In the technological age, there is a drastic increase in cyber attacks with no surprise that attacks are more sophisticated, and with the increasing dependence on electronic technology, protecting the services and data from cyber-attacks is a challenging issue.
Security testing is a procedure to determine that an information system protects data and maintains the intended functionality.
The primary purpose of security testing is to identify and mitigate vulnerabilities. Security testing deals with finding potential loopholes and identifying all possible security threats.
Importance of Security Testing
A security testing services assessment identifies and implements the security controls in applications. It also focuses on preventing and mitigating the count of vulnerabilities.
The Cost of an Information Breach
With the increasing growth in the number of applications, the sophistication and cost of security threats have also increased.

[The statics described here are based on IBM Security analysis of the research data compiled by the Ponemon Institute.]
The entirety of potential and identified cyber threats continues to grow in the volume of attacks that occur frequently and a variety of methods are introduced by cyber attackers.
The cost of a single data breach could cost a company millions of dollars along with a massive amount of downtime time to recover from the breach/attack.
- Risk Management
- Cost Reduction
- Reduced Downtime
- Regulatory Compliance and Laws
- Customer Trust
- Security of Information, Databases, and Servers.
Approach for Security Testing
White Box Testing
It is a type of Security testing approach, also known as “Clear Box Testing,” the tester has full knowledge and access to both the source code and software architecture of the Application.
Black Box Testing
It is a type of Security testing approach, there is no information given to the tester about the internal workings of the particular Application, nor about its source code or software architecture.
Grey Box Testing
It is a type of Security testing approach which combines the Black Box and the White Box Test. The Security tester only has partial knowledge of the internal workings of the Applications.
Principle of Security testing
The basic building block of Security requirements includes the elements of confidentiality, integrity, authentication, availability, authorization, and non-repudiation.
The three main components: confidentiality, integrity, and availability are referred to as the CIA triad.

- Confidentiality: Confidentiality deals with data and service protection against unintentional and unauthorized access. Confidentiality is a key component to preventing disclosure and data theft.
- Integrity: It is a mechanism that ensures the accuracy, completeness, consistency, and validity of an organization’s data.
- Authentication: Authentication is the mechanism of verifying the identity of a user or information.
- Availability: The component availability is to ensure that data and services are available to be used when it is needed by any user.
- Authorization: Authorization is a Security mechanism by which only an authorized user is permitted to use a resource or access any file.
- Non-repudiation: Non-repudiation is a method of guaranteeing message transmission between the sender and recipient via digital signature.
Security Testing Lifecycle
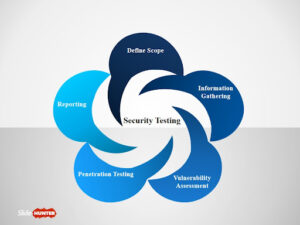
Security testing is a robust process of analyzing security-related weaknesses and flaws in software or application.
Its main objective is to find out how vulnerable a system may be and to determine whether its data, resources, and services are protected from potential cyber-attacks.
- Define Scope: The assets which should be tested during security testing to meet the organization’s objectives. It determines the rules of engagement for the assessment.
It is the First step for any Pen-test assessment, It also refers to the applications, networks, devices, or accounts that should be tested during security testing. - Information Gathering: Gathering any information relevant to the assessment goals and enumerating the attack surface.
It is a foundation step that deals with collecting publicly available information or internal information about the target. - Vulnerability Assessment: Identifying vulnerabilities and determining the risk associated. It is a mechanism for identifying, classifying, and prioritizing vulnerabilities.
Penetration Testing: Actively exploiting vulnerabilities identified. In the process of pen-test, simulated attacks are carried out to determine the weaknesses in a system. - Penetration Testing: Actively exploiting vulnerabilities identified. In the process of pen-test, simulated attacks are carried out to determine the weaknesses in a system.
- Reporting/Debriefing: It is a document that records the list of vulnerabilities found during a penetration test.
Tools for Security Testing
Here are some popular penetration testing tools used by security testers for detecting vulnerabilities and simulating cyber attacks. The tools used to defeat the clients’ defenses.
These are some of the same tools and techniques employed by malicious hackers.

Conclusion –
There are many enterprises that often take their cyber security testing services lightly and become victims of cyber attacks. Overlooking basic security measures can put the reputation at stake. The rising rate of cybercrime is never going to stop. As a business owner, you must take all the possible precautions to save your company’s and customers’ data, money, and most importantly reputation.




