Google Hacking or Google Dorking
Searching the sensitive information hidden in clusters of publically-accessible information using advanced search terms called “dorks”. This technique is referred to as both “Google hacking” or “Google Dorking”. In this article, we will learn about manual Google and Github dorking and then automate the process of dorking using the Dor-king tool.
Dorking in Cyber Security
Dorking is very useful for pen-testers and security researchers when analyzing web application vulnerabilities. It also helps you dig deeper into the security analysis of your existing web security structure: loopholes, strengths, and even possible signs of attack.
List Of Most Basic Dorks Used:
Example:
- Allintext : Searches for occurrences of all the keywords provided.
Syntax: allintext:”keyword”
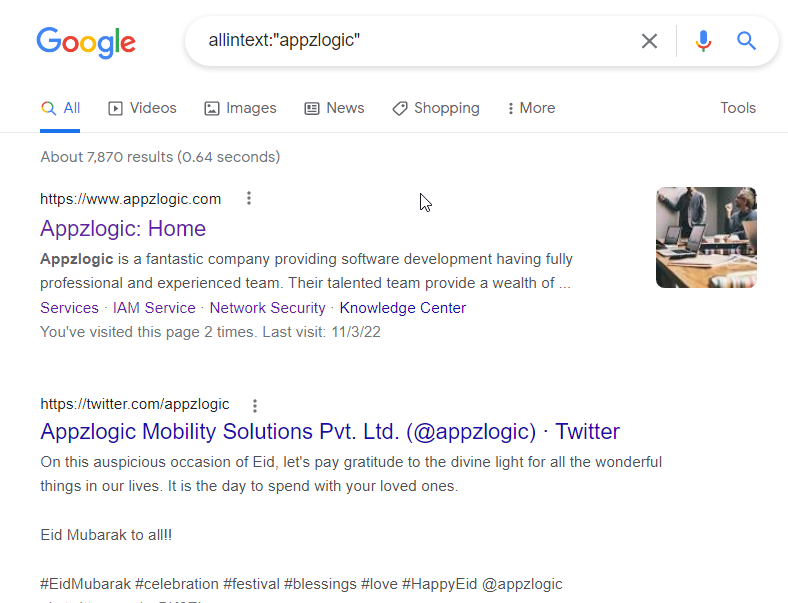
2. intext: The query intext:term limits the results to the documents containing keyword “term” in the text.
Syntax: intext:”keyword”
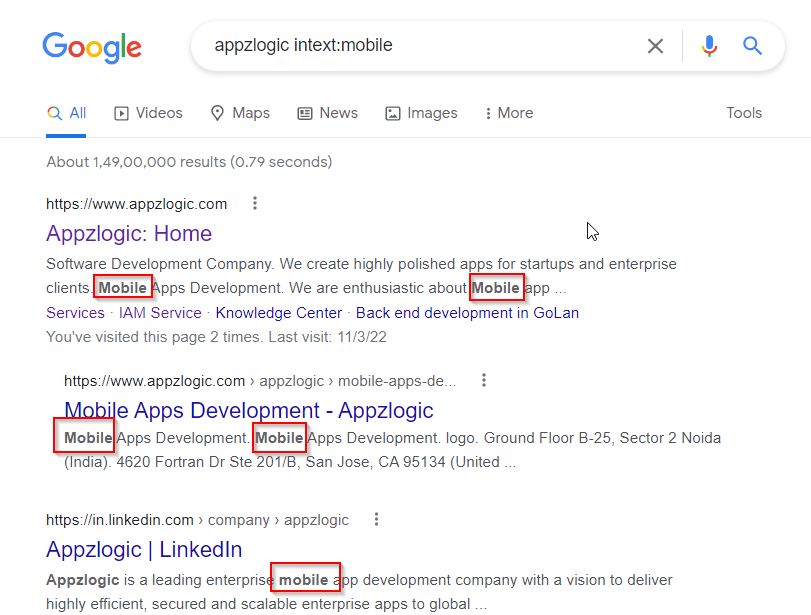
3. Inurl: Searches for a URL matching one of the keywords provided.
Syntax:inurl:”keyword”
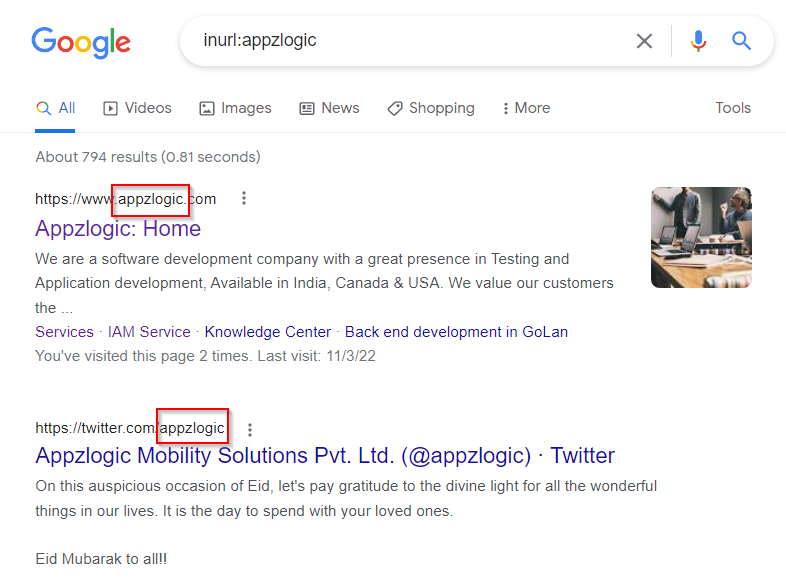
4. Allinurl: Searches for a URL matching all the keywords provided in the query.
Syntax: Allinurl:”keyword”
5. Intitle: It searches for occurrences of keywords in the title all or one.
Syntax:intitle:”keyword”
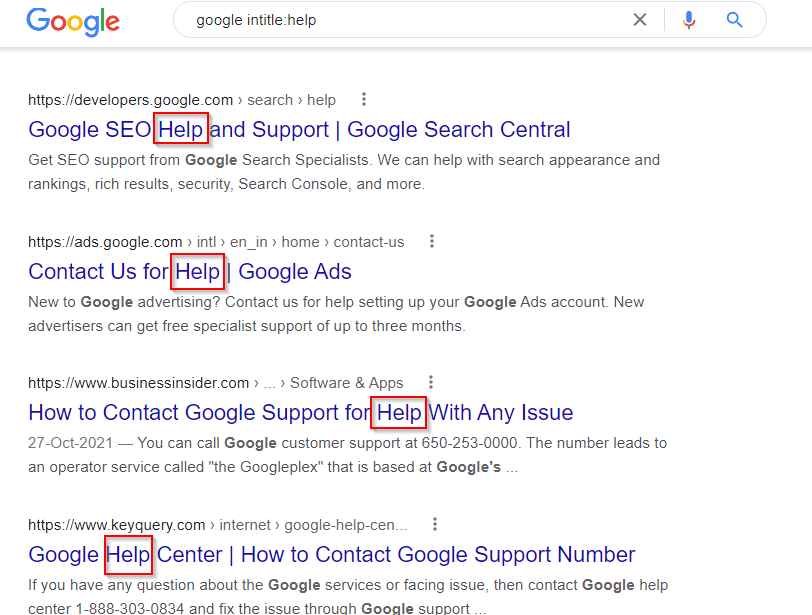
6. Allintitle: It searches for the occurrences of keywords all at a time.
Syntax:allintitle:”keyword”
7. Site: It specifically searches that particular site and lists all the results for that site.
Syntax:site:”www.google.com“
8. Filetype: It is used for Searching a particular filetype mentioned in the query.
Syntax:filetype:”pdf”
9. Link: It Searches for external links to pages.
Syntax link:”keyword” The query link URL shows pages that point to that URL
10. Numrange: It is used to locate specific numbers in your searches.
Syntax:numrange:10-100
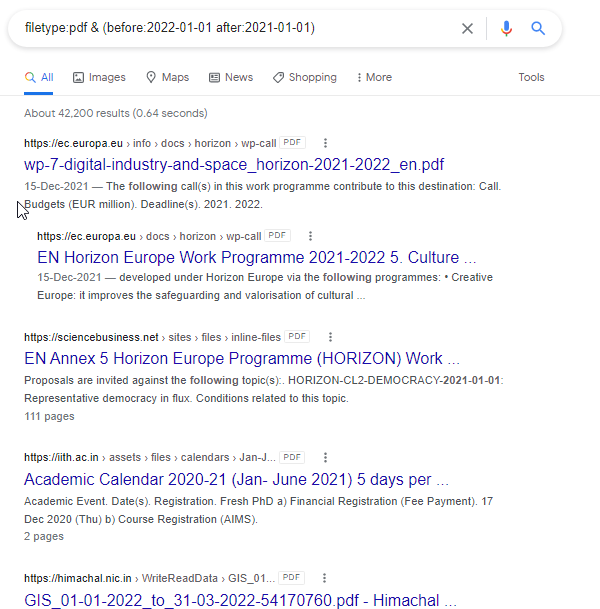
11. Before/after: It is used to search within a particular date range by providing a specific range.
Syntax:filetype:pdf & (before:2022-01-01 after:2021-01-01)
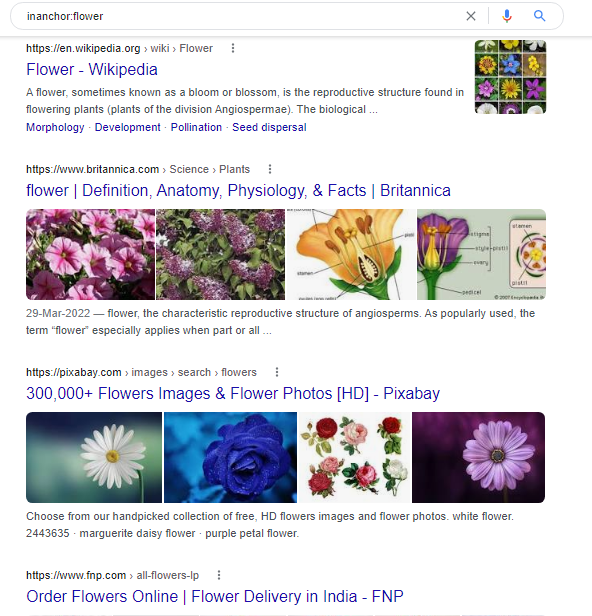
12. Allinanchor (and inanchor): This shows sites that have the key terms in links pointing to them, in order of the most links.
Syntax:inanchor:flower
13. allinpostauthor (and also inpostauthor): It is used in blog search, this one picks out blog posts that are written by a specific individual provided in the search query.
Syntax:allinpostauthor:”keyword”
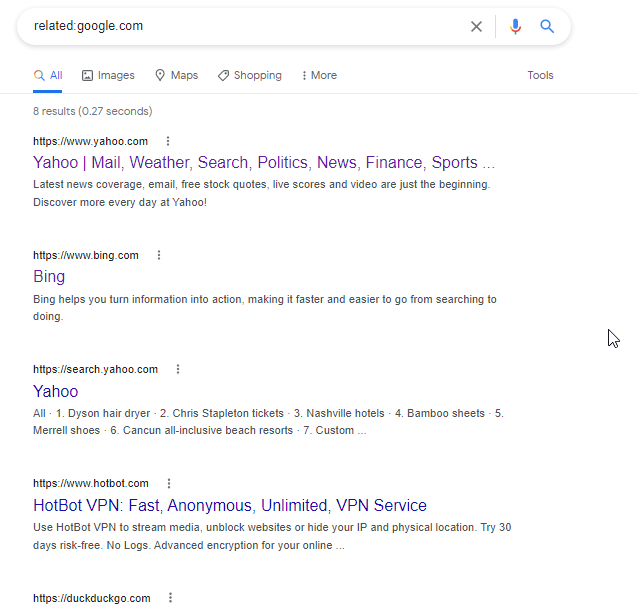
14. Related: It will list the web pages that are “similar” to a specified web page.
Syntax:related:www.google.com
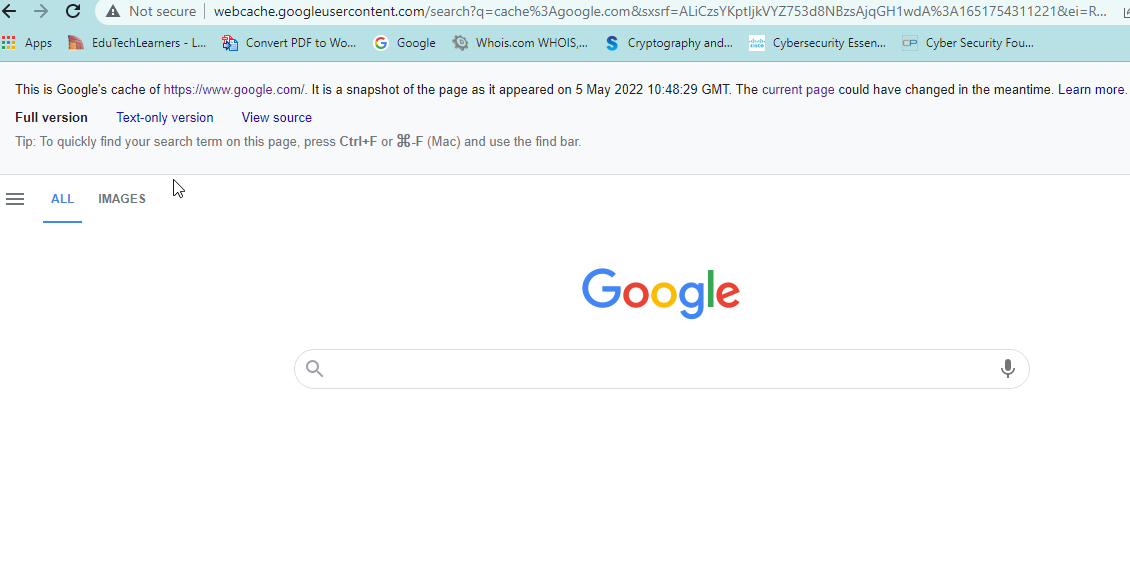
15. Cache: This shows the version of the web page that Google has in its cache.
Syntax:cache:www.google.com
Advance Google DORKS
- Directory listing vulnerabilities
Syntax : site:abcde.com intitle:index.of
2. Exposed Configuration files
Syntax: site:abcde.com ext:xml | ext:conf | ext:cnf | ext:reg | ext:inf | ext:rdp | ext:cfg | ext:txt | ext:ora | ext:ini
3. Exposed Database files
Syntax: site:abcde.com ext:sql | ext:dbf | ext:mdb
4. Find WordPress
Syntax: site:abcde.com inurl:wp- | inurl:wp-content | inurl:plugins | inurl:uploads | inurl:themes | inurl:download
5. Exposed log files
Syntax: site:abc.com ext:log
6. Backup and old files
Syntax: site:abcde.com+ext:bkf+|+ext:bkp+|+ext:bak+|+ext:old+|+ext:backup
7. Login pages
Syntax: site:abcde.com inurl:login
8. SQL errors
Syntax: site:abcde.com intext:”sql syntax near” | intext:”syntax error has occurred” | intext:”incorrect syntax near” | intext:”unexpected end of SQL command” | intext:”Warning: mysql_connect()” | intext:”Warning: mysql_query()” | intext:”Warning: pg_connect()”
9. Publicly exposed documents
Syntax: site:abcde.com ext:doc | ext:docx | ext:odt | ext:pdf | ext:rtf | ext:sxw | ext:psw | ext:ppt | ext:pptx | ext:pps | ext:csv
10. PHPinfo()
Syntax: site:abcde.com ext:php intitle:phpinfo “published by the PHP Group”
11. Finding Backdoors
Syntax: site:abcde.com inurl:shell | inurl:backdoor | inurl:wso | inurl:cmd | shadow | passwd | boot.ini | inurl:backdoor
12. Install / Setup files
Syntax: site:abcde.com inurl:readme | inurl:license | inurl:install | inurl:setup | inurl:config
13. Open Redirects
Syntax: site:abcde.com inurl:redir | inurl:url | inurl:redirect | inurl:return | inurl:src=http | inurl:r=http
14. Apache STRUTS RCE
Syntax: site:abcde.com ext:action | ext:struts | ext:do1
15. Find Pastebin entries
Syntax: site:pastebin.com abcde.com
16. Employees on LINKEDIN
Syntax: site:linkedin.com employees abcde.com
17. htaccess sensitive files
Syntax: site:abcde.com inurl:”/phpinfo.php” | inurl:”.htaccess” | inurl:”/.git” abcde.com -github.
18. Find Subdomains
Syntax: site:*.abcde.com
19. Find Sub-Subdomains
Syntax: site:*.*.abcde.com
20. Find WordPress
Syntax: site:abcde.com inurl:wp-content | inurl:wp-includes
You can find a list of popular dorks in the Exploit DB Dorks database. Google Dorking is an effective method to list out sensitive information from publicly accessible data.
Some useful tools for Google Dorking-
- Dor-king, Tool Link:https://github.com/mbappzlogic/Dor-king
- Dorks Eye, Tool Link: https://github.com/BullsEye0/dorks-eye
- Webdork, Tool Link: https://github.com/HACKE-RC/webdork
- Pagodo – Automate Google Hacking Database Scraping And Searching, Tool Link:https://github.com/opsdisk/pagodo
Defending against Google Dorking
- txt: Use the robots.txt file to avoid indexing of sensitive files, documents or folders.
- Consider removing your sensitive files from Google’s index.
- Encrypt your sensitive information (username, passwords, credit cards, emails, addresses, IP addresses, phone numbers, etc).
GitHub Dorking
In the same way that Google dorks can be used to scan websites for sensitive data, Scanning GitHub Repositories for Sensitive Data is known as GitHub Dorking.
Github Dorking is used to access sensitive data from public repositories, and because it’s a part of public sources, it can be included in any OSINT research.
You need a Github Account and analysis skills to perform Github Dorking. Things you’ll be looking for, such as database user and password, secret access keys, tokens, etc.
Before performing any recon, login into your account first. If you don’t have an account on GitHub you can register yourself using this https://github.com/ link.
List of a few random sensitive keywords such as:
- Username
- Api key
- password
- dbpassword
- dbuser
- access_key
- secret_access_key
- bucket_password
- redis_password
- Root_passwor
Let’s see some examples of GitHub Dorking-
- Search for specific credentials strings in configuration files such as –
filename:sftp-config.json password
Here, we obtained the IP address, root password and SSH port credentials.
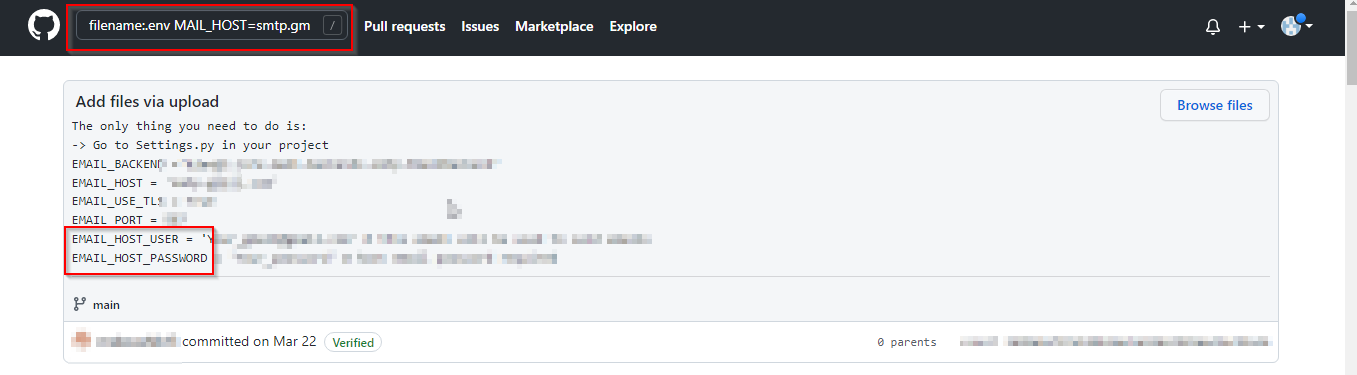
2. SMTP login credentials
Let’s search for smtp login credentials using search string like –
filename:.env MAIL_HOST=smtp.gmail.com
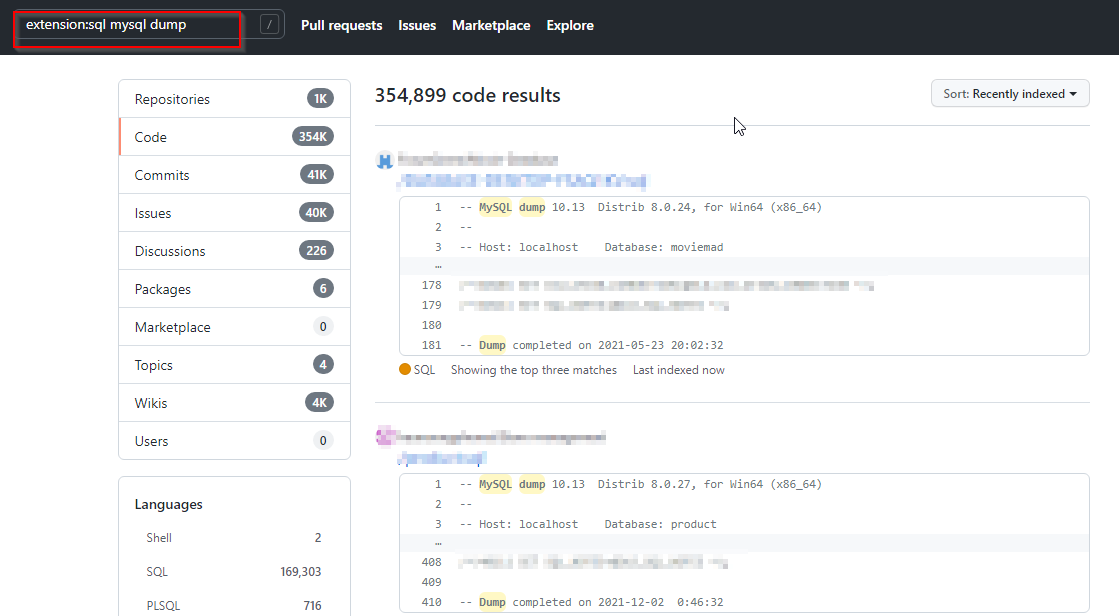
3. SQL dumps
Let’s search for SQL Dumps using the search query like-
extension:sql mysql dump
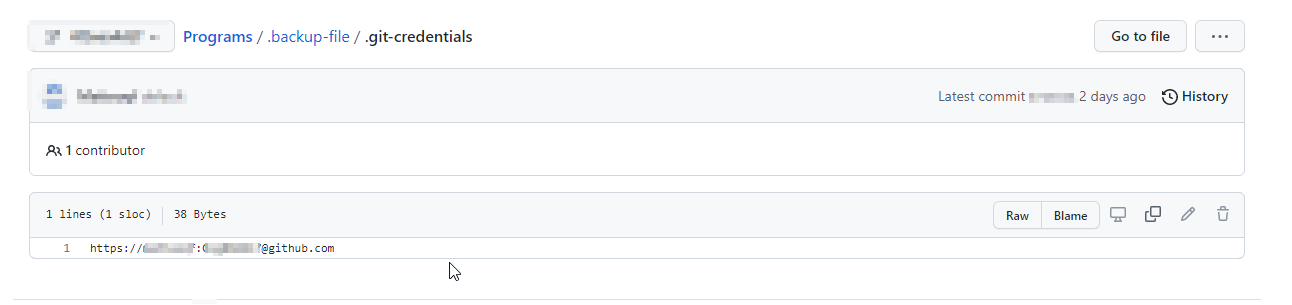
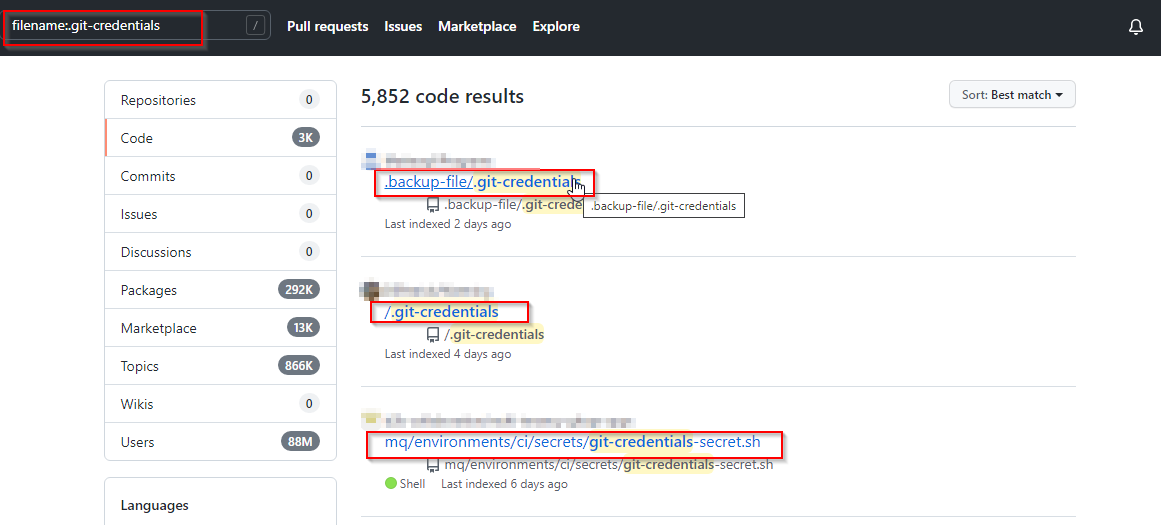
4. Git Credentials
Let’s Search for git credentials using –
filename:.git-credentials

If any organization lacks the proper configuration and sensitive information is publically available or configured to be publicly accessible then it may cause the organization to be vulnerable to cyber-attacks.
List of a few GitHub dorks which can be used to scan GitHub repositories:
- filename:.npmrc _auth
- filename:.dockercfg auth
- extension:pem private
- extension:ppk private
- filename:id_rsa or filename:id_dsa
- extension:sql mysql dump
- extension:sql mysql dump password
- filename:credentials aws_access_key_id
- filename:.s3cfg
- filename:wp-config.php
- filename:.htpasswd
- filename:.env DB_USERNAME NOT homestead
- filename:.env MAIL_HOST=smtp.gmail.com
- filename:.git-credentials
Some useful tools to perform GitHub Dorking-
- Dor-king, Tool Link:https://github.com/mbappzlogic/Dor-king
- Gitrob, Tool Link: https://github.com/michenriksen/gitrob
- Repo security scanner, Tool Link: https://github.com/techjacker/repo-security-scanner
- TruffleHog, Tool Link: https://github.com/trufflesecurity/trufflehog
Best Practices for GitHub security
- Managing two-factor authentication for your organization
- Viewing whether users in your organization have 2FA enabled
- Managing security settings for your organization
- Managing security and analysis settings for your organization
- Reviewing the audit log for your organization
- Reviewing your organization’s installed integrations
- When employees no longer work for your company, be sure to revoke all their access.
- Never allow your company developers to share GitHub credentials with anyone
Automating Google and Github Dorking using Dor-king Tool
This tool automates the process of searching for vulnerabilities using Google and GitHub dorks. It’s designed to make it easier for security researchers to find potential vulnerabilities in web applications.
This tool is used for finding sensitive information by automating the dorking process. This information may contain usernames and passwords, SQL queries, api keys, tokens, log files, configuration files, and many more. Dor-king also supports saving the results onto an HTML as well as JSON formatted file. This tool is an open source freely available tool on the GitHub platform.
Installation of Dor-king Tool on Kali Linux OS
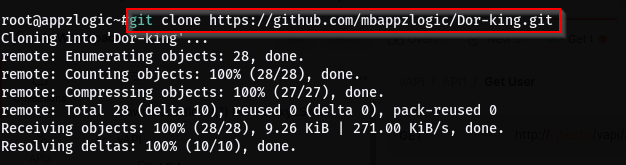
Step 1: Use the following command to install the tool.
Command: git clone https://github.com/mbappzlogic/Dor-king.git
Step 2: Navigate to the directory of the tool using the following command.
Command: cd Dor-king
Make the file executable by using the following command.
Command: chmod +x dorking.sh

After successfully installing the tool, let’s see how to use it.
Working With Dor-king Tool
Google Dorks
Usage: Finding information using Google Dorks. Run the tool and select the Google Dorks option.
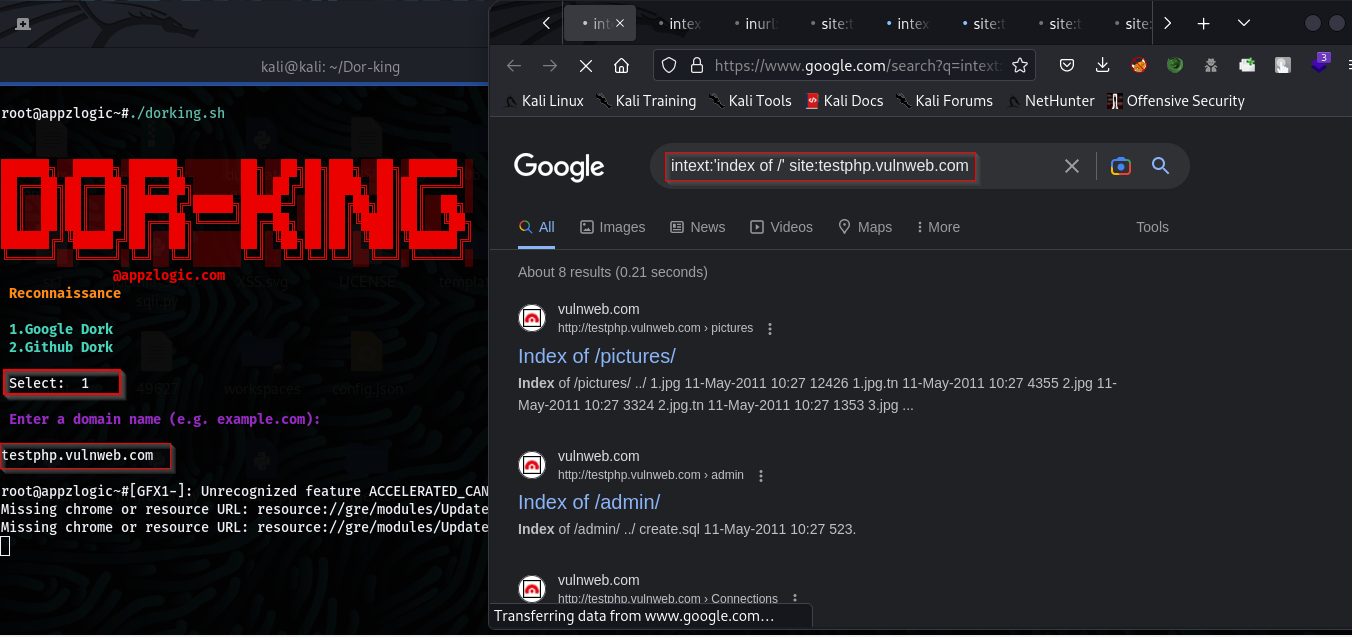
It will open the links of the target site with the dork query in the Firefox browser.
Github Dorks
Usage: Finding information using Github Dorks. Run the tool and select the GitHub Dorks option.
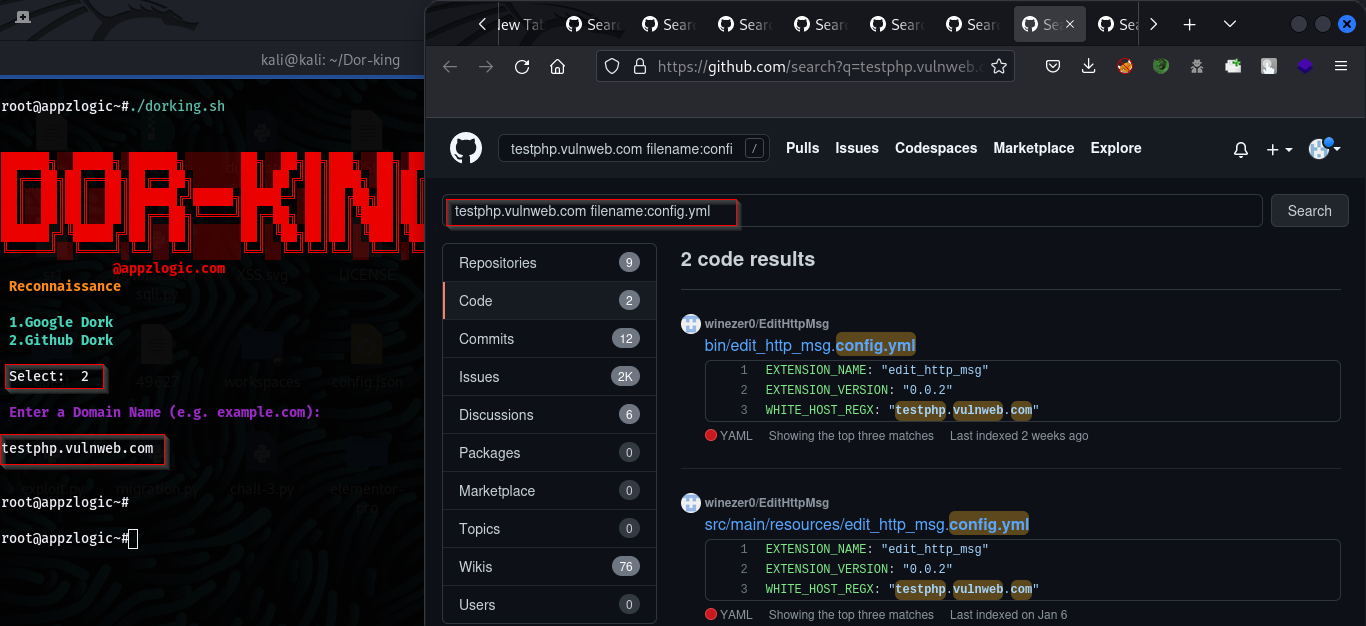
The script will automate the process of using the specified dork query and opens the link of the target site with a dork query in the Firefox browser.
References:
- Exploit Database: https://www.exploit-db.com/
- https://github.com/mbappzlogic/Dor-king
Talk To Our Security Expert
When you reach out to us, you are reaching out to our security team member who will understand your business and suggest the best service plan.
Get in Touch
Give us a call or drop by anytime; we endeavour to answer all inquiries within 24 hours, and for the career, please click here.
