaissance, as they offer insights into a target’s domain registrations, IP addresses, and DNS configurations.
- DNSDumpster is an online service that offers various DNS-related functionalities, allowing users to gather intelligence about a target’s DNS infrastructure. It provides DNS record lookups, IP-to-domain mappings, and subdomain discovery, aiding in reconnaissance activities.
- Shodan.io is a powerful search engine focused on internet-connected devices. It facilitates reconnaissance by enabling users to search for specific devices, services, or open ports. Shodan.io can uncover devices with vulnerabilities, exposed services, or misconfigurations, providing valuable information about a target’s internet-facing infrastructure.
- VirusTotal is an online service that can be utilized as a passive reconnaissance tool. It provides the capability to scan files and URLs using multiple antivirus engines and various other security tools. By submitting a file or URL to VirusTotal, you can obtain information about its reputation and detect potential malware or malicious activity.
RecOne Tool
This tool offers an automated solution for tasks such as subdomain discovery, port scanning, banner grabbing, and overall reconnaissance process optimization. Researchers can effortlessly gather subdomains linked to their target, verify open ports within the target’s network, extract banners from services running on those ports, and efficiently accumulate crucial information from JavaScript files and other interesting file providing login panels, sensitive information and error pages.
- Subdomain Enumeration: The script automates the process of discovering subdomains associated with a target. This can be helpful in identifying potential entry points or overlooked areas of the target’s infrastructure.
- Port Scanning: By scanning the target’s network for open ports, the tool enables researchers to identify running services and potential access points. Port scanning helps in assessing the target’s attack surface and understanding its network architecture.
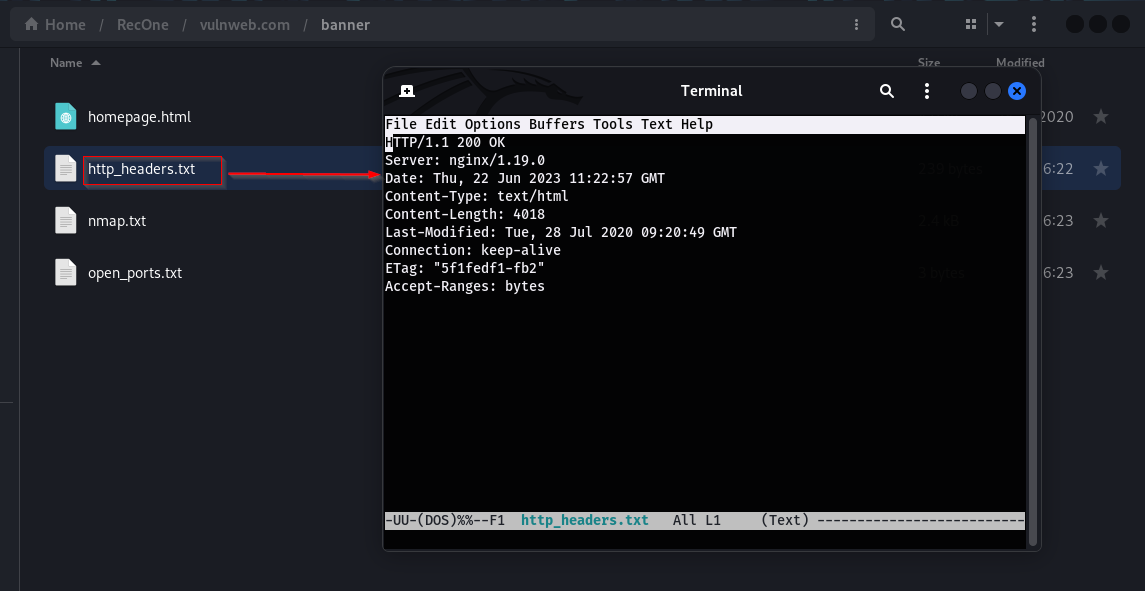
- Banner Grabbing: The tool performs banner grabbing, which involves extracting information from the banners or headers sent by services running on open ports. This can provide insights into the software versions, protocols, or configurations used by those services.
- Reconnaissance Automation: The tool brings automation to the reconnaissance process, reducing manual effort and automating the collection of valuable information. The script employs crawling and link extraction techniques, utilizing tools like hakrawler, linkfinder, and gau, to operate on the provided domain.
It collects and filters the results to identify specific elements of interest, including login panels, sensitive files, third-party assets, email addresses, usernames, sensitive paths, the contents of the robots.txt file, and subdomains associated with the target domain.
Overall, tool script enhances the efficiency and effectiveness of security researchers by automating key steps in the reconnaissance phase. It allows them to focus on analyzing the gathered information, identifying potential vulnerabilities, and making informed decisions to enhance the target’s security posture.
Installation
To install and run the tool, clone the GitHub repository to your local machine.
Command: git clone https://github.com/mbappzlogic/RecOne.git
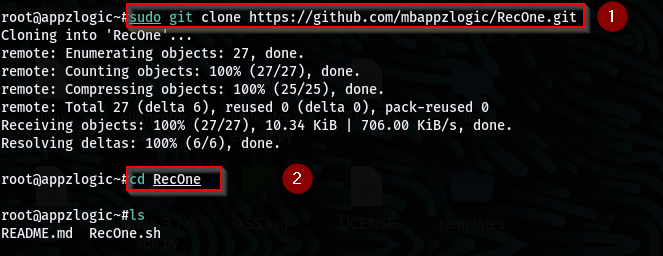
After installing the tool move to the RecOne directory and make the script executable.
Command: chmod +x RecOne.sh
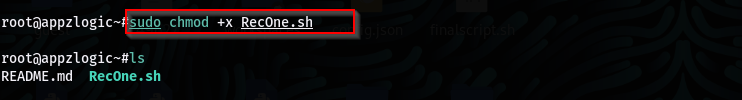
Usage:
To use the script, run the following command:
Command: sudo ./RecOne.sh
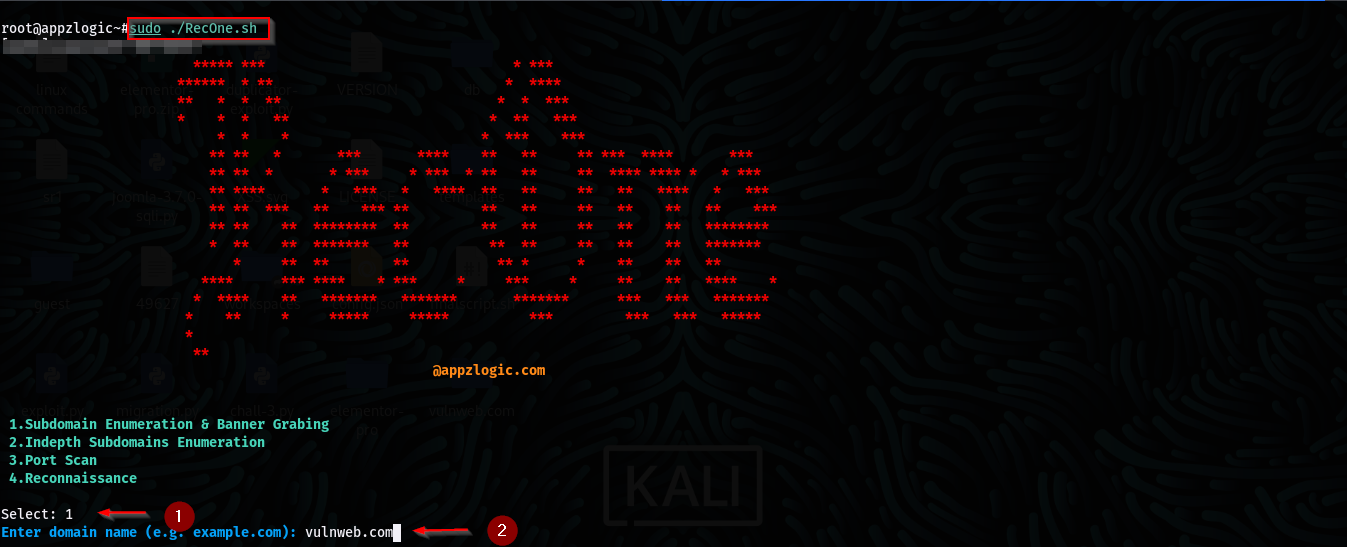
Once executed, the script will present you with a menu of tasks to choose from, including options such as subdomain enumeration, port scanning, or reconnaissance. Upon selecting the desired task, you will be prompted to enter the target domain name. Once you provide this information, the script will take over and automate the specified task, streamlining the entire process for you.
- Subdomain Enumeration & Banner Grabbing
To find subdomains of a domain and perform banner grabbing, select first module and provide the target domain when prompted.
Results: The results of the subdomain enumeration and banner grabbing are stored under target directory.
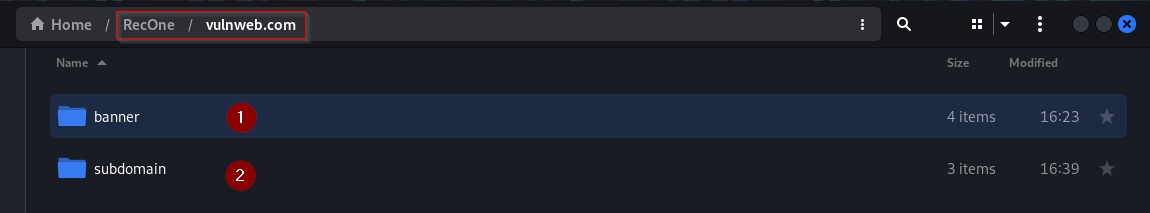
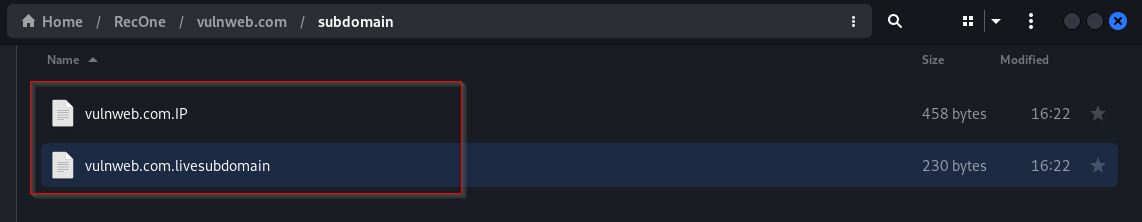
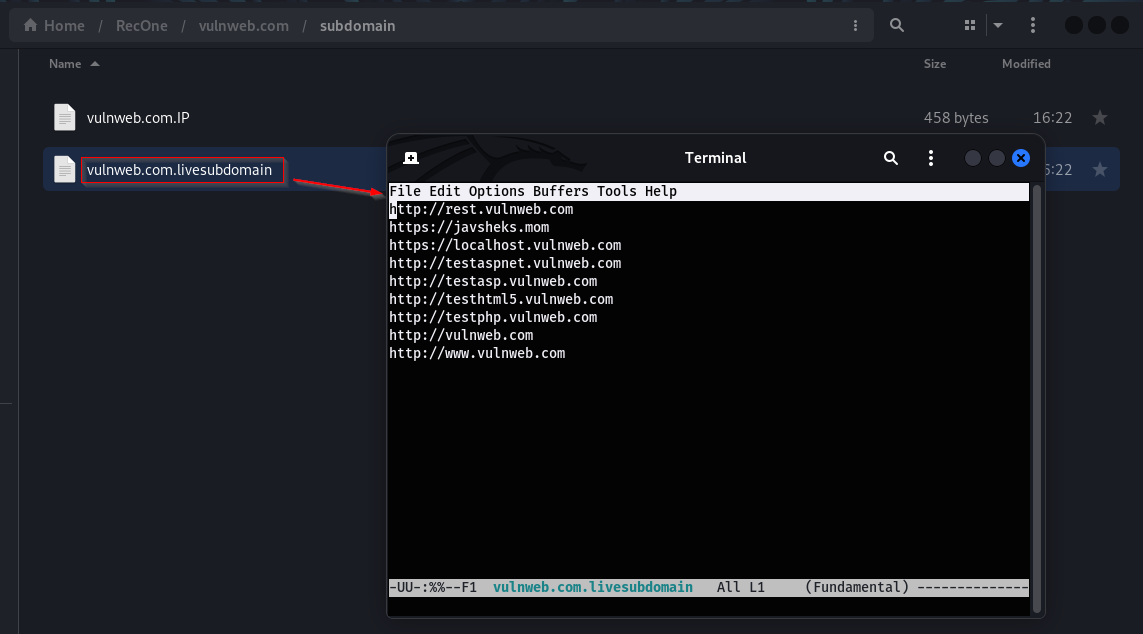
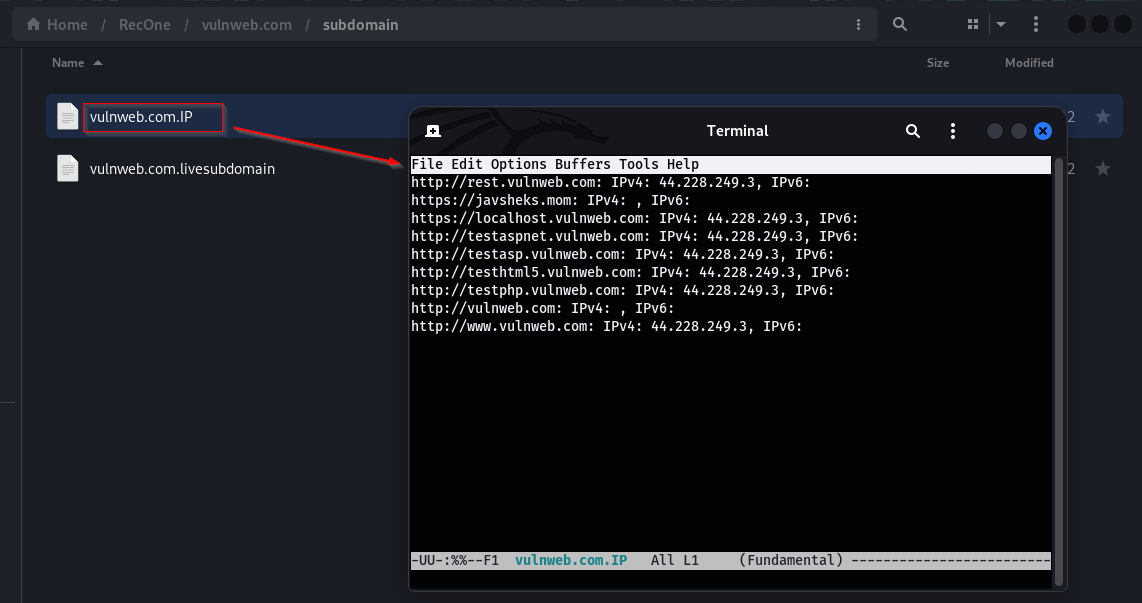
Results of subdomain enumeration are stored under subdomain directory. It contains two files, domain.livesubdomain contains all the alive subdomains found and domain.IP file that contains the IP address associated with subdomains found.
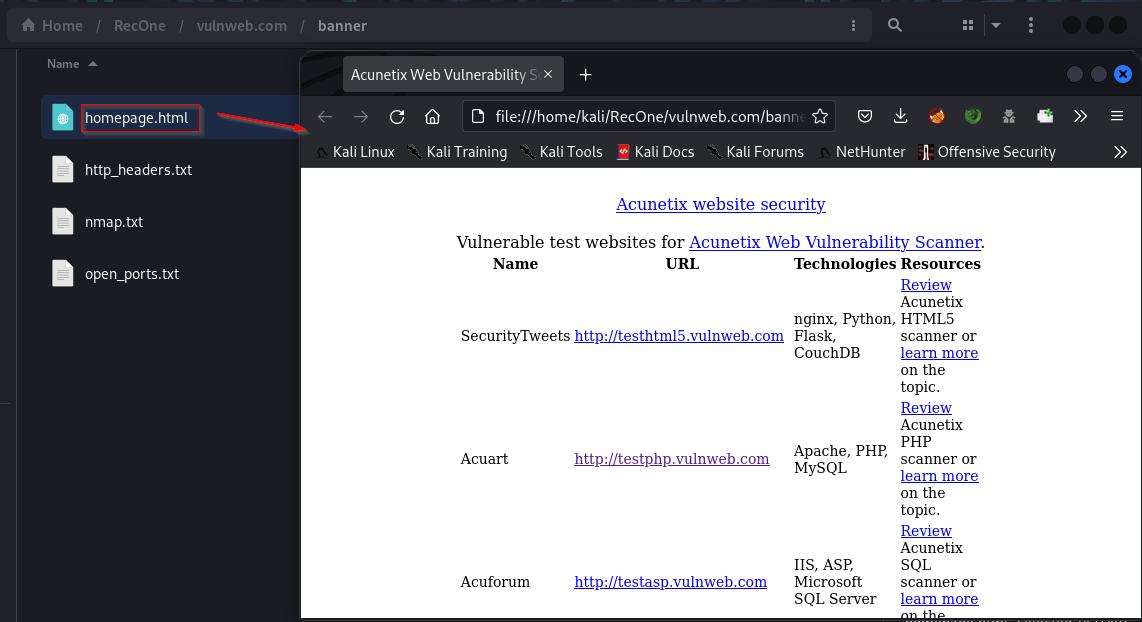
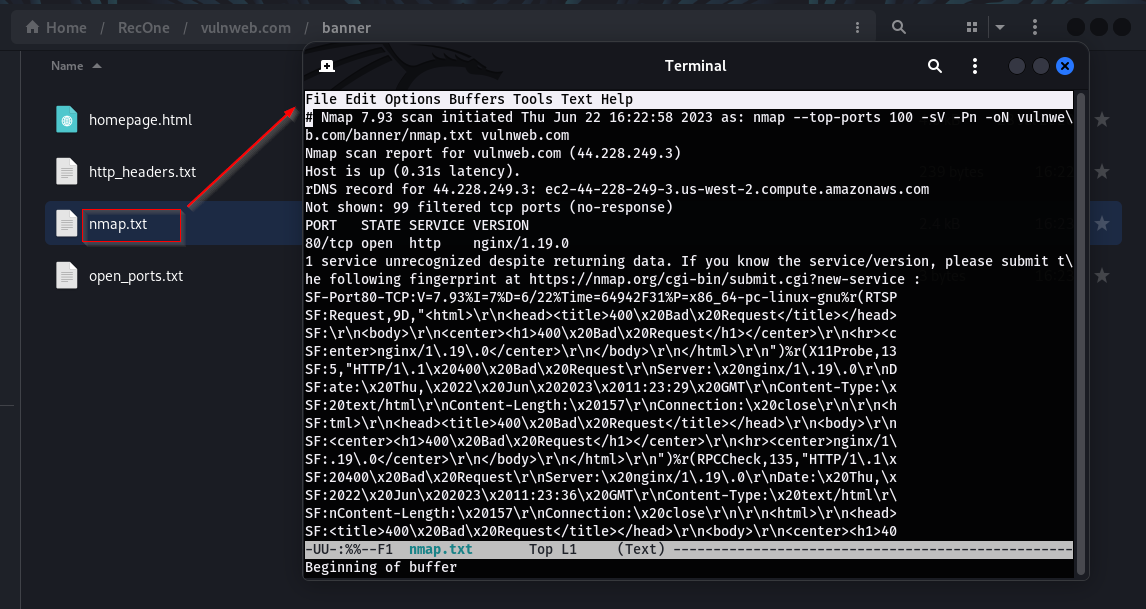
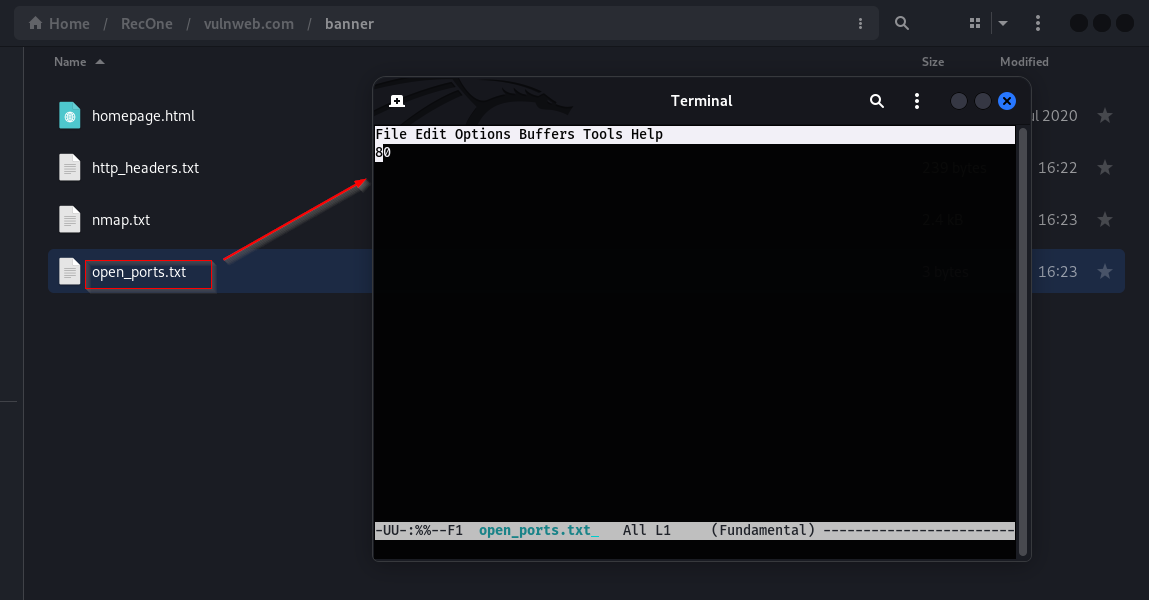
/banner directory contains banner grabbing information fetched by the tool. It contains the homepage of the target, Headers returned, scan results of the top ports and list of open ports.
- Indepth Subdomains Enumeration
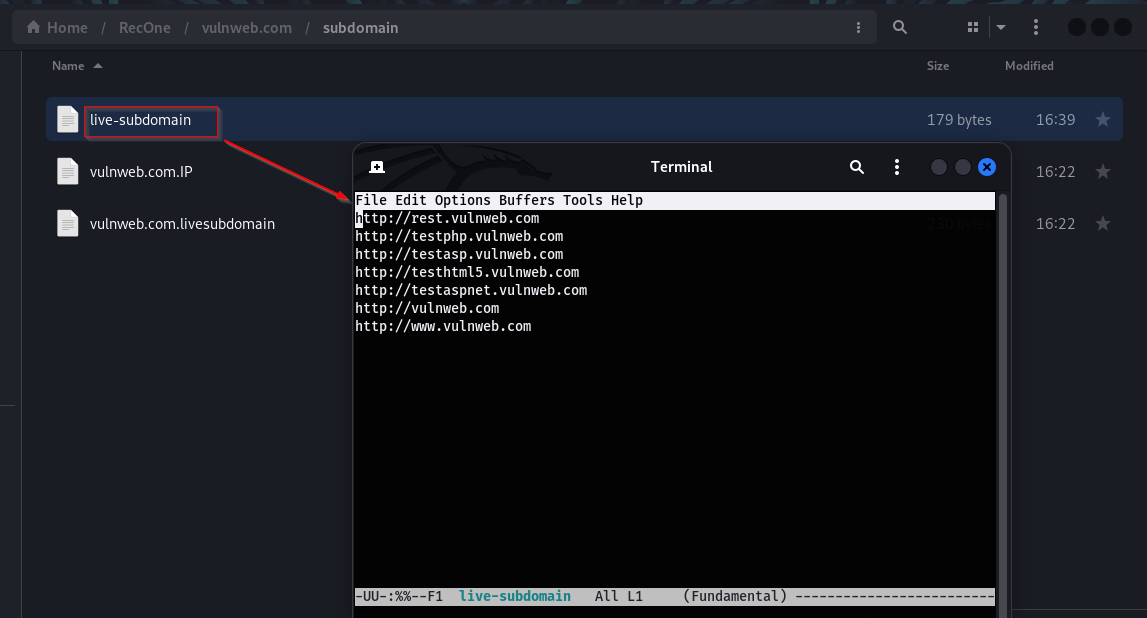
The in-depth subdomain enumeration process involves using various tools to find subdomains, along with brute-forcing techniques. The script then filters the results to provide a final list of active subdomains or live hosts.

Result: The results of In-depth subdomain enumeration can be found under the /subdomain directory. The file contains all the live subdomains found.
- Port Scan
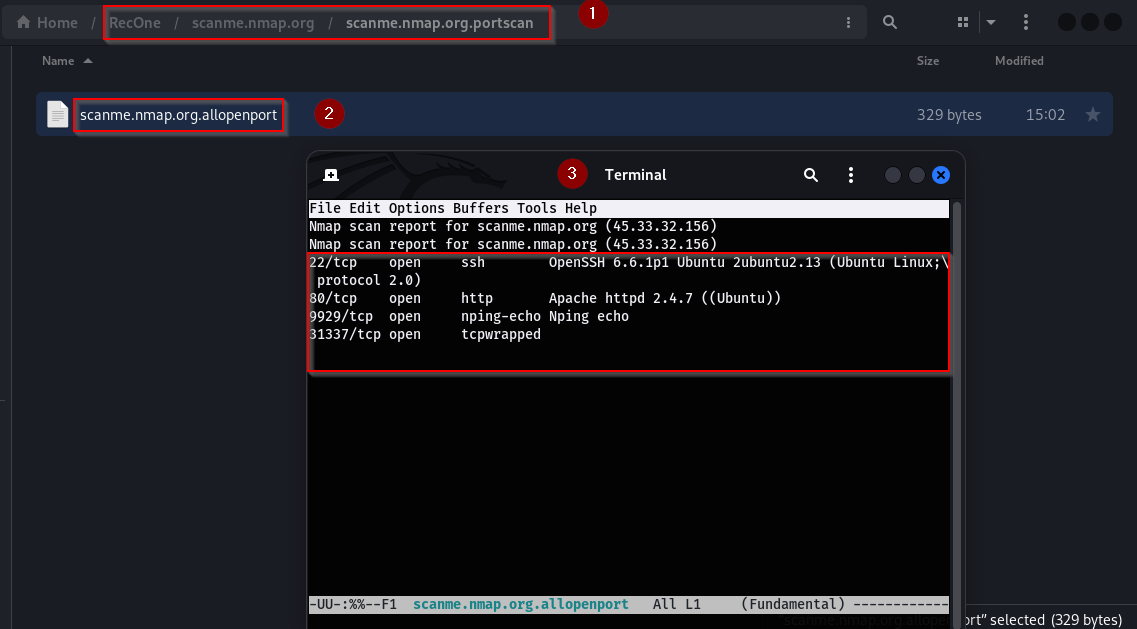
To enhance the accuracy and effectiveness of port scanning, the script utilizes advanced scanning tools such as nmap, masscan, and rustscan. These tools are employed to conduct a thorough port scan, resulting in improved scanning results.

Result: The results of the scan are stored in the directory named after the provided domain name. The result includes all the open ports for the targeted domain and the details of the services running upon those ports.
- Reconnaissance
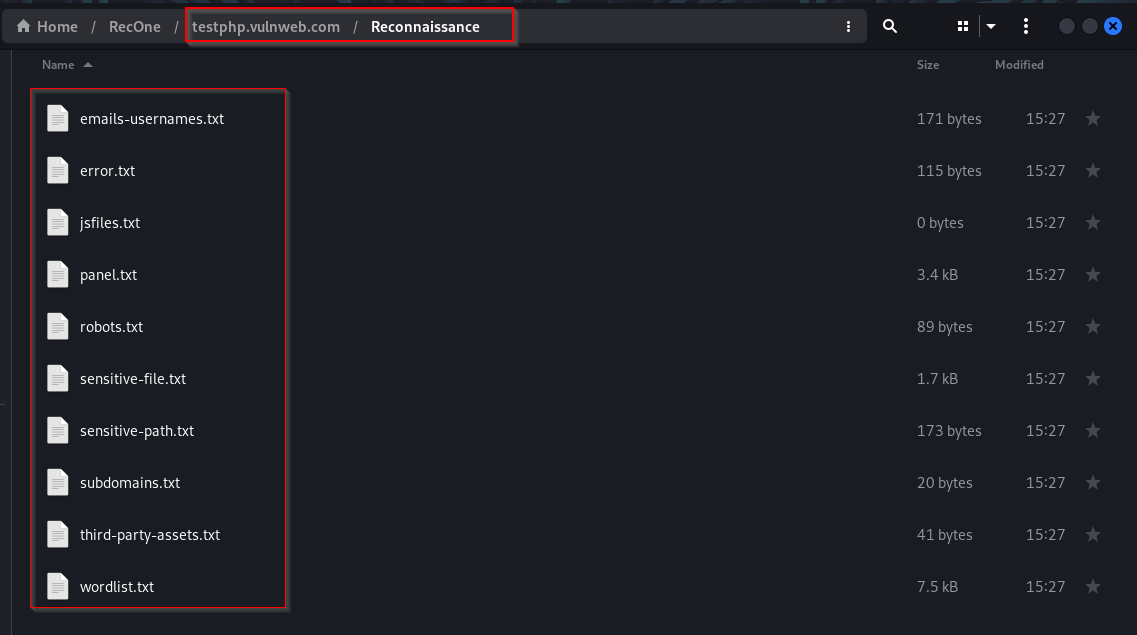
This module utilizes crawling and link extraction methods, using tools such as hakrawler, linkfinder, gau, and gauplus, to process the specified domain. It gathers and filters the obtained data to pinpoint relevant components such as login panels, sensitive files, third-party assets, email addresses, usernames, sensitive paths, the contents of the robots.txt file, and subdomains associated with the target domain.

Results: The results are stored in reconnaissance directory under the directory with target domain name.
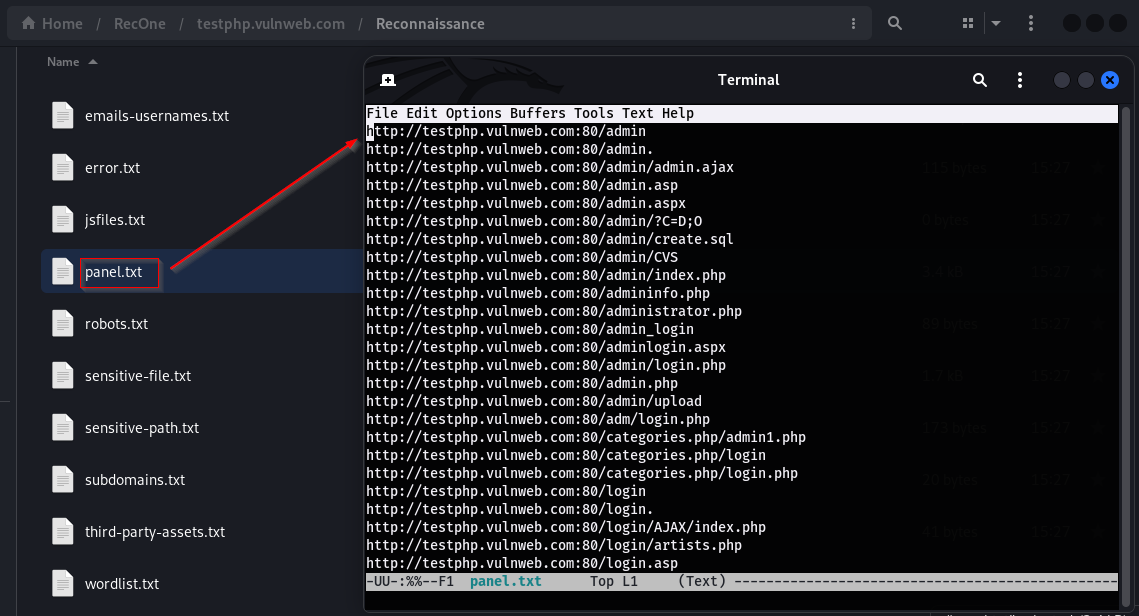
Panel.txt: It contains all the panel-relevant information found from crawling and extraction for the targeted domain.
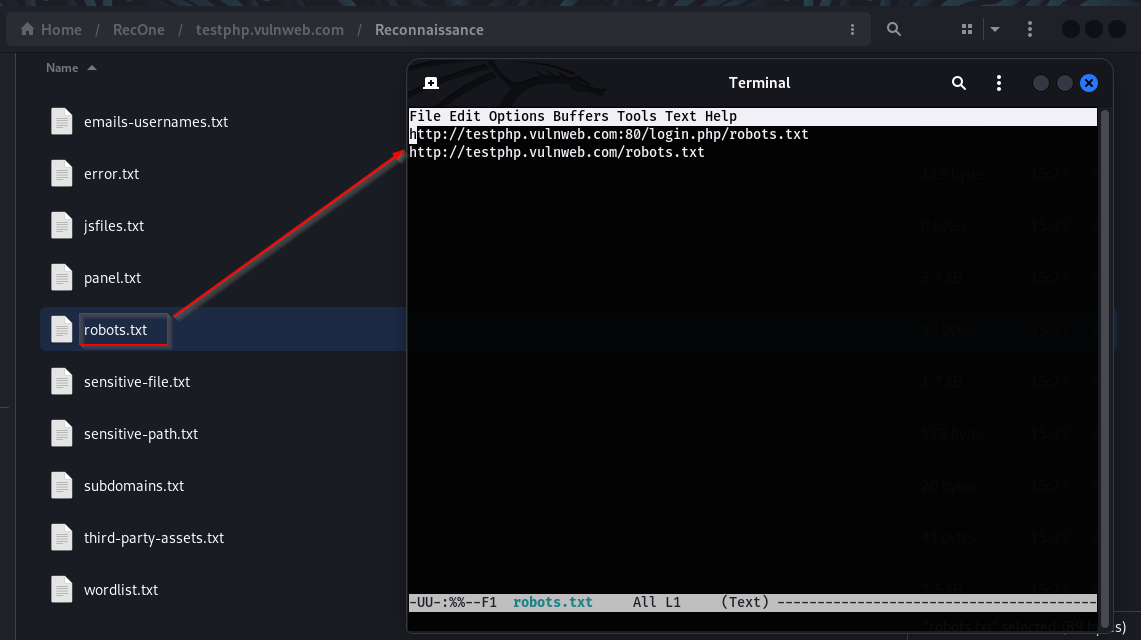
Robots.txt: It contains all the instances of robots.txt for the targeted domain.
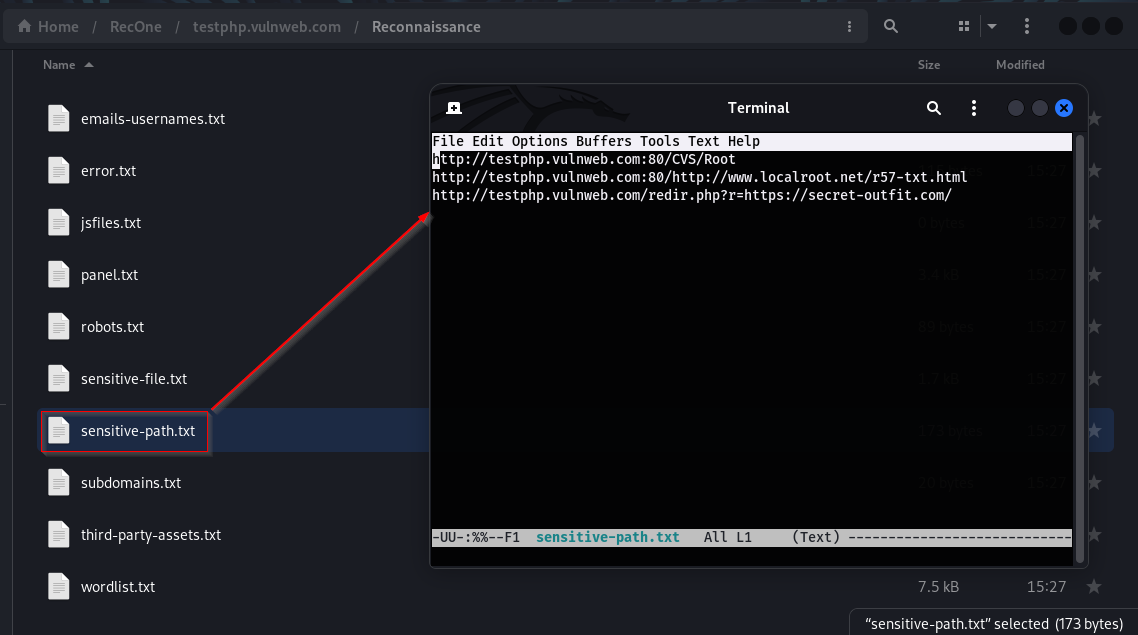
Sensitive-file/Sensitive-path: This file contains all the sensitive files or paths found from crawling.
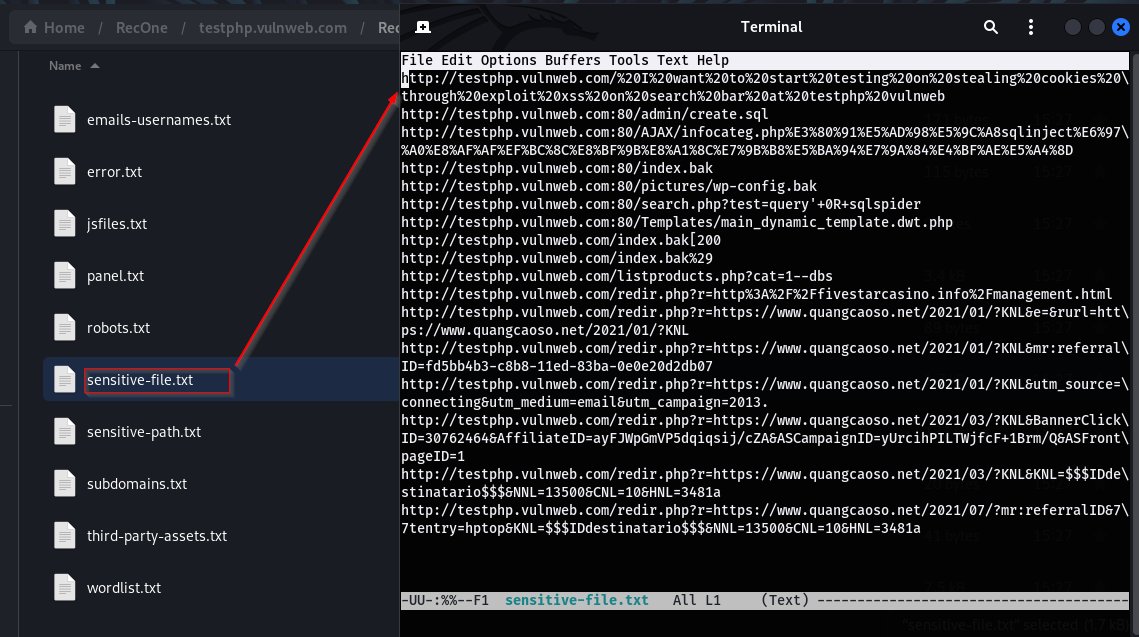
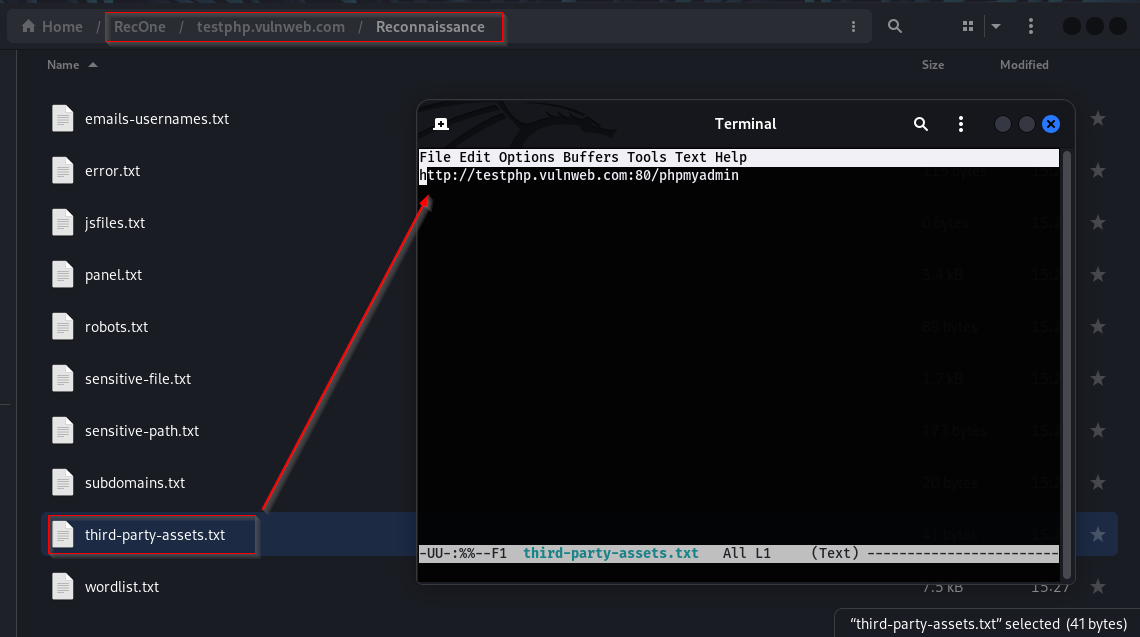
Third-party assets: It contains data relevant to third-party assets. Third-party assets are external components or resources integrated into a target system or website that are developed and maintained by third-party entities. Examples include software applications like Jira, which aids in project management and issue tracking, and phpMyAdmin, a web-based tool for managing MySQL databases.
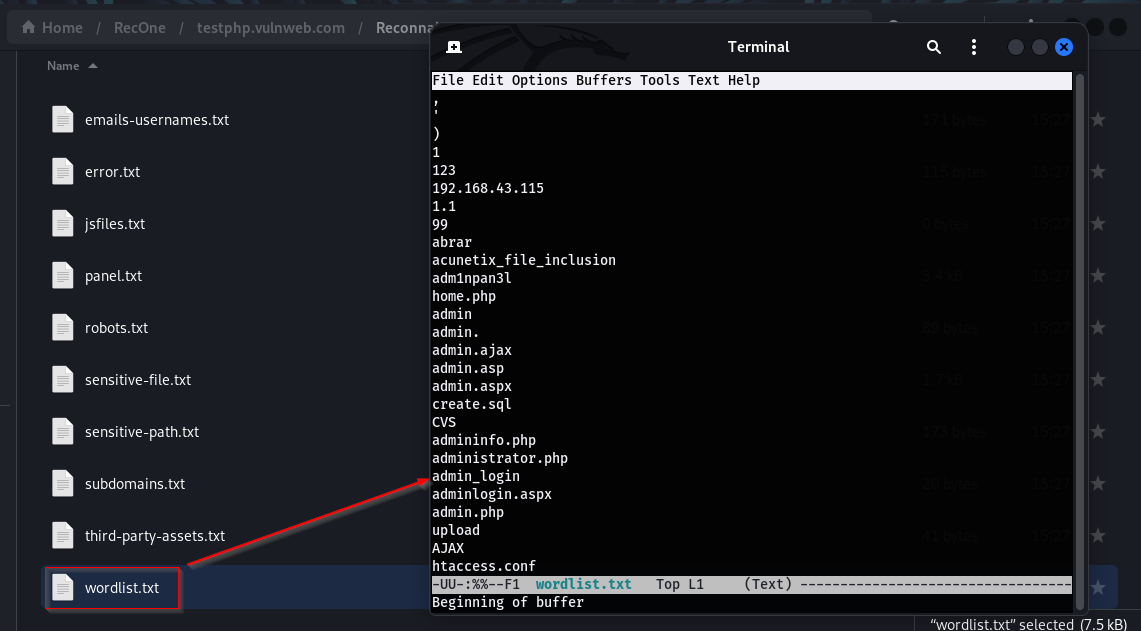
Furthermore, the tool can create a word list that can be used to explore the targeted domain more extensively. This wordlist assists in fuzzing, a technique that involves testing different combinations of words or characters to discover hidden areas, directories, or files on the target domain.
In this blog, we explored the concepts of Active Reconnaissance and Passive Reconnaissance. Along with the different tools used in each approach to gather information about target systems or networks.
Furthermore, the blog provided insights into the RecOne Tool, which is a versatile tool. It covered the tool’s introduction, installation process, and usage. Noteworthy functionalities such as Subdomain Enumeration and Banner Grabbing, In-depth Subdomain Enumeration, Port Scanning, and overall Reconnaissance capabilities were also explored.




